Packet Strider: network packet forensics tool for SSH
Packet Strider
Packet Strider for SSH is a packet forensics tool that aims to provide valuable insight into the nature of SSH traffic, shining a light into the corners of SSH network traffic where golden nuggets of information previously lay in the dark.
The problem that packet strider aims to help with (AKA Why?)
SSH is obviously encrypted, yet valuable contextual information still exists within the network traffic that can go towards TTP’s, intent, success, and magnitude of actions on objectives. There may even exist situations where valuable context is not available or deleted from hosts, and so having an immutable and unalterable passive network capture gives additional forensic context. “Packets don’t lie”.
Separately to the forensic context, packet strider predictions could also be used in an active fashion, for example, to shun/RST forward connections if a tunneled reverse SSH session initiation feature is predicted within, even before reverse authentication is offered.
The broad techniques of packet strider (AKA How?)
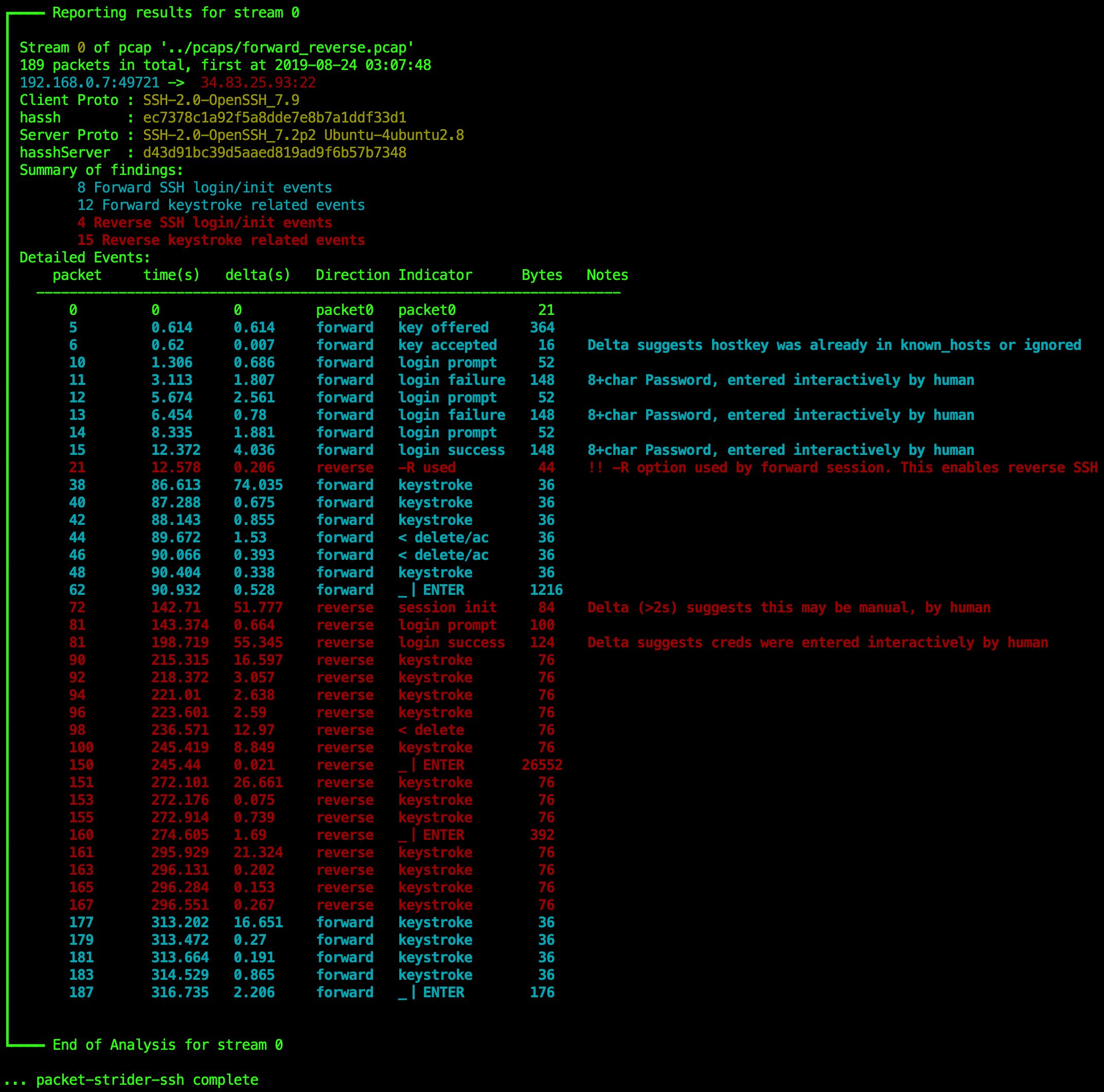
- Builds a rich feature set in the form of pandas dataframes. Over 40 features are engineered from packet metadata such as SSH Protocol message content, normalized statistics, direction, size, latency, and sliding window features.
- Strides through this feature set numerous times using sliding windows (Inspired by Convolutional Neural networks) to predict:
- The use -R option in the forward session – this is what enables a Reverse connection to be made later in the session. This artifact is discovered very early in the session, directly after the forward session is authenticated. This is the first available warning sign that Reverse sessions are possible.
- Initiation of the Reverse SSH session, this can occur at any point (early, or late) in the forward session. This is discovered prior to the Reverse session being authenticated successfully. This is the second warning sign, in that a reverse session has just been requested and set up for authentication.
- Success and/or Failure of the Reverse session authentication. This is the third and final warning sign, after this point, you know someone is on your host, inside a reverse session.
- The use of the -A option (SSH Agent Forwarding), which enables the client to share its local SSH private keys with the server. This functionality is generally considered dangerous. References: https://matrix.org/blog/2019/05/08/post-mortem-and-remediations-for-apr-11-security-incident https://skylightcyber.com/2019/09/26/all-your-cloud-are-belong-to-us-cve-2019-12491/ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2019-12491
- All predictions and metadata report on a stream by stream basis.
- Human or scripted, based on timing deltas.
- Is the server already known to the client? or was it the first time a connection between the two has been made? This is done through packet deltas associated with known_hosts.
- Whether a client certificate or password auth was used, and if the length of the password is 8 chars or less.
- keystrokes, delete keypress, enter keypresses (cut and paste and up/down is YMMV/experimental).
- exfil/infil data movement predictions in both Forward and Reverse sessions.
- Works on interactive sessions as well as file-based ssh file transfer apps (eg scp, putty, Cyberduck, etc).
Install & Use
Copyright (C) 2019 benjeems





