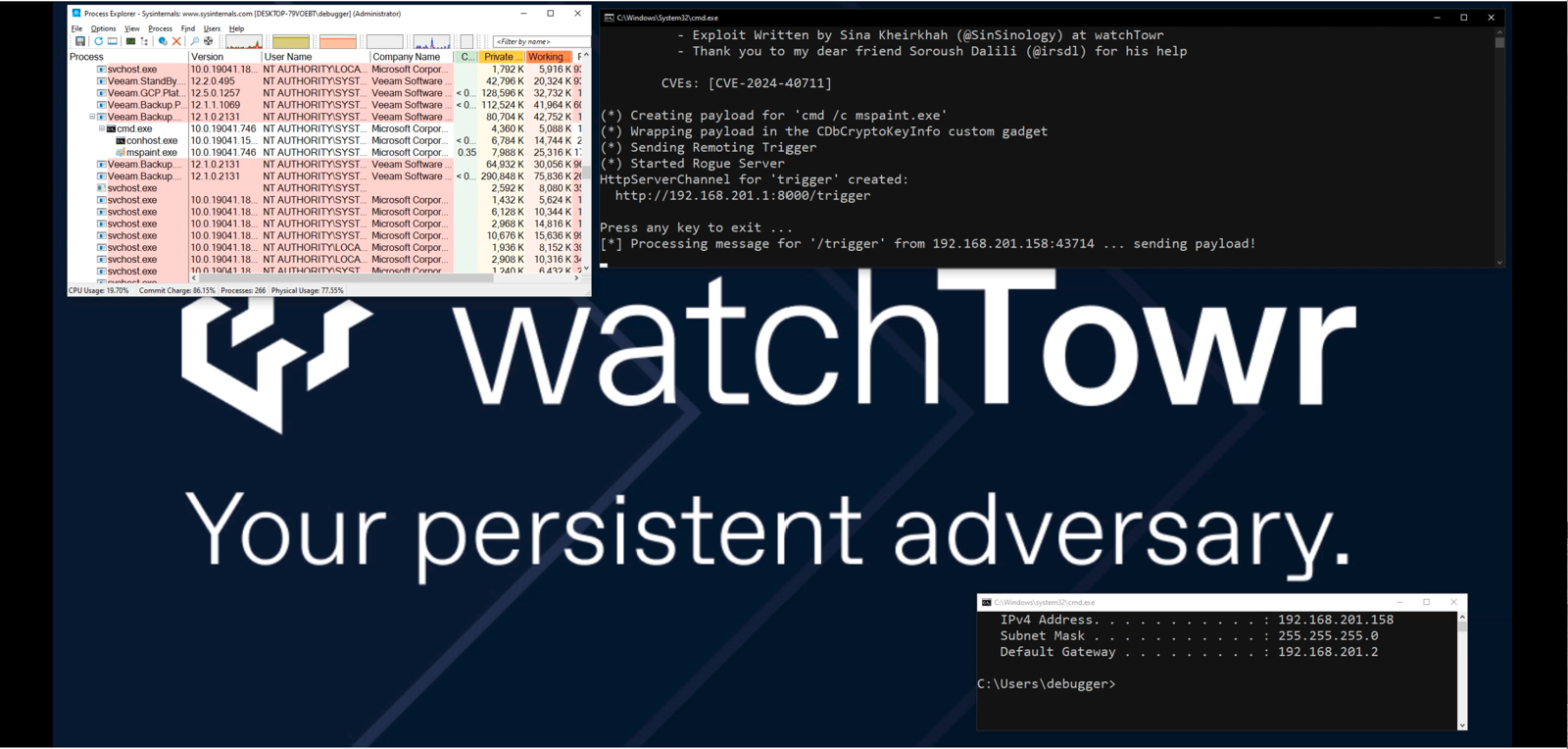
In a major revelation for cybersecurity professionals, security researcher Sina Kheirkhah (@SinSinology) of watchTowr has published an analysis and proof-of-concept (PoC) exploit for CVE-2024-40711, a critical vulnerability in Veeam’s widely-used Backup & Replication software. With a CVSS score of 9.8, this unauthenticated remote code execution (RCE) issue poses a severe threat to enterprise environments running versions 12.1.2.172 and below, as highlighted by Veeam’s security advisory.
CVE-2024-40711 was initially reported by Florian Hauser from CODE WHITE GmbH, and it quickly drew attention due to its high potential for exploitation. This vulnerability stems from Veeam’s use of .NET Remoting, an aging communication mechanism notorious for being vulnerable to deserialization attacks. While the initial advisory labeled the bug as unauthenticated RCE, further analysis revealed that in certain instances, attackers would need low-level credentials due to an inconsistency between the advisory’s description and the assigned CVSS score. Nevertheless, the risk remains high.
The exploitation path is particularly concerning because it enables attackers to craft malicious payloads that bypass Veeam’s protective measures. The flaw is rooted in the software’s reliance on a deserialization process that uses a whitelist/blacklist system to control what class types can be deserialized. Researchers found that an oversight in this system, specifically the omission of the ObjRef class, allowed attackers to remotely execute code on the server running Veeam’s backup service.
This type of vulnerability isn’t new in the .NET ecosystem, where older remoting frameworks have often fallen victim to deserialization exploits. The ability to manipulate serialized data in this way has opened the door for attackers to fully compromise vulnerable systems.
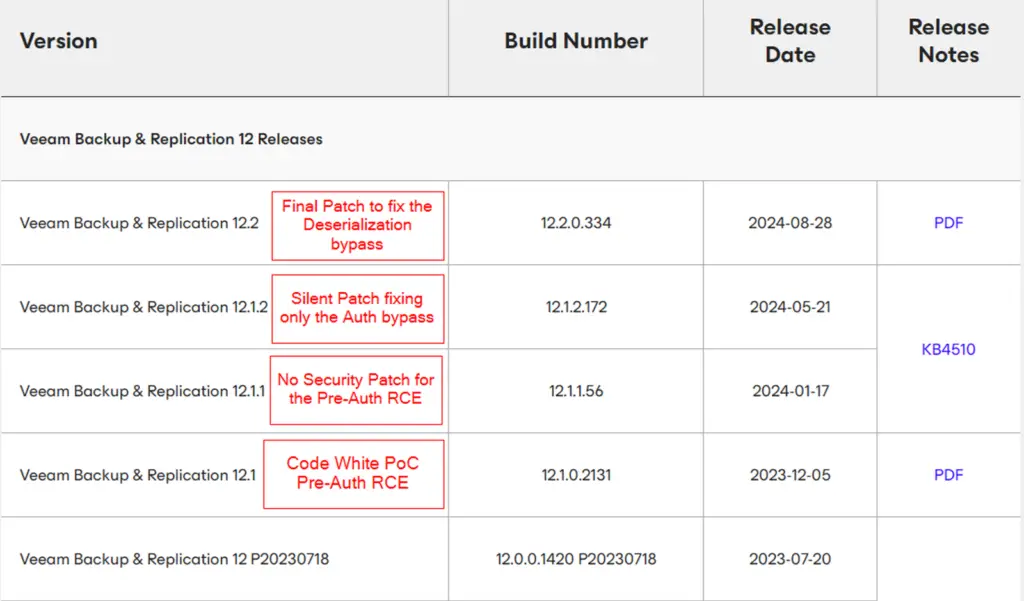
In response to the vulnerability, security teams engaged in patch diffing to assess the changes made in the updated versions of Veeam Backup & Replication. They discovered 1,900 file modifications, of which only 700 could be quickly dismissed as non-security-related. The complexity and sheer volume of changes indicate that Veeam’s patching process went far beyond CVE-2024-40711, potentially addressing a range of additional security flaws.
Veeam’s patching process for CVE-2024-40711 has raised some questions. The company issued two separate releases addressing different components of the vulnerability. The first patch (version 12.1.2.172) focused on tightening the authorization process, ensuring that low-level credentials were required for exploitation. The second patch (version 12.2.0.334) fully resolved the deserialization bug, closing the door on RCE attempts altogether.
This staggered patch approach has led some in the cybersecurity community to speculate that Veeam might have downplayed the severity of the vulnerability. While this remains unconfirmed, the suspicion stems from the fact that the initial patch did not fully mitigate the RCE threat, leaving systems partially exposed.
To complicate matters further, a proof-of-concept (PoC) exploit for CVE-2024-40711 has been made publicly available on GitHub. This gives attackers a ready-made tool to launch attacks against unpatched systems, heightening the urgency for enterprises to apply the latest updates.
Cybersecurity firm Rapid7 has warned that previous Veeam vulnerabilities have been exploited in the wild, often by ransomware groups, underscoring the potential severity of this new flaw. “More than 20% of Rapid7 incident response cases in 2024 so far have involved Veeam being accessed or exploited in some manner, typically once an adversary has already established a foothold in the target environment,” Rapid7 wrote.
Veeam has been proactive in releasing advisories and patches for this critical vulnerability. Enterprises using Veeam Backup & Replication are strongly urged to update to version 12.2.0.334 or later to ensure full protection. In addition to applying the patch, organizations should also review their network access controls, disable any unnecessary services, and monitor their backup infrastructure for any signs of unauthorized access.
Related Posts:
- Veeam Backup & Replication Faces RCE Flaw– CVE-2024-40711 (CVSS 9.8) Allows Full System Takeover
- Veeam Users Beware: PoC Exploit for Critical CVE-2024-29849 Flaw Released
- EstateRansomware Exploits Veeam Vulnerability (CVE-2023-27532) in Sophisticated Attack
- Critical Flaws in Veeam ONE Expose Systems to RCE (CVE-2024-42024) and Credential Theft (CVE-2024-42019)
- Veeam Patches Critical Security Flaw in Recovery Orchestrator (CVE-2024-29855)
- CISA Alert: CVE-2023-27532 & CVE-2023-38035 Vulnerabilities Being Exploited in Attacks