IBM, Global Cyber Alliance, and Packet Clearing House partnered to launch the free Quad9 public DNS service (9.9.9.9) that will block domains associated with botnets,...
If you use virtual machines with Thin Provision disks (which are created with a minimum size and increase as they...
On the situation, you were forgotten/lost main user password in Linux, you can enter the single mode to...
Find hidden files dir command Displays a list of a directory’s files and subdirectories. If used without...
INTANG is research project for circumventing the “TCP reset attack” from the Great Firewall of China (GFW)...
OpenVPN road warrior installer for Debian, Ubuntu, and CentOS. VPN (Virtual Private Network), between the client and the host...
Xfce Xfce is a lightweight desktop environment for UNIX-like operating systems. It aims to be fast and...
The Shadow Simulator Shadow is a unique discrete-event network simulator that runs real applications like Tor and...
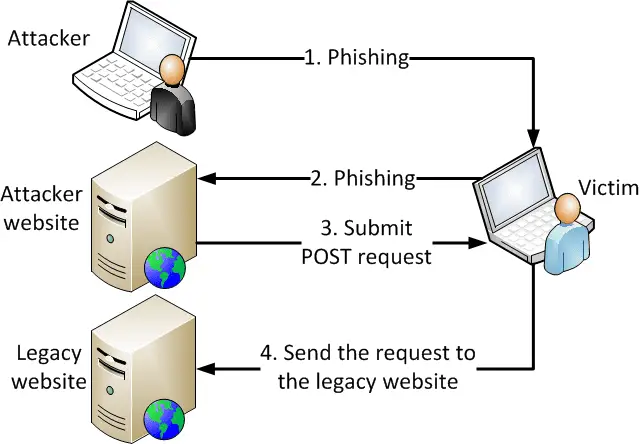
Understanding CSRF The Express team’s csrf and csurf modules frequently have issues popping up concerned about our usage of cryptographic functions....
Reverse proxy grapher This is a useful little tool that will generate a nice graphviz graph illustrating...
Since May this year, WannaCry extortion software in the global outbreak, there have been Equifax experienced large-scale...
Nmap Scripting Engine Search Description Nsearch is a tool that helps you to find scripts that are...
I am going to make a web crawler that will login to a school website using my...
Easily create and run hidden services Easily run a hidden service inside the Tor network with this...
clrinject Injects C# EXE or DLL Assembly into any CLR runtime and AppDomain of another process. The...