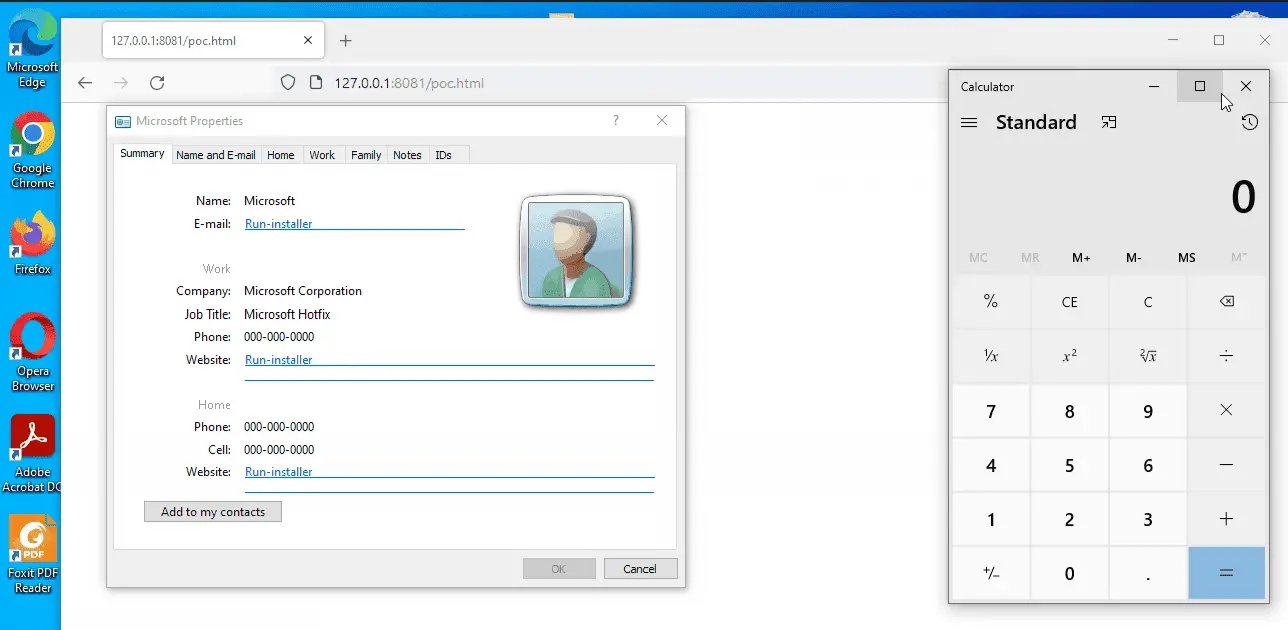
Proof-of-concept (PoC) exploits have been released for a patched Windows Contacts vulnerability that can be exploited for remote code execution.
The flaw, tracked as CVE-2022-44666 (CVSS score of 7.8) and rated important severity, was discovered by John Page (aka hyp3rlinx) of ApparitionSec and j00sean and it was patched by the tech giant with its December 2022 Patch Tuesday updates.
Microsoft Windows could allow a remote attacker to execute arbitrary code on the system, caused by a flaw in the Contacts component. By persuading a victim to open specially-crafted content, an attacker could exploit this vulnerability to execute arbitrary code on the system.
A specific flaw exists within the processing of CONTACT files. Crafted data in a CONTACT file can cause Windows to display a dangerous hyperlink. The user interface fails to provide sufficient indication of the hazard. An attacker can leverage this vulnerability to execute code in the context of the current user.

Researcher j00sean this week announced the release of a PoC exploit for CVE-2022-44666. However, his PoC does not achieve remote code execution – it shows how an attacker can leverage the flaw to execute the payload, and finally run notepad.exe. The researcher also exploits this bug to privilege escalation.
A technical analysis of the CVE-2022-44666 bug was published and several PoC exploits have now been created on the Github page, including:
The files located in ./report-pocs/:
- ./report-pocs/exploit.vcf: Proof of concept to double-click it.
- ./report-pocs/exploit.zip: Zipped file to be downloaded which includes all the tricks to exploit the bug (video: full-payload.gif)
- ./report-pocs/hidden/payload.lnk: LNK file to run the payload with cmdline arguments.
- ./report-pocs/hidden/payload.bin: DLL payload. It finally runs notepad.exe
- ./report-pocs/hidden/payload.exe: Executable payload. It finally runs notepad.exe
And files located in ./src:
- dllmain.cpp: DLL library used as payload (payload.bin).
- payload.cpp: Executable used as payload (payload.exe).