PHP malware scanner
Traversing directories for files with php extensions and testing files against text or regexp rules, the rules-based on self-gathered samples and publicly available malwares/webshells. The goal is to find infected files and fight against kiddies, because too easy to bypass rules.
Changelog v1.0.26
-
Sample update
Download
git clone https://github.com/scr34m/php-malware-scanner.git
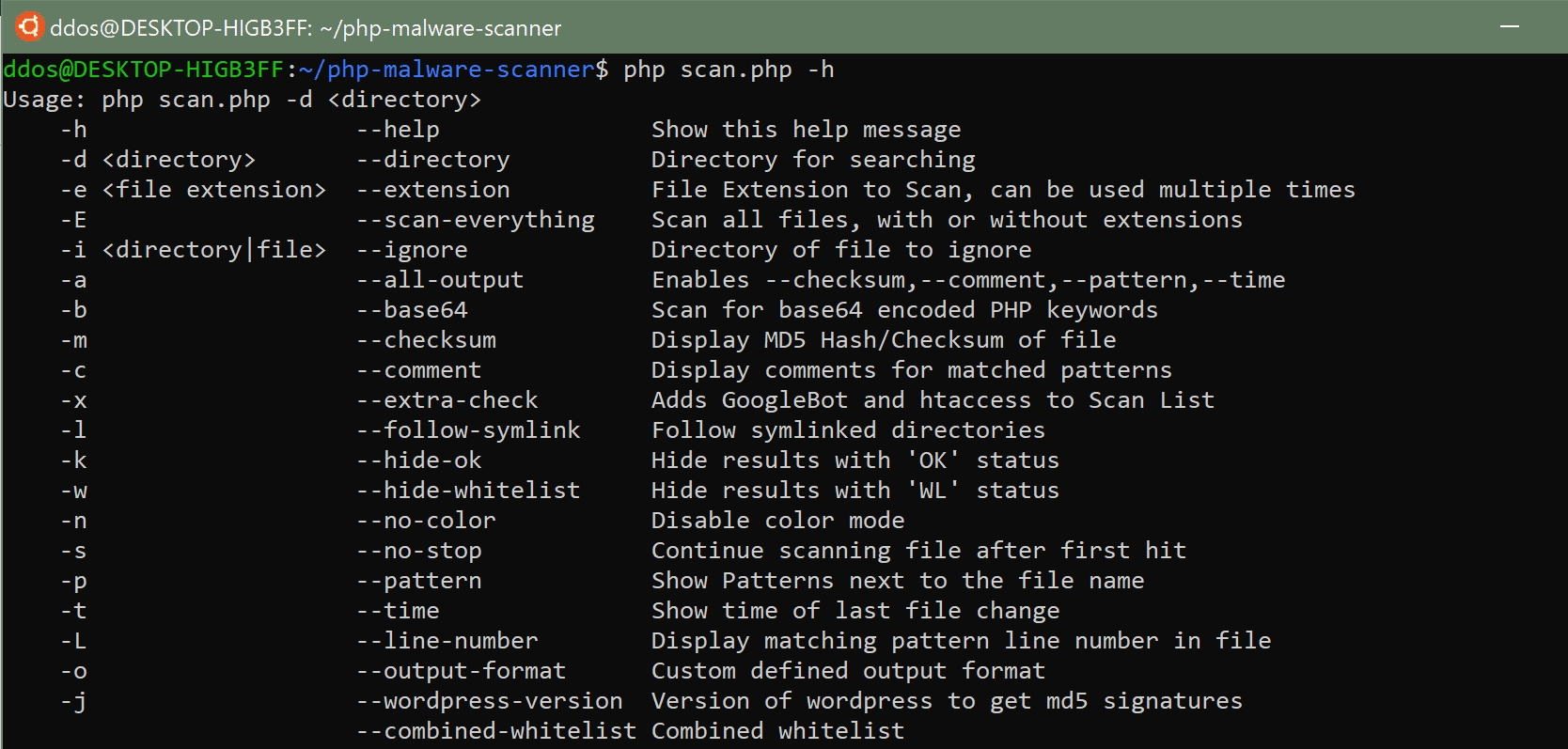
Use

Ignore argument could be used multiple times and accept glob-style matching ex.: “cache*”, “??-cache.php” or “/cache” etc.
Extension argument defaults to “.php” and also can be used multiple times too.
--base64is an alternative scan mode which ignores the main pattern files and uses a large list of php keywords and functions that have been converted to base64. Slower and prone to false positives, but gives additional base64 scanning coverage. These pattern files are located in base64_patterns and were derived from php 7 keywords and functions. Not many PHP extensions are included.--commentflag will display the last comment to appear in the pattern file before the matched pattern, so documenting the pattern files is important.
Output formatting
Default output depending on the specified parameters, but the full format is “%S %T %M # {%F} %C %P # %L” and using ANSI coloring too.
Possible variables are:
%S– matching indicator, possible values are OK, ER, WL%T– file change time%M– file md5 hash value%F– file with path%P– pattern%C– pattern comment%L– matching pattern line number
Patterns
There are three main pattern files the cover different types of pattern matching. There is one pattern per line. All lines where the very first character is a “#” is considered a comment and not used as a pattern. Whitespace in the pattern files is not used.
patterns_raw.txt– Raw string matchingpatterns-iraw.txt– Case insensitive raw string matchingpatterns-re.txt– Regular expression matching.
More…
Copyright (C) 2017 scr34m