phpcs-security-audit v2.0.1 releases: finds vulnerabilities and weaknesses related to security in PHP code
phpcs-security-audit
phpcs-security-audit is a set of PHP_CodeSniffer rules that find vulnerabilities and weaknesses related to security in PHP code.
It currently has core PHP rules as well as Drupal 7 specific rules.
The tool also checks for CVE issues and security advisories related to CMS/framework. Using it, you can follow the versioning of components during static code analysis.
The main reason for this project for being an extension of PHP_CodeSniffer is to have easy integration into continuous integration systems. It is also able to find security bugs that are not detected with object-oriented analysis (like in RIPS or PHPMD).
phpcs-security-audit is backed by Floe design + technologies and written by Jonathan Marcil.
Chanelog v2.0.1
- Making this to publish on Packagist with the few bug fixes we did in the last year or so as reported on #39.
Install
Requires PHP CodeSniffer version 3.x with PHP 5.4 or higher.
Because of the way PHP CodeSniffer works, you need to put the Security/ folder from phpcs-security-audit in /usr/share/php/PHP/CodeSniffer/Standards or do a symlink to it.
The easiest way to install is to git clone and use composer that will create the symlink for you:
The package is also on Packagist:
If you want to integrate it all with Jenkins, go see http://jenkins-php.org/ for extensive help.
Usage
Simply point to any XML ruleset file and a folder:
Specifying extensions is important since, for example, PHP code is within .module files in Drupal.
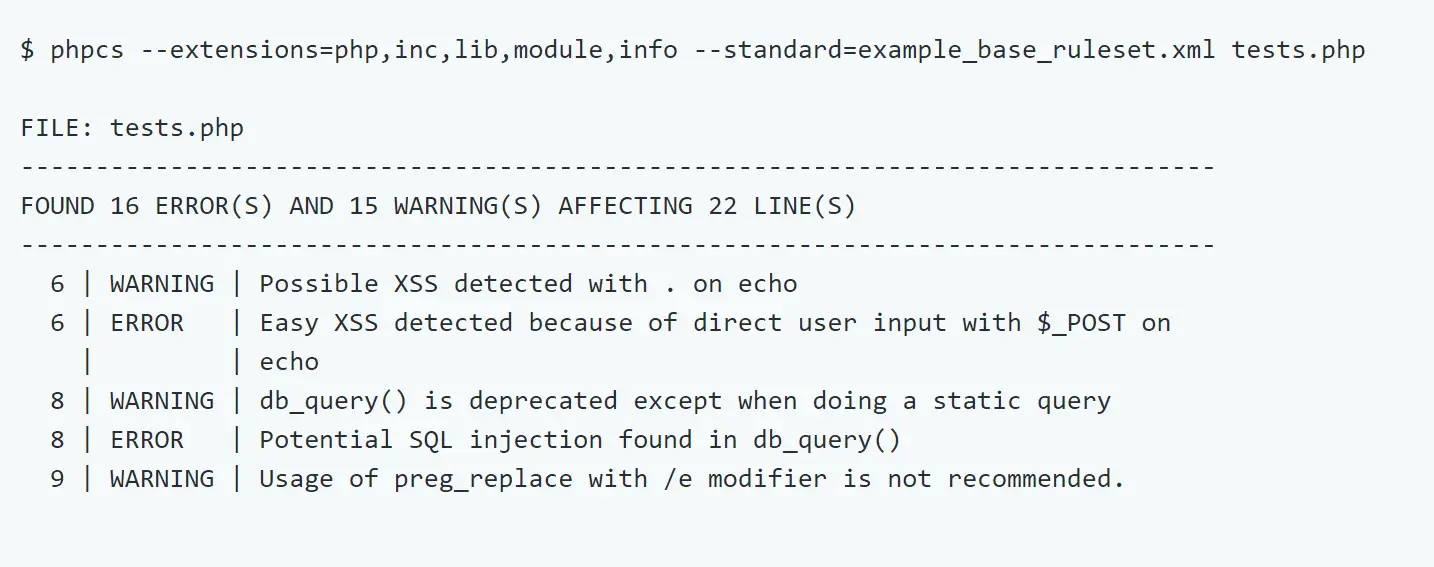
To have a quick example of the output you can use the provided tests.php file:
Drupal note
For the Drupal AdvisoriesContrib you need to change your /etc/php5/cli/php.ini to have:
short_open_tag = On
in order to get rid of “No PHP code was found in this file” warnings.
Please note that only Drupal modules downloaded from drupal.org are supported. If you are using contrib module but from another source, the version checking will probably won’t work and will generate a warning.
More…
Author: jmarcil && Valentin Backofen





