Ox4Shell
Deobfuscate Log4Shell payloads with ease.
Since the release of the Log4Shell vulnerability (CVE-2021-44228), many tools were created to obfuscate Log4Shell payloads, making the lives of security engineers a nightmare.
This tool intends to unravel the true contents of obfuscated Log4Shell payloads.
For example, consider the following obfuscated payload:
After running Ox4Shell, it would transform into an intuitive and readable form:
This tool also aids to identify and decode base64 commands. After running Ox4Shell, the tool reveals the attacker’s intentions:
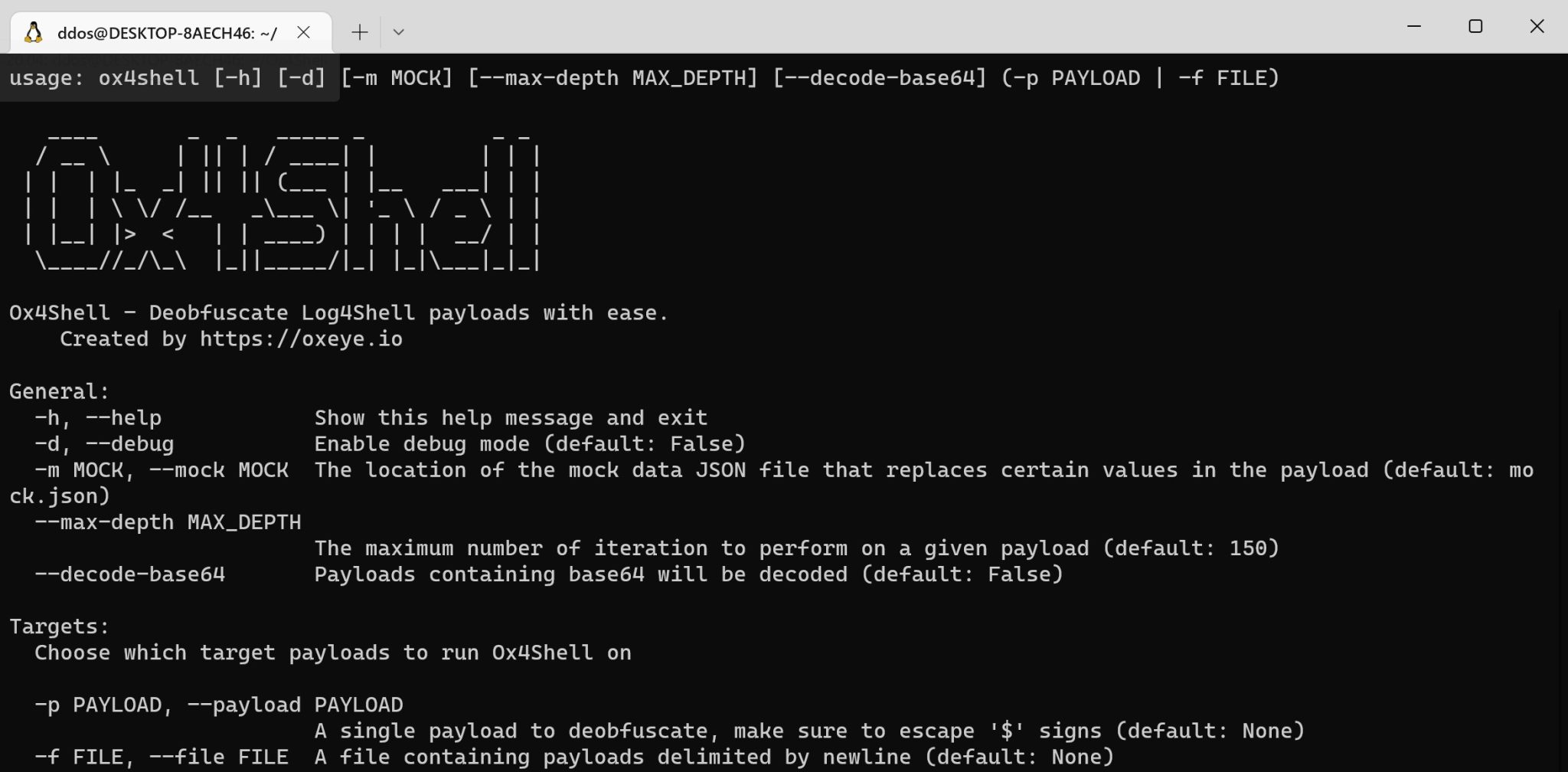
We recommend running Ox4Shell with a provided file (-f) rather than an inline payload (-p), because certain shell environments will escape important characters, therefore will yield inaccurate results.
Mock Data
The Log4j library has a few unique lookup functions, which allow users to look up environment variables, runtime information on the Java process, and so forth. This capability grants threat actors the ability to probe for specific information that can uniquely identify the compromised machine they targeted.
Ox4Shell uses the mock.json file to insert common values into certain lookup functions, for example, if the payload contains the value ${env:HOME}, we can replace it with a custom mock value.
The default set of mock data provided is:
As an example, we can deobfuscate the following payload using the Ox4Shell’s mocking capability:
Download
git clone https://github.com/ox-eye/Ox4Shell.git
Use
