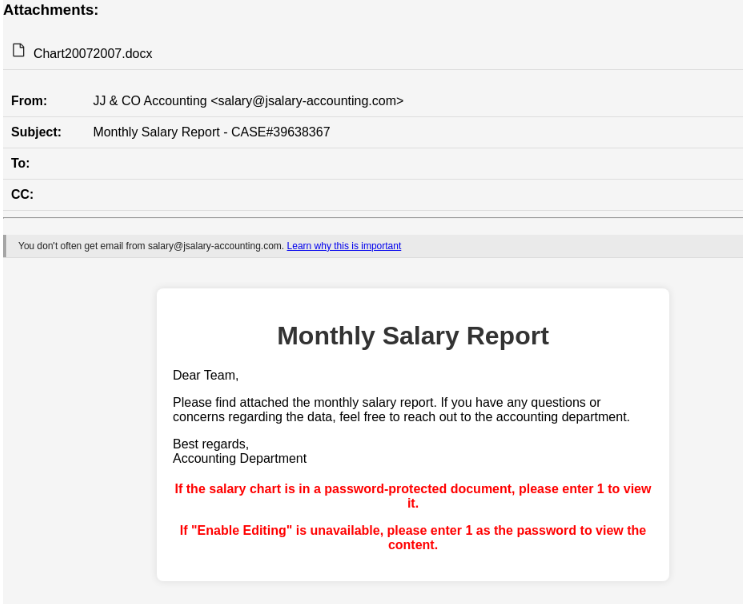
Targets are prompted to enter the password “1” and to click “Enable Editing”
A sophisticated new malware campaign dubbed “PhantomBlu” is on the prowl, preying on US-based organizations with a potent combination of evasive techniques and the notorious NetSupport RAT (Remote Access Trojan). Security researchers at Perception Point have uncovered this insidious threat, revealing its cunning strategies for bypassing detection and gaining control of targeted systems.
The RAT Evolves
PhantomBlu breaks the mold, showcasing how legitimate remote administration tools like NetSupport Manager can be twisted into potent cyberweapons. NetSupport RAT, already a formidable threat, now boasts a new level of stealth. This campaign leverages a technique called OLE template manipulation, where malicious code is hidden within seemingly harmless Microsoft Office documents. This advanced technique involves hiding the malicious payload outside of the document, which only executes upon user interaction, marking a novel approach in the deployment of NetSupport RAT.
The Phishing Lure

PhantomBlu targets unsuspecting employees with carefully crafted phishing emails posing as salary reports from an accounting service. Victims are tricked into downloading password-protected Word documents and following detailed instructions. This social engineering lures them into clicking a deceptively disguised image, triggering a complex chain of exploitation.
Unveiling the PhantomBlu Infection
Perception Point’s analysis reveals how the PhantomBlu attackers:
- Abuse Legitimate Services: Utilize mass-mailing platforms like SendInBlue to lend credibility to the phishing emails.
- Manipulate Documents: Embed malicious OLE packages within Word documents to sneak past traditional security checks.
- Deploy Layers of Obfuscation and Establish RAT Persistence: Perception Point’s analysis exposed a PowerShell dropper concealed within a .LNK file, designed to fetch and execute a script from a specified URL. The script, obfuscated to obscure its malicious purpose, serves as a master key to unleashing the NetSupport RAT, ensuring its persistence through a registry key for AutoStart. In accessing and analyzing the secondary payload, Perception Point mirrored the attackers’ methods to unveil the command and control (C2) servers integral to PhantomBlu’s operations, illustrating the campaign’s reliance on sophisticated communication and operational directives.
PhantomBlu’s use of encrypted .docs via OLE template manipulation and Template Injection (T1221) represents a departure from traditional NetSupport RAT deployments, which have typically relied on executable files and simpler phishing tactics. This innovation underscores PhantomBlu’s blend of sophisticated evasion techniques with social engineering.
Perception Point’s proprietary anti-evasion model, the “Recursive Unpacker,” played a pivotal role in dissecting the multi-layered obfuscation and evasion techniques wielded by PhantomBlu. From the initial email to the extraction of the concealed LNK file, this tool underscores the importance of advanced defensive strategies in the face of evolving cyber threats.
The Threat of RAT-Based Attacks
Once NetSupport RAT infests a system, it allows attackers to:
- Monitor and Record Activities: Log keystrokes, capture screenshots, and steal sensitive data.
- Control the System: Execute commands, install further malware, and move laterally within the network.
- Exfiltrate Information: Transfer stolen data to attacker-controlled servers.
The Takeaway
The PhantomBlu campaign underscores the ever-evolving nature of cyberthreats. Attackers are constantly refining their tactics, requiring organizations to remain vigilant and proactive in their defenses.