
Organizations using Cleo file transfer software are urged to take immediate action as a critical vulnerability, CVE-2024-50623, is being actively exploited in the wild. This zero-day flaw affects Cleo LexiCom, VLTrader, and Harmony products, and allows attackers to execute malicious code remotely on vulnerable systems.
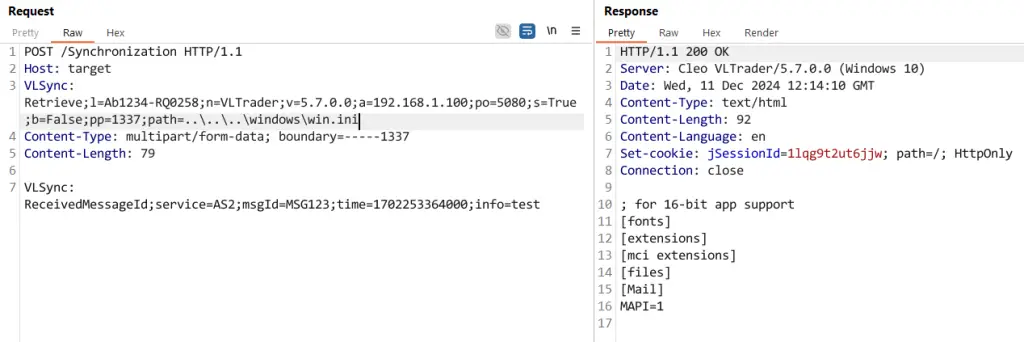
Cleo initially reported and addressed the vulnerability, which allows unrestricted file uploads and downloads, in October 2024. However, security researchers at Huntress have discovered that the patch issued by Cleo was incomplete, leaving systems vulnerable to attack.
“This vulnerability is being actively exploited in the wild and fully patched systems running 5.8.0.21 are still exploitable,” warns Huntress. “We strongly recommend you move any internet-exposed Cleo systems behind a firewall until a new patch is released.”
Evidence of active exploitation began on December 3, 2024, with a significant surge in attacks observed on December 8th. Attackers are exploiting the flaw to upload malicious files to the ‘autorun’ directory of target systems, leading to the execution of malicious PowerShell commands.
WatchTowr, a security research firm, has published technical details and proof-of-concept exploit (PoC) code for CVE-2024-50623, further emphasizing the urgency of the situation.
Cleo has acknowledged the issue and released an updated patch (version 5.8.0.24) to address the vulnerability. “Cleo strongly advises all customers to immediately upgrade instances of Harmony, VLTrader, and LexiCom to the latest released patch (version 5.8.0.24) to address additional discovered potential attack vectors of the vulnerability.”
Organizations are strongly encouraged to update their Cleo software to the latest version immediately and to implement additional security measures, such as network segmentation and intrusion detection systems, to mitigate the risk of compromise.
Related Posts:
- Researchers Detail Critical PHP Flaw CVE-2024-4577 with PoC Exploit Code
- Technical Details Released for Check Point Remote Access VPN 0-Day Flaw
- Unpatched Zero-Day Vulnerability in Mitel MiCollab Exposes Businesses to Serious Security Risks
- CISA & Microsoft Warn of 6 Actively Exploited Zero-Day Vulnerabilities
