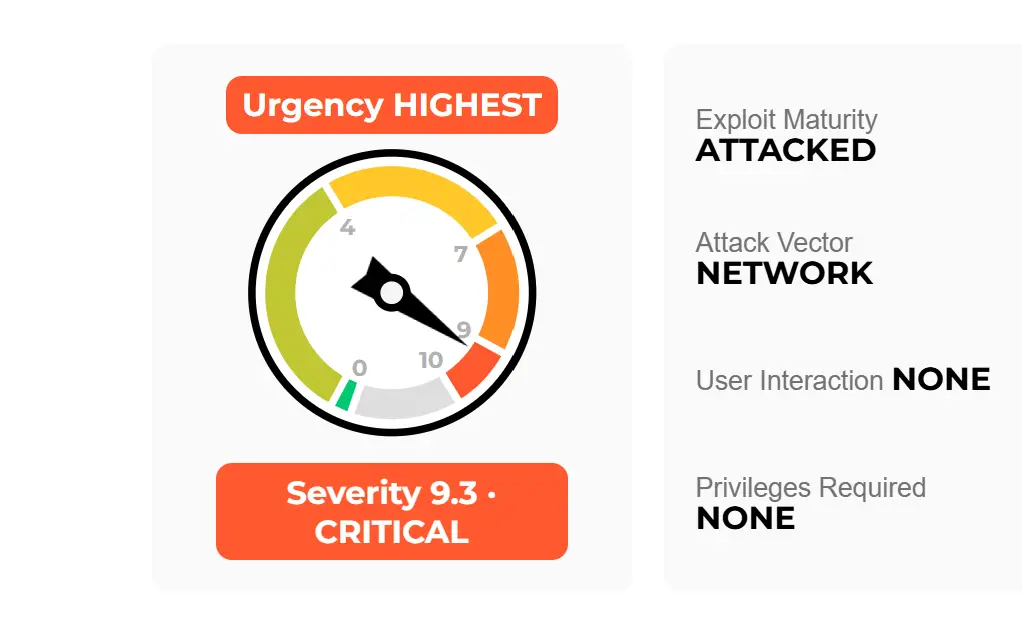
Today, Palo Alto Networks, a leading cybersecurity firm, has issued an urgent update to a recent security advisory, raising the severity level to “Critical” after observing active exploitation of a remote code execution vulnerability in their next-generation firewalls. The vulnerability, with a CVSS score of 9.3, affects the firewall management interfaces and could allow attackers to take complete control of vulnerable devices.
On November 8th, Palo Alto Networks initially warned customers about the vulnerability, urging them to restrict access to their firewall management interfaces. However, the situation escalated when the company detected malicious activity exploiting this flaw.
“Palo Alto Networks has observed threat activity exploiting an unauthenticated remote command execution vulnerability against a limited number of firewall management interfaces which are exposed to the Internet,” the updated advisory states. “We are actively investigating this activity.”
The company strongly emphasizes the importance of securing access to the management interface. “We recommend that you immediately ensure that access to the management interface is possible only from trusted internal IPs and not from the Internet,” the advisory urges. “The vast majority of firewalls already follow this Palo Alto Networks and industry best practice.”
For those who cannot immediately restrict access, Palo Alto Networks provides guidance on mitigating the risk: “If the management interface access is restricted to IPs the risk of exploitation is greatly limited, as any potential attack would first require privileged access to those IPs. CVSS for this scenario is 7.5 High.”
To help customers identify potentially vulnerable devices, Palo Alto Networks has implemented a tagging system within their Customer Support Portal. Devices with internet-facing management interfaces discovered during their scans are tagged with “PAN-SA-2024-0015.”
While securing access to the management interface is the immediate priority, Palo Alto Networks is actively working on a more permanent solution. “As we investigate the threat activity, we are preparing to release fixes and threat prevention signatures as early as possible,” the company assures.
Related Posts:
- Palo Alto Networks Investigates Potential Remote Code Execution Vulnerability in PAN-OS
- Fake Palo Alto Tool Delivers Sophisticated Malware in Middle East Cyberattack
- Palo Alto Networks’ Unit 42 Reveals a New Cyber Threat in China: Financial Fraud APKs
- A New Set of Tools for Cyber Espionage: Targeting the Middle East, Africa, and the US