[BlackHat Tool] PAKURI v2.0 releases: Penetration test Achieve Knowledge Unite Rapid Interface
What’s PAKURI
Sometimes, penetration testers love to perform a complicated job. However, I always prefer the easy way. PAKURI is a semi-automated user-friendly penetration testing tool framework. You can run the popular pentest tools using only the numeric keypad, just like a game. It is also a good entry tool for beginners. They can use PAKURI to learn the flow to penetration testing without struggling with a confusing command line/tools.
Abilities of “PAKURI”.
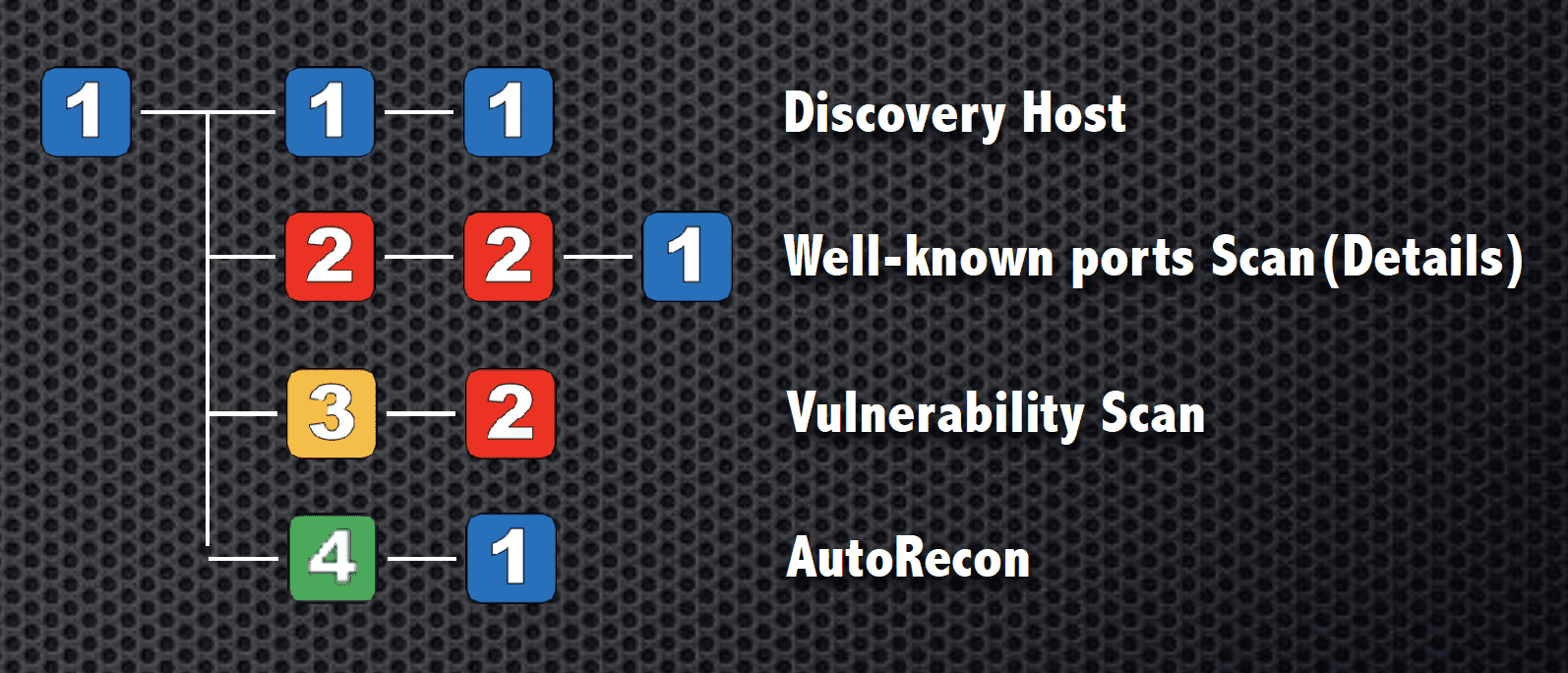
- Intelligence gathering.
- Vulnerability analysis.
- Visualize.
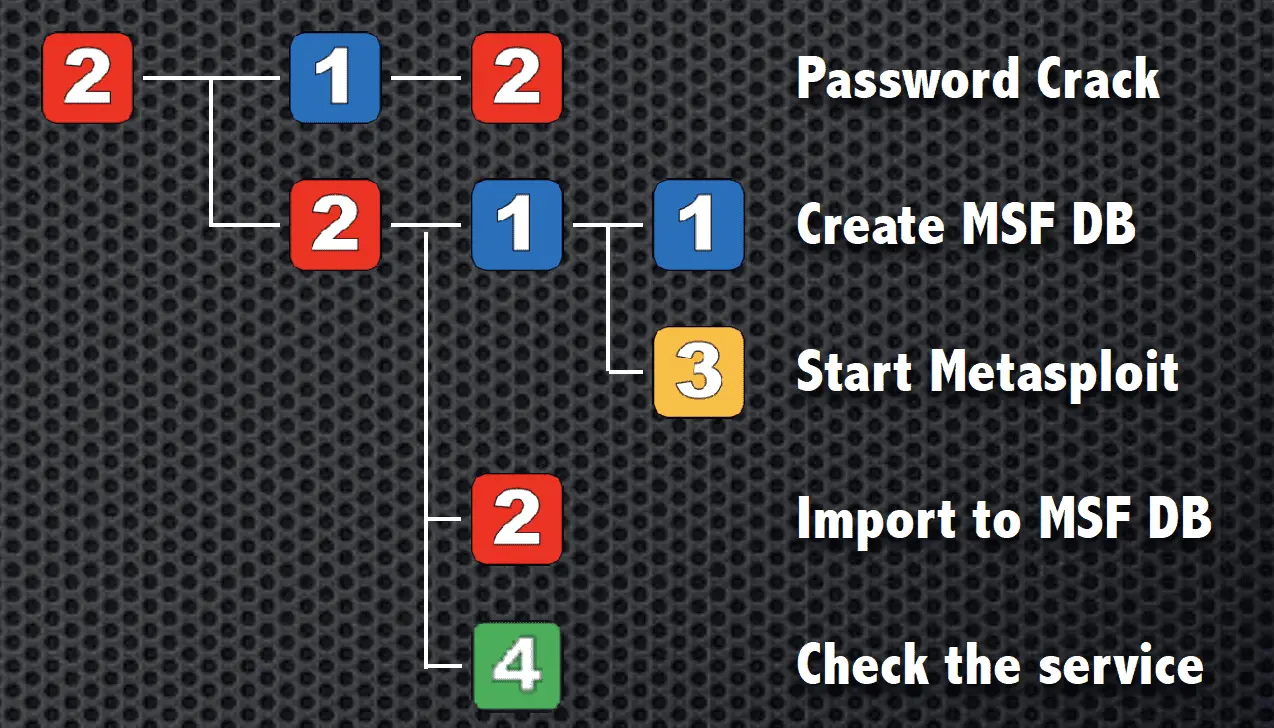
- Brute Force Attack.
- Exploitation.
Your benefits.
By using our PAKURI, you will benefit from the following.
For redteam:
(a) Red Teams can easily perform operations such as information enumeration and vulnerability scanning.
(b) Visualizing the survey results is possible only with the numeric keypad.
For blueteam:
(c) The Blue Team can experience a dummy attack by simply operating the numeric keypad even they do not have any penetration testing skill.
For beginner:
(d) PAKURI has been created to support the early stages of penetration testing. These can be achieved with what is included in Kali-Tools. It can be useful for training the entry level pentesters.
NOTE
If you are interested, please use them in an environment under your control and at your own risk. And, if you execute the PAKURI on systems that are not under your control, it may be considered an attack and you may have legal liability for your action.
Features
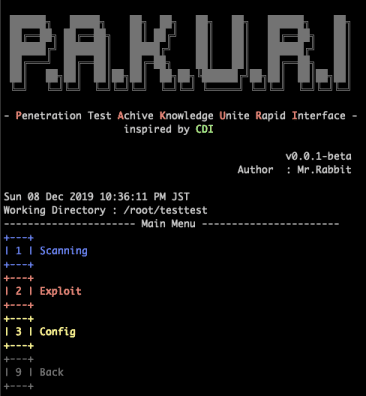
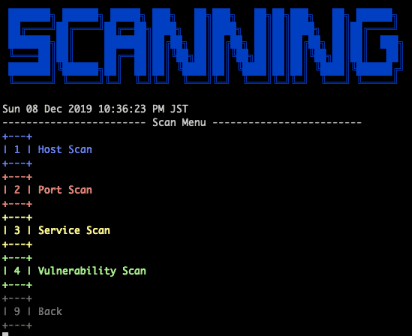
- Scan
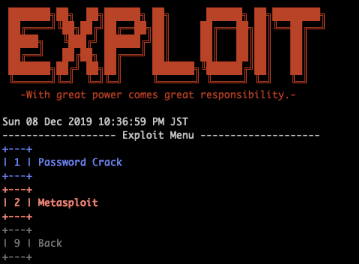
- Exploit
- Visualize
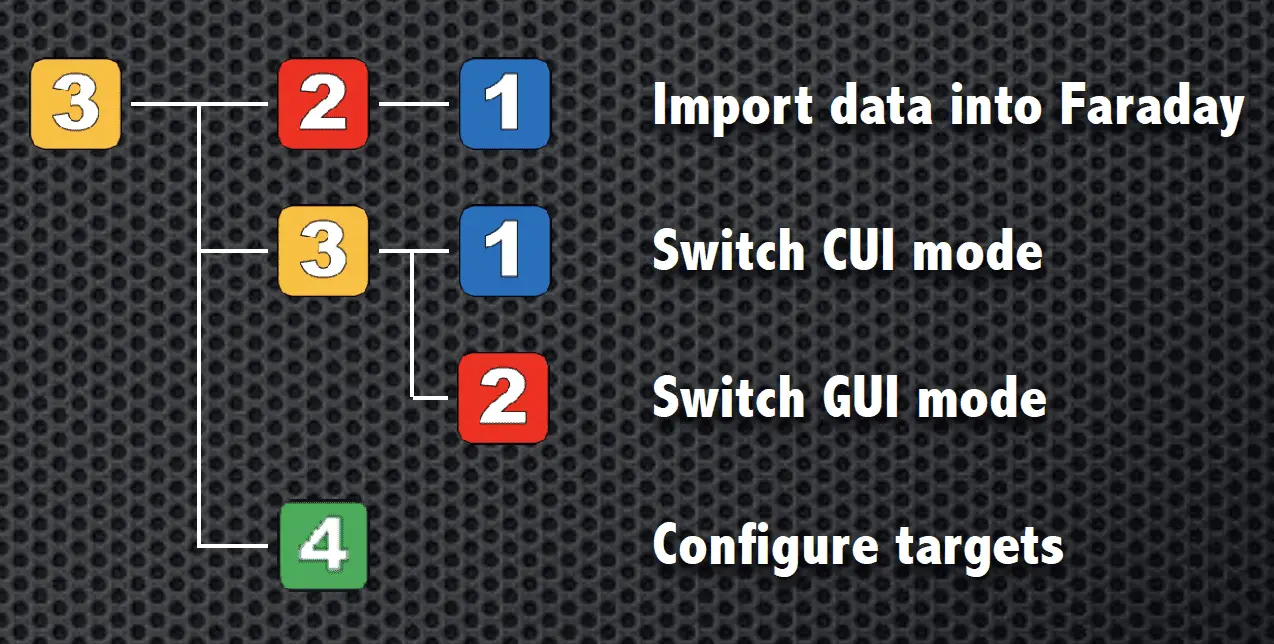
- CUI-GUI switching
- PAKURI can be operated with CUI and does not require a high-spec machine, so it can be operated with Raspberry Pi.
Scanning
Exploit
Config
By operating the numeric keypad, it is possible to scan the network, scan for vulnerabilities, and perform simple pseudo attacks.
Changelog v1.1.1
- This is PAKURI version 2, presented at BlackHat Asia 2020 Arsenal
Install
git clone https://github.com/01rabbit/PAKURI.git
cd PAKURI
./install.sh
Use
./pakuri.sh
Copyright (C) 2019 01rabbit
Source: https://github.com/01rabbit/