PivotSuite: A Network Pivoting Toolkit
PivotSuite
PivotSuite: Hack The Hidden Network – A Network Pivoting Toolkit
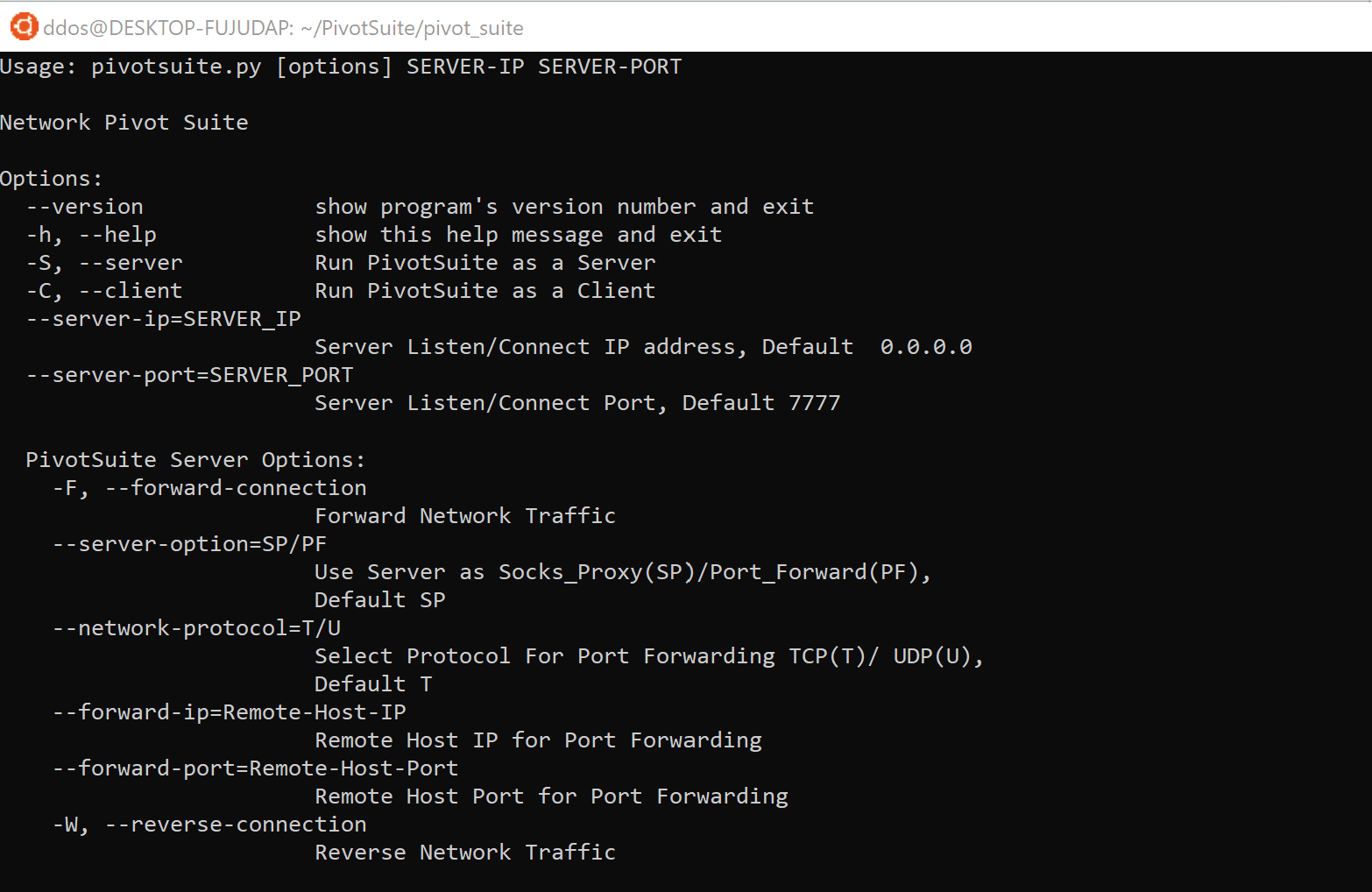
It is a portable, platform-independent and powerful network pivoting toolkit, Which helps Red Teamers / Penetration Testers to use a compromised system to move around inside a network. It is a Standalone Utility, Which can use as a Server or as a Client.
PivotSuite as a Server :
If the compromised host is directly accessible (Forward Connection) from Our pentest machine, Then we can run pivotsuite as a server on the compromised machine and access the different subnet hosts from our pentest machine, Which was only accessible from compromised machine.
PivotSuite as a Client :
If the compromised host is behind a Firewall / NAT and isn’t directly accessible from our pentest machine, Then we can run pivotsuite as a server on the pentest machine and pivotsuite as a client on a compromised machine for creating a reverse tunnel (Reverse Connection). Using this we can reach different subnet hosts from our pentest machine, which was only accessible from compromised machine.
Key Features:
- Supported Forward & Reverse TCP Tunneling
- Supported Forward & Reverse socks5 Proxy Server
- UDP over TCP and TCP over TCP Protocol Supported
- Corporate Proxy Authentication (NTLM) Supported
- Inbuilt Network Enumeration Functionality, Eg. Host Discovery, Port Scanning, OS Command Execution
- It allows to get access to different Compromised host and their network, simultaneously (Act as C&C Server)
- Single Pivoting, Double Pivoting and Multi-level pivoting can perform with the help of PivotSuite.
- It also works as SSH Dynamic Port Forwarding but in the Reverse Direction.
Advantage Over Other tools:
- Doesn’t require admin/root access on Compromised host
- Italso works when a Compromised host is behind a Firewall / NAT When Only Reverse Connection is allowed.
- No dependency is other than python standard libraries.
- No Installation Required
- UDP Port is accessible over TCP
Install
pip install PivotSuite
Use
Example
Case 1 : (Forward TCP Tunneling)
IF the Compromised host is directly accessible from our pentest machine.
Case 2 : (Reverse TCP Tunneling)
IF the Compromised host is behind a Firewall / NAT and directly not accessible from our pentest machine.
IF Corporate Proxy Authentication (NTLM) required for reverse connection on Compromised Host :
Copyright (C) 2019 <Manish Gupta>





