Image Credit: Mohammed Adel
A critical vulnerability, identified as CVE-2024-20419, has been publicly disclosed by security researcher Mohammed Adel, who published a detailed writeup along with proof-of-concept (PoC) exploit code. This vulnerability affects Cisco’s Smart Software Manager On-Prem (SSM On-Prem) and has been assigned a maximum CVSS score of 10, indicating its severe potential for exploitation.
The vulnerability stems from a flaw in SSM On-Prem’s authentication system, allowing unauthenticated attackers to remotely change any user’s password—including administrator accounts—without requiring the original credentials. This security flaw puts affected systems at significant risk of unauthorized access and potential full system compromise.
The root cause of CVE-2024-20419 lies in the improper handling of authorization tokens during the One-Time Password (OTP) generation process. Specifically, the vulnerability is located in the /backend/reset_password/generate_code endpoint, which is responsible for generating an OTP for users attempting to reset their passwords.
In normal operation, this endpoint should generate and send an OTP to the user, who must then verify the code to proceed with the password reset. However, in vulnerable versions of Cisco SSM On-Prem, the application erroneously includes the authorization token (auth_token) in the response to the OTP generation request. This token is a critical piece of data that should only be issued after successful OTP verification.
By prematurely exposing the auth_token, the application inadvertently allows attackers to bypass the OTP verification step entirely. With this token, an attacker can directly authorize themselves to reset the password of any account, including administrative accounts, without needing to know or verify the original credentials.
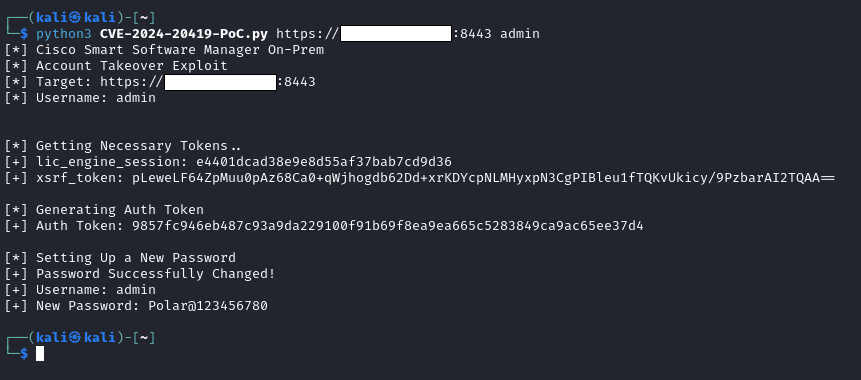
Mohammed Adel’s write-up includes a visual demonstration of the PoC exploit, showcasing the ease with which the CVE-2024-20419 vulnerability can be leveraged to take over administrative accounts. The public availability of this exploit code significantly raises the stakes, as it provides a blueprint for attackers to potentially exploit unpatched systems.
While the vulnerability has been rated as critical, the good news is that the security threat monitoring platform Shadowserver has detected only over 40 instances of vulnerable systems exposed to the internet. However, with the exploit code now publicly available, the risk of exploitation is expected to rise if patches are not applied promptly.

The Shadowserver Foundation
Cisco has responded quickly by issuing patches for all affected versions of Cisco SSM On-Prem. At the time of writing, there are no reports of in-the-wild exploitation, but this could change rapidly given the ease of exploitation demonstrated by the PoC.
Administrators are strongly advised to upgrade to the patched versions of Cisco SSM On-Prem immediately. No workarounds are available for this vulnerability, meaning that the only way to secure affected systems is by applying the official patches released by Cisco.
Failing to patch could result in severe consequences, including unauthorized access to critical systems, data breaches, and potential loss of control over the entire network environment.
Related Posts:
- Critical Flaw in Cisco Smart Software Manager Opens Door to Account Takeover
- Cisco Warns of Public PoC Exploit Code of Critical CVE-2024-20419 (CVSS 10) Flaw
- Massive Android SMS Stealer Campaign Uncovered: Over 100,000 Malicious Apps Targeting Global Users
- Zero-Day Vulnerability in SysAid On-Prem Software