A proof-of-concept (PoC) local privilege escalation (LPE) exploit for the vulnerability tracked as CVE-2022-2602 (CVSS score: 7.0) has been detailed by two security researchers @LukeGix and @kiks.
Linux Kernel could allow a local authenticated attacker to gain elevated privileges on the system, caused by a use-after-free flaw when an io_uring request is being processed. By sending a specially-crafted request, an authenticated attacker could exploit this vulnerability to gain elevated privileges.
According to the seclists, CVE-2022-2602 is a “use-after-free that happens when an io_uring request is being processed on a registered file and the Unix GC runs and frees the io_uring fd and all the registered fds. The order at which the Unix GC processes the inflight fds may lead to registered fds be freed before the io_uring is released and has the chance to unregister and wait for such requests to finish.” The bug affects Linux kernel upstream stable 5.4.y, 5.15.y, and later versions. 5.10.y.
Security researchers ALESSANDRO GROPPO and LukeGix, who shared the PoC exploit code for CVE-2022-2602, also published the write-up (1, 2) with details on the methods used by the exploit.
“The vulnerability is an Use-After-Free in the io_uring subsystem while handling registered files. The IORING_REGISTER_FILES functionality permits to register file descriptors in the io_uring context so that the consumer (the user-land application) do not have to keep them open. It works by passing the list of file descriptors using the io_uring_register syscall. However, the Unix Garbage collector (well explained in this project zero blog post), which its entrypoint is the unix_gc function and its responsability is to de-allocate in-flight sockets, can free these registered files while io_uring is using them, causing an Use-After-Free vulnerability,” GROPPO explained.

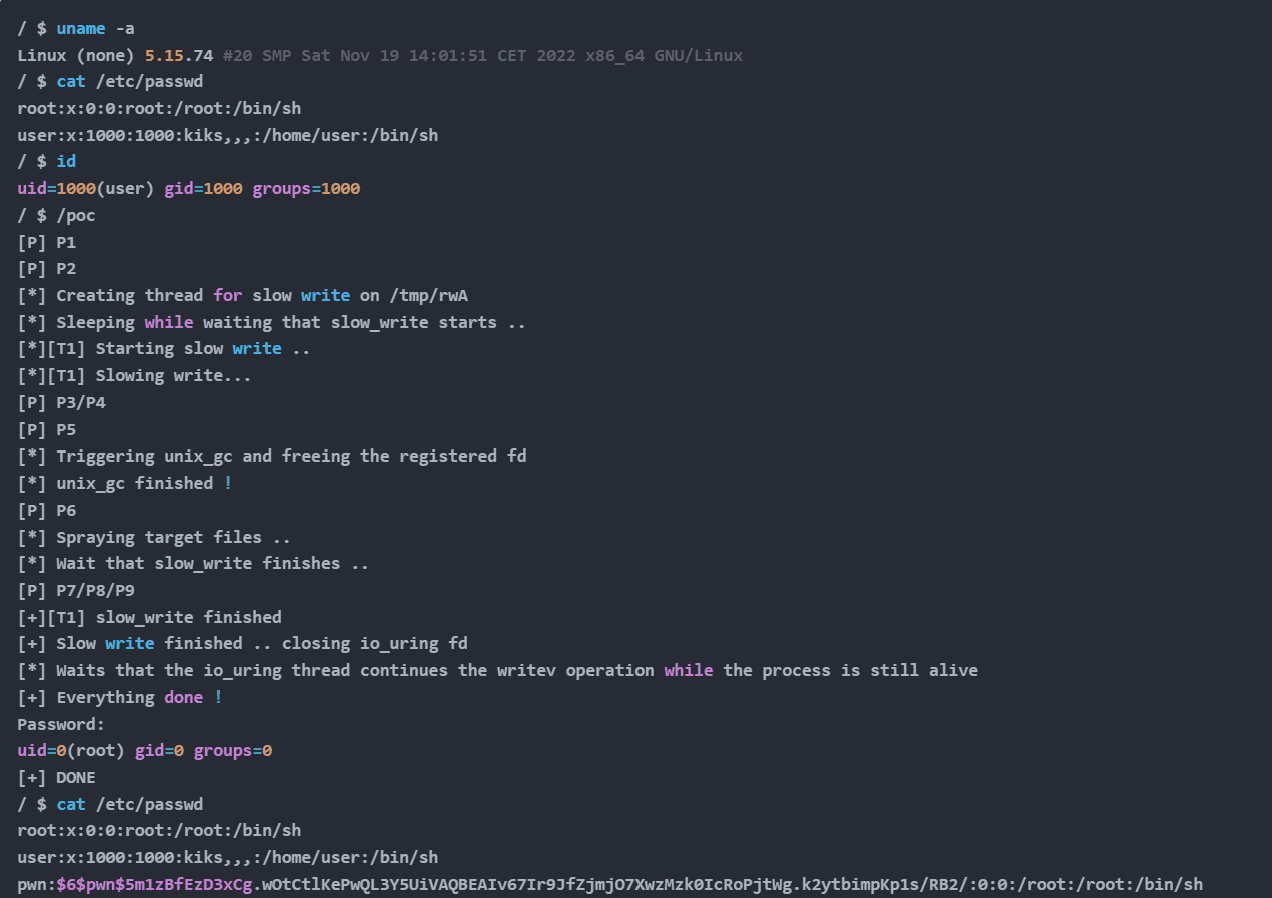
The working PoC exploit (1, 2) has been tested successfully against unpatched 64-bit versions of Linux kernel 5.15.74.
Administrators are advised to apply the appropriate updates on their Linux distributions as soon as they receive them from their respective distro. They’re also recommended to allow only trusted users to access local systems and always monitor affected systems.