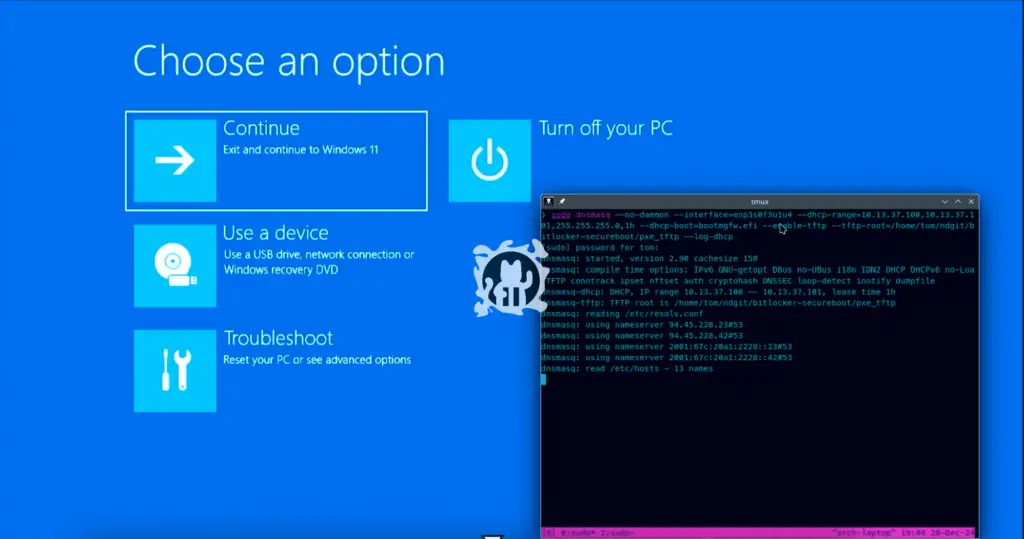
A revelation emerged from the Chaos Communication Congress (CCC) last week, shaking the foundations of Windows’ trusted BitLocker encryption. Security researcher Thomas Lambertz, in his presentation “Windows BitLocker: Screwed without a Screwdriver,” exposed a glaring vulnerability that allows attackers to bypass BitLocker encryption and access sensitive data, even on systems supposedly patched against the flaw.
The vulnerability, dubbed “bitpixie” (CVE-2023-21563), was initially addressed by Microsoft in November 2022. However, Lambertz demonstrated how attackers can exploit an outdated Windows bootloader via Secure Boot to extract encryption keys. This attack requires only momentary physical access to the device and a network connection – no screwdrivers or hardware hacking necessary.
The root cause lies in the limited storage for certificates within UEFI, a critical component in the boot process. New Secure Boot certificates are not expected to be available before 2026. As interim measures, Lambertz advises users to set custom PINs for BitLocker or disable network access through the BIOS. However, even a basic networked USB device could potentially facilitate the attack.
While the average user might not be a primary target, the implications for corporate, government, and other high-security environments are significant. The ability to completely decrypt a device with just brief physical access raises serious concerns about data protection.
For those wishing to explore the topic further, a full recording of Lambertz’s 56-minute presentation is available on the CCC media center website. It delves into the technical intricacies and explains why resolving this vulnerability presents such a formidable challenge.
Related Posts:
- Critical Microsoft Access Vulnerability Exploited for NTLM Token Theft
- Microsoft will focus on building AI and cloud platforms in the future instead of Windows
- Google is strengthening Android security and encourages vendors to strongly encrypt devices