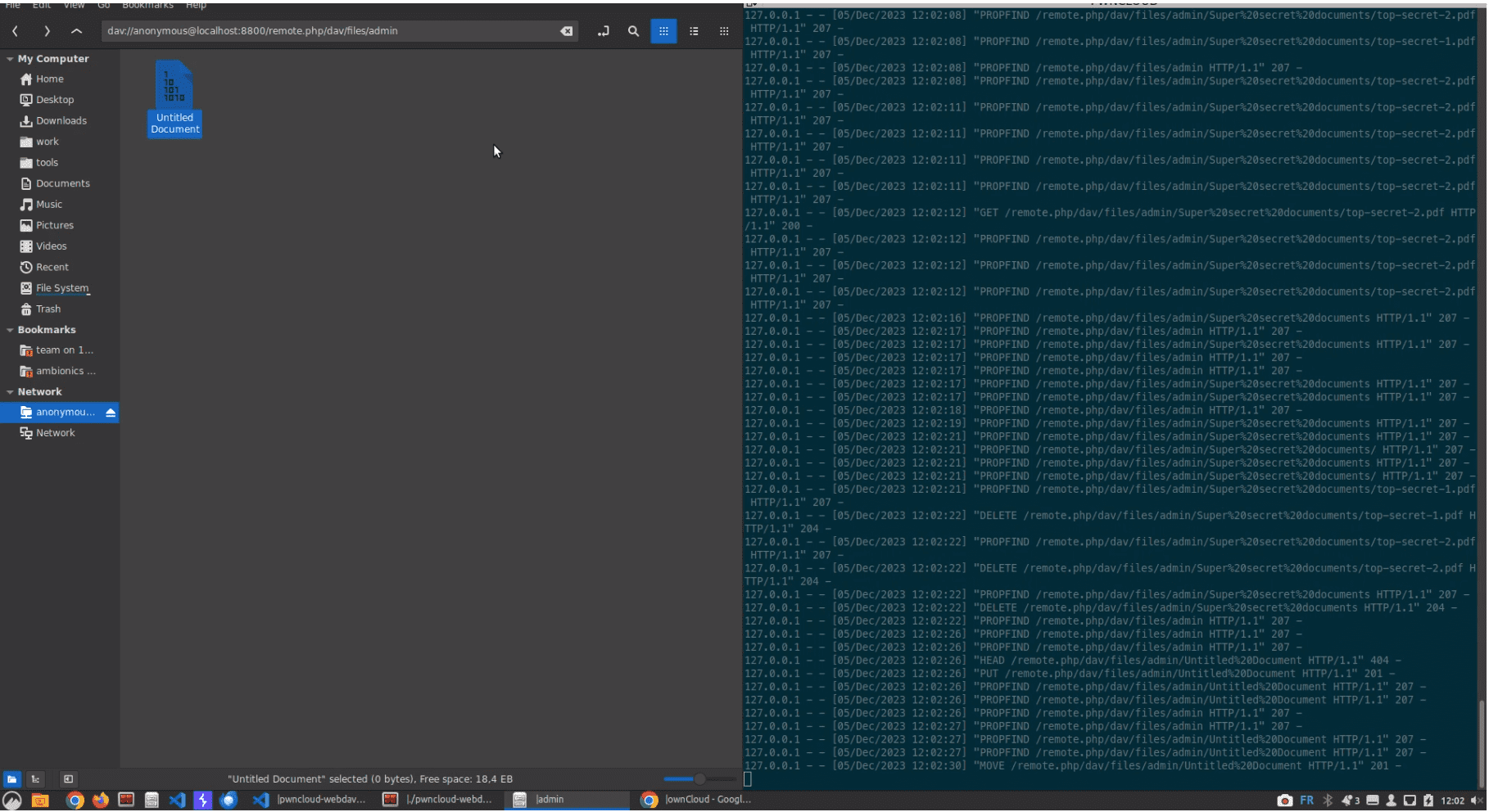
A critical security vulnerability (CVE-2023-49105) affecting ownCloud versions 10.6.0 to 10.13.0 has been made public, and a proof-of-concept (PoC) exploit code is readily available. This flaw has a 9.8 CVSS score and poses a significant threat to ownCloud users as it allows attackers to access, modify, or delete any file without authentication. The vulnerability stems from the fact that ownCloud’s default configuration doesn’t require users to set signing keys.

The real impact of CVE-2023-49105 is twofold and deeply concerning:
- Attackers, even without an account, can gain control (Create, Read, Update, Delete – CRUD) over every file in any account. In certain scenarios, this could even lead to Remote Code Execution (RCE).
- Attackers with standard account credentials can escalate their privileges to an administrator level, thus paving the way for RCE.
The technical details and proof-of-concept (PoC) of this flaw were recently published by a security researcher from Ambionics, bringing to light the severe risks associated with this vulnerability. The researcher’s analysis succinctly puts it: “CVE-2023-49105 allows you to either gain complete access to the files of any user (and potentially, get RCE), or if you already have an account, escalate your privileges to admin, leading to remote code execution.”
The PoC for CVE-2023-49105 is available here.
Further emphasizing the gravity of this situation, the researcher released a video showcasing how an unauthenticated attacker could gain access to the files of any user. This visual demonstration amplifies the urgency for users to patch their systems immediately.
With the PoC exploit code now publicly available, it’s imperative for users of ownCloud versions 10.6.0 to 10.13.0 to swiftly apply the patches.