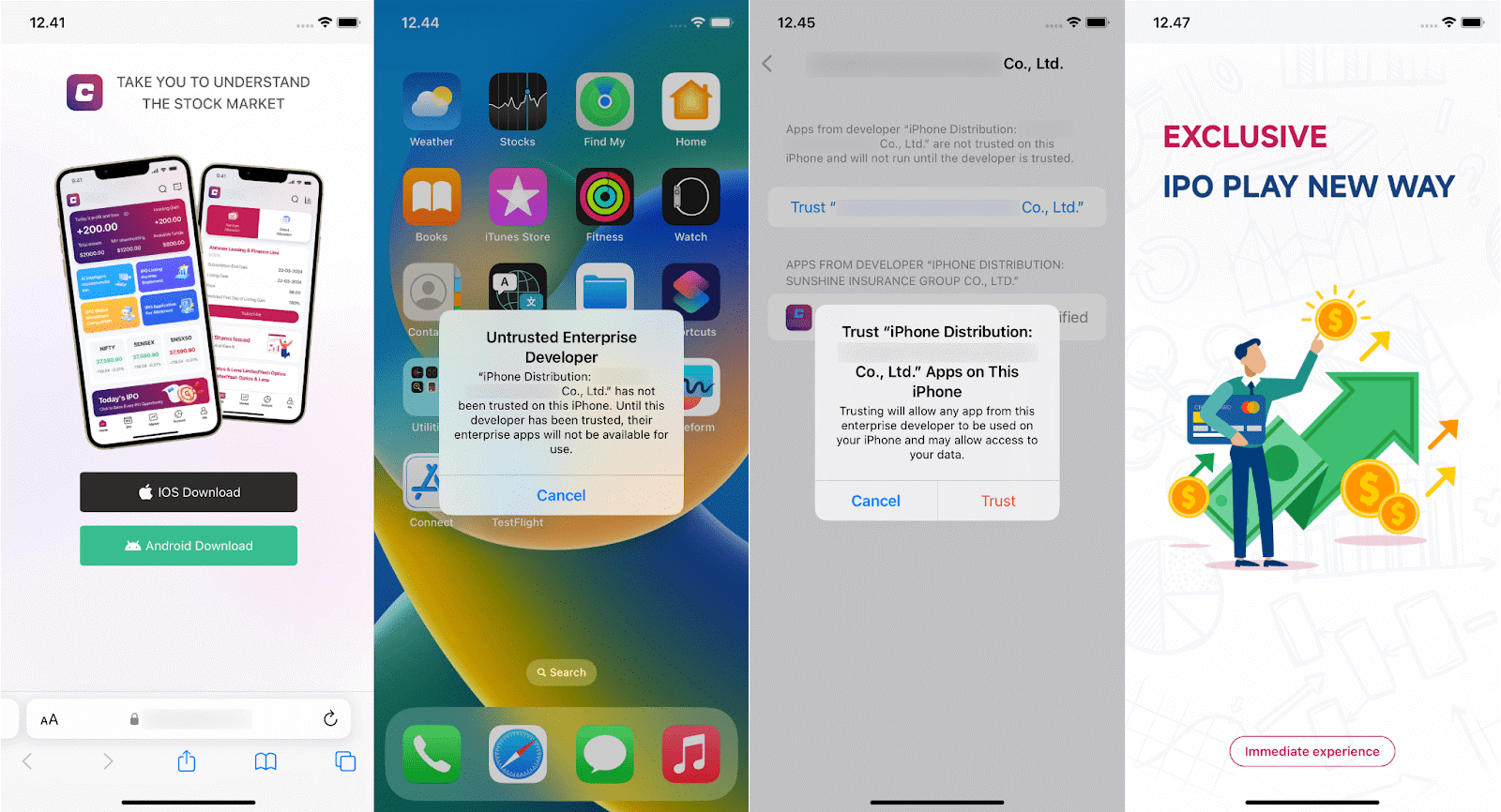
Example of a visit to a phishing website, the installation process and the opening of a fraudulent application | Image: Group-IB
Cybersecurity specialists from Group-IB have uncovered an alarming new trend in fraudulent activity, targeting users of iOS and Android devices through fake trading apps. Dubbed “Pig Butchering,” this elaborate scam lures victims with the promise of lucrative financial gains, only to drain them of their investments once trust has been established. Group-IB’s latest report exposes the tactics behind this growing threat and the widespread impact it is having across multiple regions.
The term “Pig Butchering” refers to the manipulative nature of these scams, where cybercriminals gradually “fatten” their victims through prolonged social engineering tactics before ultimately “butchering” them by stealing their funds. These schemes often begin with cybercriminals reaching out to potential victims via dating apps, social media, or even cold calls, pretending to be financial advisors or investment experts. Over time, they gain the victim’s trust, leading them to invest in fraudulent trading platforms.
Since May 2024, Group-IB analysts have identified a series of fraudulent trading apps targeting iOS and Android users in various regions, including Asia-Pacific, Europe, and the Middle East. These apps, built using the UniApp framework, are specifically designed to appear legitimate, often tricking victims into uploading personal identification documents and depositing funds into bogus trading accounts.
Key findings from Group-IB’s investigation include:
- Fraudulent trading apps have been found in both the Google Play Store and Apple App Store, exploiting users’ trust in these platforms.
- The apps were created using the cross-platform UniApp framework, allowing cybercriminals to target both iOS and Android users with minimal effort.
- Victims are lured into funding fake accounts, with the apps displaying fabricated stock trading activities and inflated account balances to encourage further investments.
- The scam has impacted victims across multiple regions, with Group-IB’s analysis indicating that the reach of this fraud may be even wider.
Initially, one of the fraudulent iOS applications was successfully uploaded to the official Apple Store, relying on the trust users place in Apple’s security mechanisms. Although it has since been removed, the criminals have shifted to distributing these apps via phishing websites, offering downloads for both iOS and Android. In the case of iOS, users are tricked into manually trusting a malicious developer profile, making the app operational once installed.
Once inside the app, victims are required to register using an invitation code—suggesting that these campaigns are highly targeted rather than mass attacks. The criminals then guide victims through a series of steps, including uploading personal documents and funding their trading accounts. However, once the funds are deposited, they are stolen, and the victims are left with nothing but an empty balance.
Group-IB’s analysis uncovered several fraudulent applications classified under a malware family dubbed “UniShadowTrade.” These apps provided multi-language support (English, Portuguese, Chinese, and Hindi) and appeared to offer full trading functionality. Victims were presented with a convincing trading interface, complete with stock listings, account balances, and trading history. However, when victims attempted to withdraw their funds, they found that the account balances were fabricated, and the money was already gone.
Group-IB’s Threat Intelligence and Fraud Protection analysts have detected numerous victims across the Asia-Pacific, European, Middle East, and African regions, underscoring the global scope of this Pig Butchering campaign. As the tactics employed by these fraudsters continue to evolve, it remains critical for users to exercise caution, especially when approached by supposed “investment experts” online.
For more detailed information on Indicators of Compromise (IOCs) and protection strategies, visit Group-IB’s blog and stay updated on the latest developments in the fight against cyber fraud.
Related Posts:
- The Cobalt hacker group is still active, although the leader was arrested
- Group-IB and other security firms assisted Ukrainian police in taking down on DDoS criminal gangs
- Massive Scam Surge: Google Ads Fueling Fraud