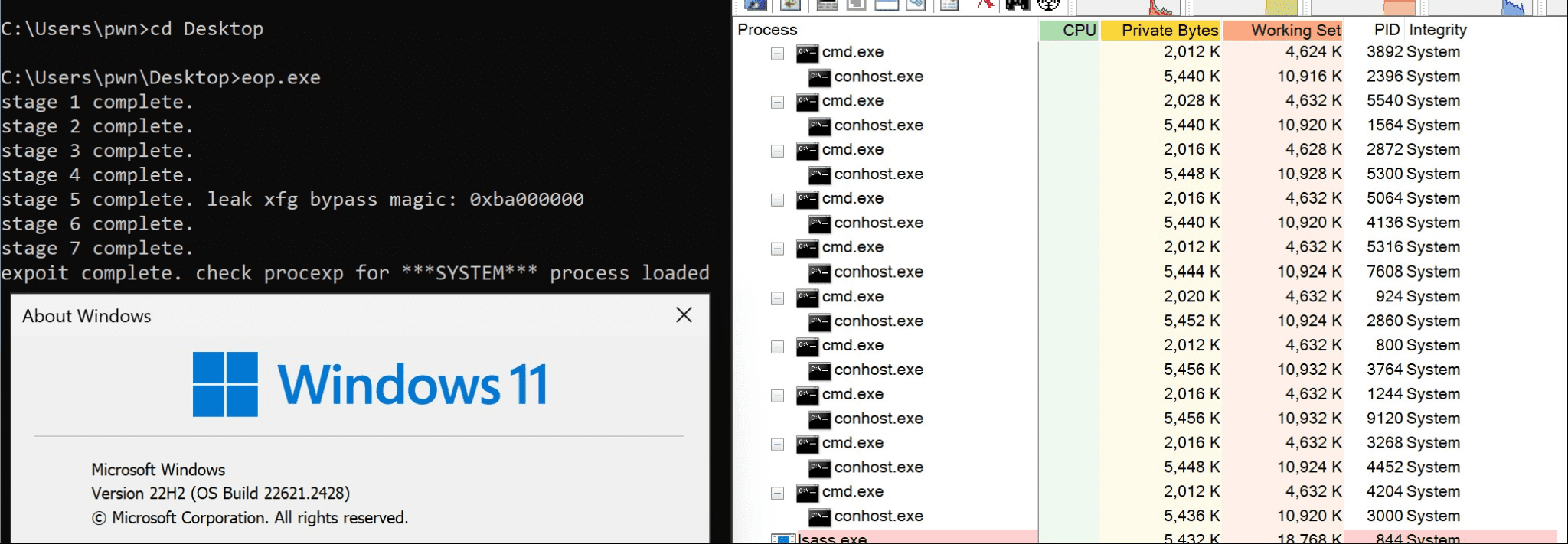
Security researcher published the technical details and a proof-of-concept (PoC) exploit for a patched elevation of privilege vulnerability in the Windows Telephony service tracked as CVE-2024-26230. This flaw, which has a CVSS score of 7.8, presents a significant risk, allowing attackers to gain SYSTEM privileges on affected systems through a use-after-free vulnerability in the telephony service.
The Windows Telephony Service is an RPC-based service that, while not running by default, can be activated by invoking the StartServiceW API with standard user privileges. The vulnerability arises in the way this service handles objects with the magic value “GOLD,” a unique identifier used within the service’s global handle table.
The service’s interface consists of three primary functions:
- ClientAttach: Creates a context handle.
- ClientRequest: Processes requests using the specified context handle.
- ClientDetach: Releases the context handle.
The vulnerability is rooted in the ClientRequest method, where a global variable named “gaFuncs” routes requests to specific dispatch functions. These functions process various objects, which are created and inserted into the global handle table by the NewObject function.
However, when handling objects with the “GOLD” magic value, a critical oversight occurs. The telephony service fails to check whether the “GOLD” object is owned by the context handle before freeing it. This flaw can be exploited by creating two context handles: one to hold the “GOLD” object and another to invoke the FreeDiagInstance dispatch function, which frees the “GOLD” object. As a result, the original context handle retains a dangling pointer to the freed object, leading to a use-after-free vulnerability when the service later attempts to reference it.
The exploit for this vulnerability was developed by k0shl of Cyber Kunlun, who employed a novel technique to bypass eXtended Flow Guard (XFG) mitigation on Windows 11—a security feature designed to prevent such attacks. Following k0shl’s detailed analysis, another researcher, Wa1nut4, published a proof-of-concept (PoC) exploit code for CVE-2024-26230 on GitHub, making the flaw widely accessible to attackers.
The exploit works by manipulating the input buffer of the RPC client, which can be fully controlled by the attacker. This control ultimately leads to the telephony service crashing when it attempts to reference a virtual function through the dangling pointer.
Successful exploitation of this vulnerability has severe consequences, granting attackers full control over the compromised system. With SYSTEM privileges, malicious actors can execute arbitrary code, install malware, exfiltrate sensitive data, and establish persistent backdoors.
Microsoft addressed this vulnerability in its April 2024 security updates. System administrators and users are strongly urged to apply these updates immediately to protect their systems.
Related Posts:
- Bitcoin Gold Hacked: Lose $18 Million
- CVE-2024-43044: Critical Jenkins Vulnerability Exposes Servers to RCE, PoC Exploit Published
- CVE-2024-45488: Flaw in Safeguard for Privileged Passwords Enables Unauthorized Access