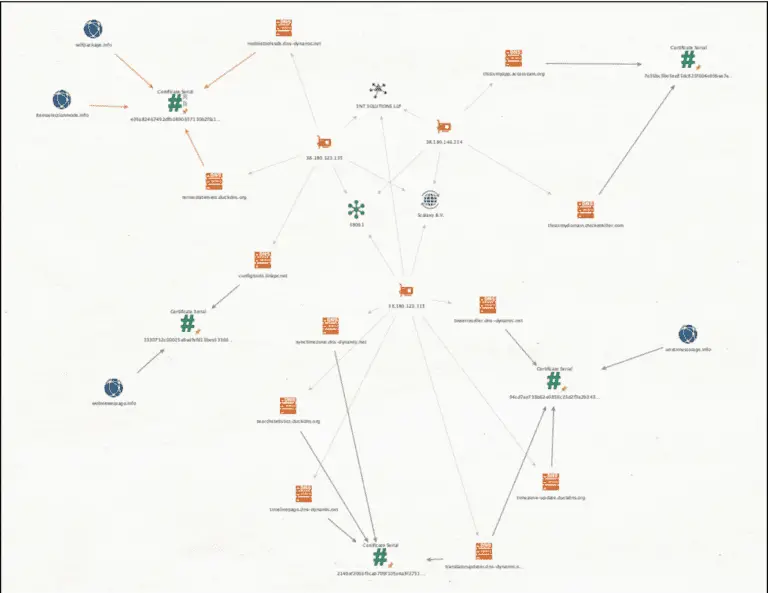
Researchers at ANY.RUN have identified a new campaign using Tycoon 2FA phish-kit. This time, attackers are targeting...
A critical vulnerability, identified as CVE-2024-41992, has been discovered in the Arcadyan FMIMG51AX000J model, and potentially other...
Mysterious codes that can cause system crashes frequently appear in the iOS system. Typically, these enigmatic codes...
SolarWinds has issued an urgent security advisory for its Web Help Desk (WHD) software, warning of a...
The browser extension Bypass Paywalls Clean (BPC), which allowed users to circumvent paywalls and access content on...
After over a decade of speculation, Microsoft has officially confirmed that the traditional Control Panel, a cornerstone...
A critical vulnerability in the popular data protection workflow management tool, Kanister, has been discovered, potentially allowing...
A recent report from Insikt Group has shed light on the covert operations of GreenCharlie, an Iran-backed...
Despite its discovery over two years ago, the Log4j vulnerability, known as Log4Shell (CVE-2021-44228), continues to pose...
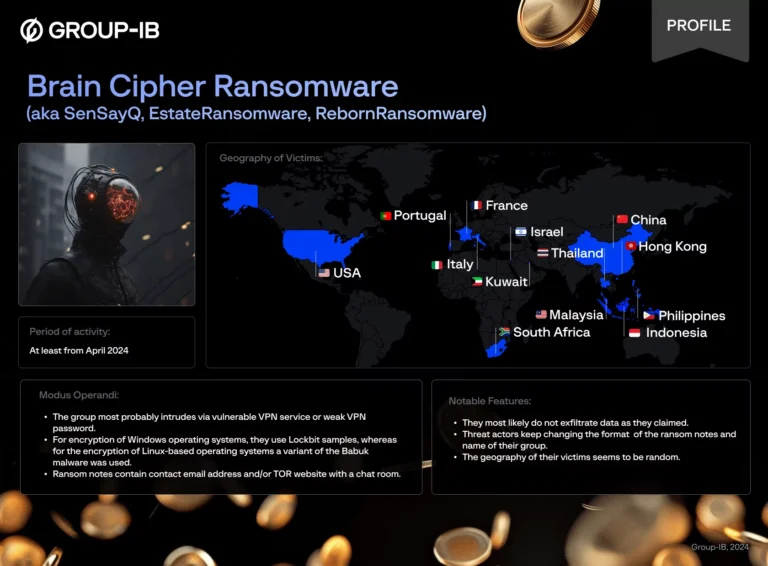
Indonesian government agencies have fallen victim to a large-scale cyberattack orchestrated by the Brain Cipher ransomware group....
Google has released an urgent Chrome update (version 128.0.6613.84/85) in response to an actively exploited zero-day vulnerability...
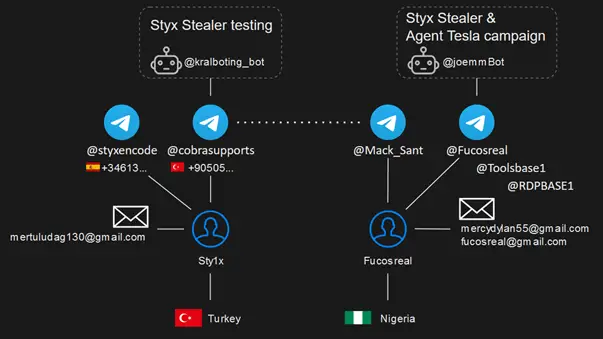
Recently, Check Point Research (CPR) discovered a new malware variant, Styx Stealer. Derived from the notorious Phemedrone...
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert, adding four critical security...
A critical security vulnerability (CVE-2024-28000, CVSS 9.8) in the widely-used Litespeed Cache plugin for WordPress has been...
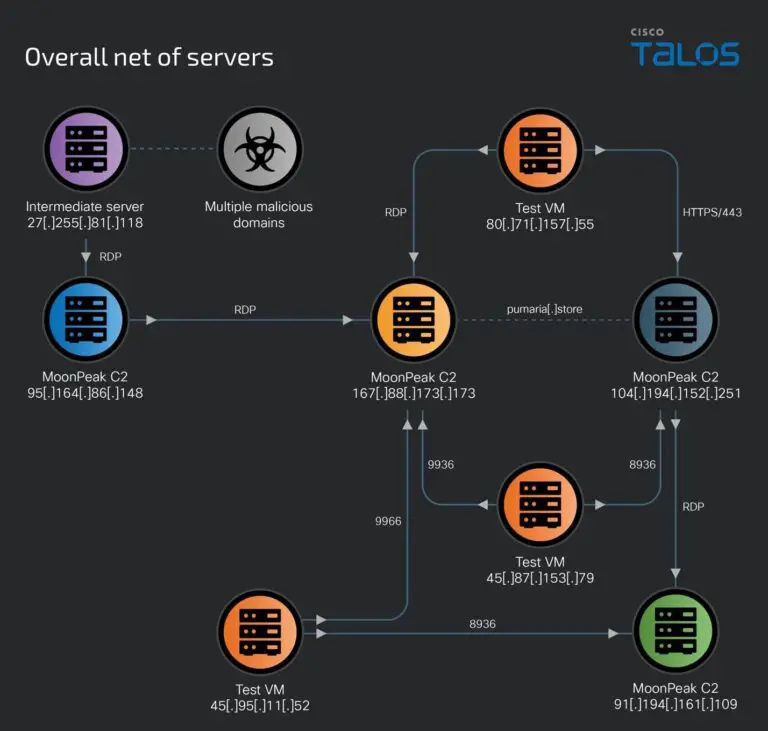
In a recent disclosure, cybersecurity researchers at Cisco Talos have uncovered a newly developed Remote Access Trojan...