Image Credit: Gergely
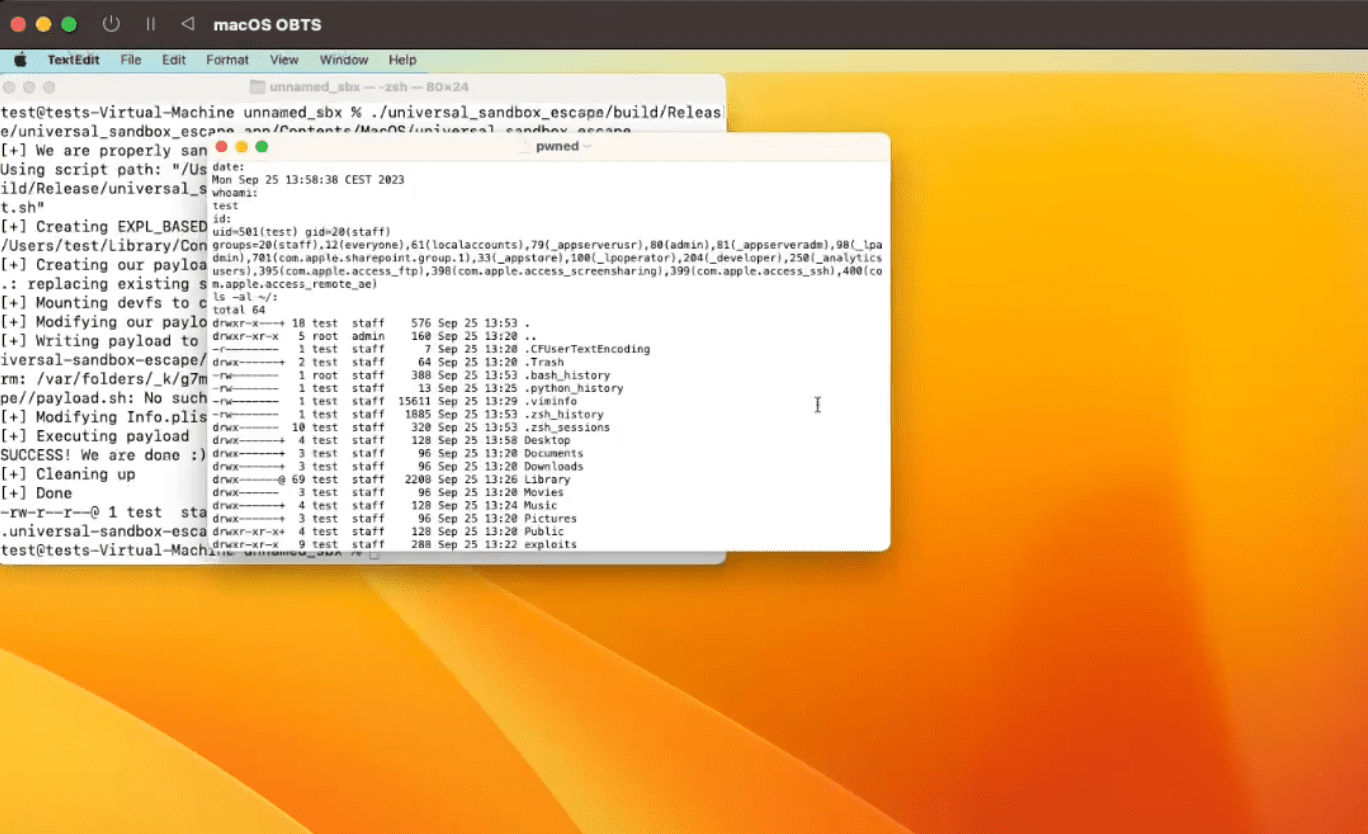
A security researcher has published details and proof-of-concept (PoC) code for a macOS CVE-2023-32364 vulnerability that could be exploited to escape a sandbox and execute code within the Terminal.
The vulnerability in question, designated as CVE-2023-32364 and boasting a concerning CVSS score of 8.6, is not a clandestine, unknown flaw lurking in the dark. In fact, Apple was informed of this defect last year and subsequently rolled out a corrective patch with the release of macOS Ventura 13.5 in July.
In Apple’s advisory, the tech giant elaborated that this flaw provided a sandboxed process with the ability to dodge sandbox restrictions. Essentially, think of the macOS sandbox as a protective bubble. This vulnerability would let a bad actor pop the bubble from the inside, stepping out into the wider system.

However, for an adversary to capitalize on this flaw, they would need the capability to run low-privileged code on the victim’s system. It’s not a glaring open door, but rather a potential backdoor if the attacker can sneak into the initial premises.
Gergely Kalman, who was credited for reporting CVE-2023-32364, pinpoints the bug’s origin to a trio of issues:
- Unprivileged user mounting is an incredibly powerful attack tool
- Relying on optional filesystem features for security is a timebomb
- Mixing of unrelated identities (file / directory) in the context of apps makes defending difficult
To patch this vulnerability, Apple has inhibited sandboxed apps from concocting directories on devfs. Moreover, Apple now mandates the app to sport the “.app” extension, adding a small, yet significant hurdle.
However, the key concern that remains is Apple’s primary corrective measure seems more like a temporary solution. If an attacker can craft a directory devoid of the quarantine flag, the sandbox remains penetrable.
To underscore the potential threat, Gergely recently showcased a detailed breakdown of the code required to exploit this vulnerability, complemented with a visual demonstration. This acted as a chilling reminder of how this seemingly benign bug can be weaponized to break free from the macOS sandbox and run commands in the Terminal. The full PoC exploit code for CVE-2023-32364 is available on Github.
This vulnerability is a serious security flaw that could allow attackers to gain full control of a macOS system. Apple has released a patch for this vulnerability in macOS Ventura 13.5, so it is important to update to the latest version of macOS as soon as possible. Suppose you are unable to update to macOS Ventura 13.5 or later. In that case, you can mitigate the risk of this vulnerability by avoiding untrusted applications and by keeping your software up to date.