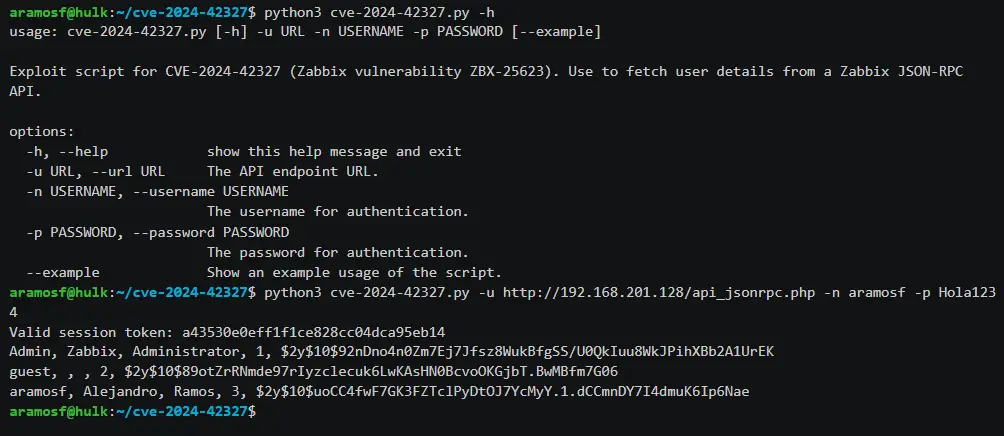
Security researcher Alejandro Ramos has published a detailed technical analysis and proof-of-concept (PoC) exploit code for CVE-2024-42327, a critical SQL injection vulnerability affecting Zabbix, a widely used open-source enterprise network and application monitoring platform. With a CVSSv3 score of 9.9, this flaw represents a near-perfect criticality rating and has serious implications for Zabbix deployments worldwide.
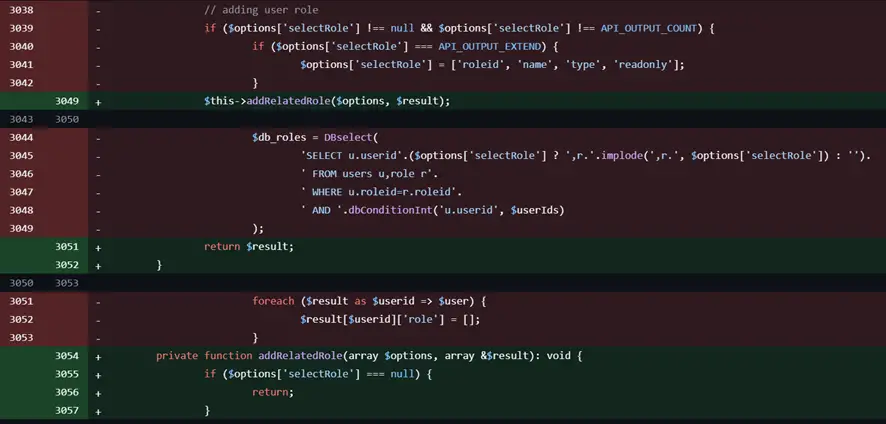
The vulnerability resides in the Zabbix frontend, specifically in the CUser class’s addRelatedObjects function, which is called by the CUser.get method. According to the project’s description, the flaw allows non-admin user accounts with default User roles or any role that permits API access to exploit the vulnerability. Ramos elaborates, “The vulnerability is in the user.get method, specifically in selectRole, which chains an array without validating the input data [Translated].”
Once exploited, this SQL injection could enable attackers to escalate privileges, potentially compromising the monitoring system and gaining access to sensitive enterprise data.
The flaw was originally discovered by Márk Rákóczi and reported through the HackerOne bug bounty platform. Zabbix explained: “An SQLi exists in the CUser class in the addRelatedObjects function, this function is being called from the CUser.get function which is available for every user who has API access.”
Zabbix has acknowledged the severity of the issue and urged users to immediately update their installations. Affected versions include 6.0.0 through 6.0.31, 6.4.0 through 6.4.16, and 7.0.0. Users should upgrade to the latest patched versions: 6.0.32rc1, 6.4.17rc1, or 7.0.1rc1, to mitigate the risk.
Zabbix’s global customer base includes thousands of organizations across every continent. Enterprises that use Zabbix for critical monitoring operations could face severe disruptions if this vulnerability is exploited. From data exfiltration to privilege escalation, attackers could leverage this flaw to gain unauthorized control over Zabbix environments.
Ramos has released a PoC exploit for CVE-2024-42327 on GitHub, significantly raising the risk of exploitation. The SQL injection vulnerability can be triggered by API-accessible accounts, making it essential for organizations to restrict unnecessary API permissions and upgrade their Zabbix installations without delay.
Related Posts:
- CVE-2024-42327 (CVSS 9.9): Critical SQL Injection Vulnerability Found in Zabbix
- FBI arrests CEO Phantom who sold customized BlackBerry to Sinaloa drug trafficking group
- CVE-2024-22116 (CVSS 9.9): Critical RCE Vulnerability Found in Zabbix Monitoring Solution
- Zabbix Addresses Multi Vulnerabilities, Including RCE CVE-2024-36461 (CVSS 9.1) Flaw
- CVE-2024-42330 (CVSS 9.1): Zabbix Patches Critical Remote Code Execution Vulnerability