Palo Alto Networks, a leading cybersecurity solutions provider, has recently released a critical security advisory, urging its customers to take immediate action to address several vulnerabilities discovered in their products. The vulnerabilities, if exploited, could allow unauthorized access, data breaches, and disruption of services.
The advisory highlights a range of vulnerabilities affecting various Palo Alto Networks products, including PAN-OS, GlobalProtect, Cortex XDR, and others. The severity of these vulnerabilities varies, with some classified as critical, posing a significant risk to organizations’ security posture.
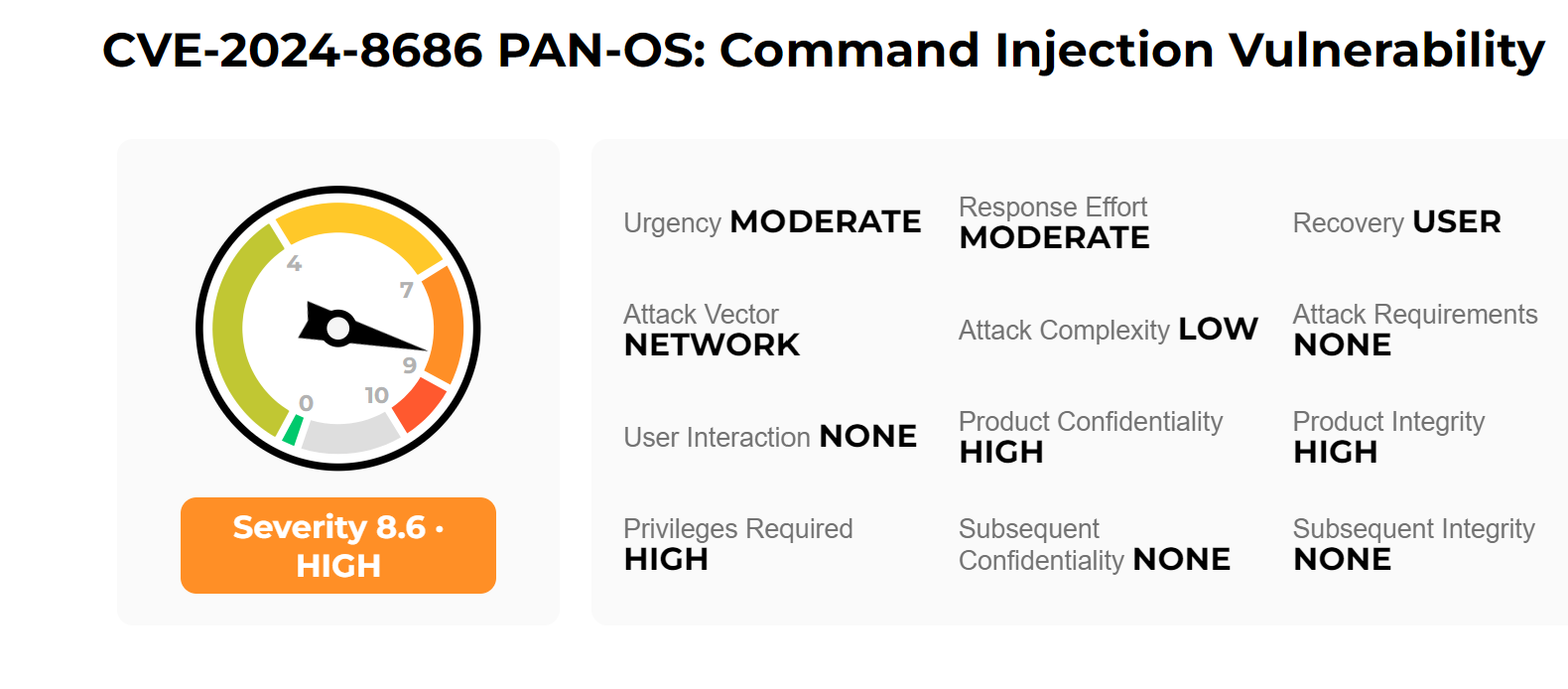
Here’s a closer look at the two most significant issues, CVE-2024-8686 and CVE-2024-8687.
- CVE-2024-8686: Command Injection Vulnerability in PAN-OS (CVSS 8.6)
One of the most critical vulnerabilities, identified as CVE-2024-8686, affects PAN-OS and could enable an authenticated administrator to bypass system restrictions and execute arbitrary commands as root on the firewall. This vulnerability could allow an attacker to gain complete control over the affected system, potentially leading to a devastating compromise.
Affected Versions:
- PAN-OS 11.2: Versions prior to 11.2.3 are affected.
- Cloud NGFW: Not affected.
- Prisma Access: Not affected.
To mitigate this vulnerability, administrators are urged to upgrade to PAN-OS 11.2.3 or later versions.
- CVE-2024-8687: GlobalProtect Cleartext Exposure (CVSS 6.9)
Another significant vulnerability, CVE-2024-8687, impacts PAN-OS and GlobalProtect and could expose sensitive information, such as GlobalProtect uninstall passwords and disable or disconnect passcodes. This vulnerability could enable end-users to bypass security measures and uninstall, disable, or disconnect GlobalProtect, even if their configuration doesn’t permit them to do so.
Affected Versions:
- GlobalProtect App 6.3: Not affected.
- Versions prior to 6.2.1, 6.1.2, 6.0.7, 5.2.13, and 5.1.12 are vulnerable.
Users are advised to update to the latest versions of GlobalProtect to prevent exploitation.
Mitigation and Recommendations
The advisory also addresses other vulnerabilities, including cleartext exposure of credentials, arbitrary file read vulnerabilities, and user impersonation issues. These vulnerabilities, while not as critical as the aforementioned ones, still pose a significant risk to organizations’ security and should be addressed promptly.
Palo Alto Networks has released patches and updates to mitigate these vulnerabilities and strongly recommends that customers apply them immediately. The company also provides detailed instructions and workarounds for those who cannot immediately apply the patches.
Organizations that rely on Palo Alto Networks products are urged to take this advisory seriously and prioritize patching their systems. The potential consequences of failing to address these vulnerabilities could be severe, including data breaches, financial losses, and reputational damage.
In addition to patching, organizations should also implement other security best practices, such as regular backups, strong password policies, and multi-factor authentication. These measures can help to minimize the risk of a successful attack, even if a vulnerability is exploited.
For a detailed breakdown of affected versions and patch instructions, see the official advisory from Palo Alto Networks [1,2,3,4,5,6].
Related Posts:
- Fake Palo Alto Tool Delivers Sophisticated Malware in Middle East Cyberattack
- Palo Alto Networks Issues Security Advisories, Urges Updates Amidst 34 Vulnerabilities
- PAN-OS: PAN-OS Remote Code Execution Vulnerability
- WikiLoader Malware Evolves with SEO Poisoning, Targets GlobalProtect Users
- PAN-OS arbitrary code execution vulnerability