PEASS – Privilege Escalation Awesome Scripts SUITE v202304132 releases
Here you will find privilege escalation tools for Windows and Linux/Unix* (in some near future also for Mac).
These tools search for possible local privilege escalation paths that you could exploit and print them to you with nice colors so you can recognize the misconfigurations easily.
- Check the Local Windows Privilege Escalation checklist from book.hacktricks.xyz
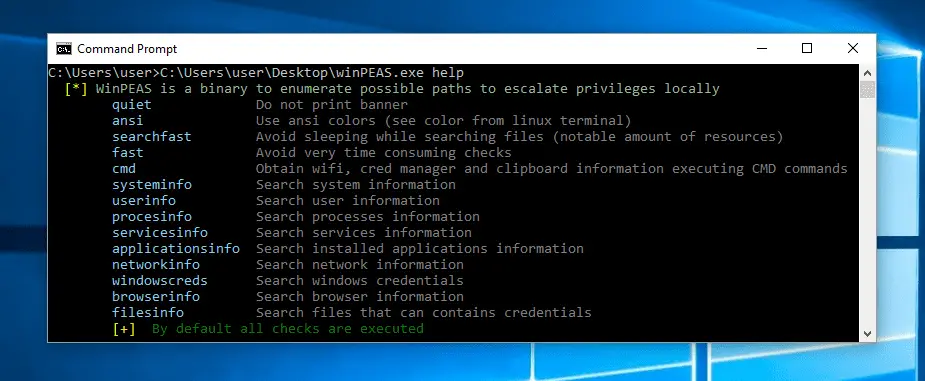
- WinPEAS – Windows local Privilege Escalation Awesome Script (C#.exe and .bat)
The goal of this project is to search for possible Privilege Escalation Paths in Windows environments.It should take only a few seconds to execute almost all the checks and some minutes searching in the whole main drive for known files that could contain passwords (the time depends on the number of files in your drive). Get rid of that time-consuming check using the parameter fast.By default, the program sleeps 150ms before start searching files in each directory. This is made to consume fewer resources (stealthier). You can avoid this sleep using searchfast parameter.The ouput will be colored. Below you have some indications about what does each color means exactly, but keep in mind that Red is for something interesting (from a pentester perspective) and Green is something good (from a defender perspective).The tool is heavily based in SeatBelt.IMPORTANT TO NOTICE: By default, WinPEAS will use colors for Windows terminals (without ANSI characters). If you are executing winpeas.exe from a reverse shell without any option any color will appear. To see colors in a Linux terminal you need to use the ANSI parameter.
- Check the Local Linux Privilege Escalation checklist from book.hacktricks.xyz
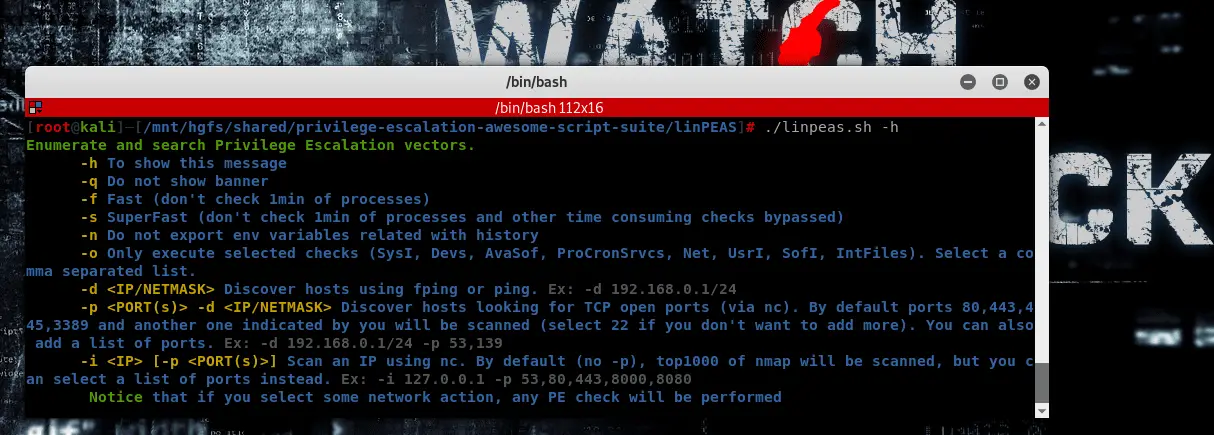
- LinPEAS – Linux local Privilege Escalation Awesome Script (.sh)LinPEAS is a script that searches for possible paths to escalate privileges on Linux/Unix* hosts. The checks are explained on book.hacktricks.xyzCheck the Local Linux Privilege Escalation checklist from book.hacktricks.xyz.The goal of this script is to search for possible Privilege Escalation Paths (tested in Debian, CentOS, FreeBSD, and OpenBSD).This script doesn’t have any dependency.It uses /bin/sh syntax, so it can run in anything supporting sh (and the binaries and parameters used).It could take from 2 to 3 minutes to execute the whole script (less than 1 min to make almost all the checks, almost 1 min to search for possible passwords inside all the accessible files of the system and 1 min to monitor the processes in order to find very frequent cron jobs).You can decrease this time use the parameters:
- -f (fast) – This will bypass checking processes during 1 min
- -s (superfast) – This will bypass the previous check and other time-consuming checks.
This script has several lists included inside of it to be able to color the results in order to highlight the PE vector.
LinPEAS also exports a new PATH variable if common folders aren’t present in the original PATH variable. It also exports unset and export several environmental commands so no command executed during the session will be saved in the history file (you can avoid these actions using the parameter -n).
 Hosts Discovery and Port Scanning
Hosts Discovery and Port ScanningWith LinPEAS you can also discover hosts automatically using fping, ping and/or nc, and scan ports using nc.
LinPEAS will automatically search for these binaries in $PATH and let you know if any of them are available. In that case, you can use LinPEAS to hosts discovery and/or port scanning.
Download
peass-ng is (C) 2006-2022 Carlos Polop Martin.
Source: https://github.com/carlospolop/