The world of Linux users has been abuzz for the past couple of days, and for good reason. A previously identified security flaw in the GNU C library’s ld.so dynamic loader, dubbed “Looney Tunables“, is back in the limelight. But this time, it’s the release of a Proof-of-Concept (PoC) exploit that’s stirring the pot.
When we first reported the discovery of Looney Tunables, details were scant. Originating in the ld.so dynamic loader within the GNU C library, the flaw, if leveraged successfully, could let malevolent actors escalate local privileges and attain root access. Such authority would grant virtually unrestricted system control.

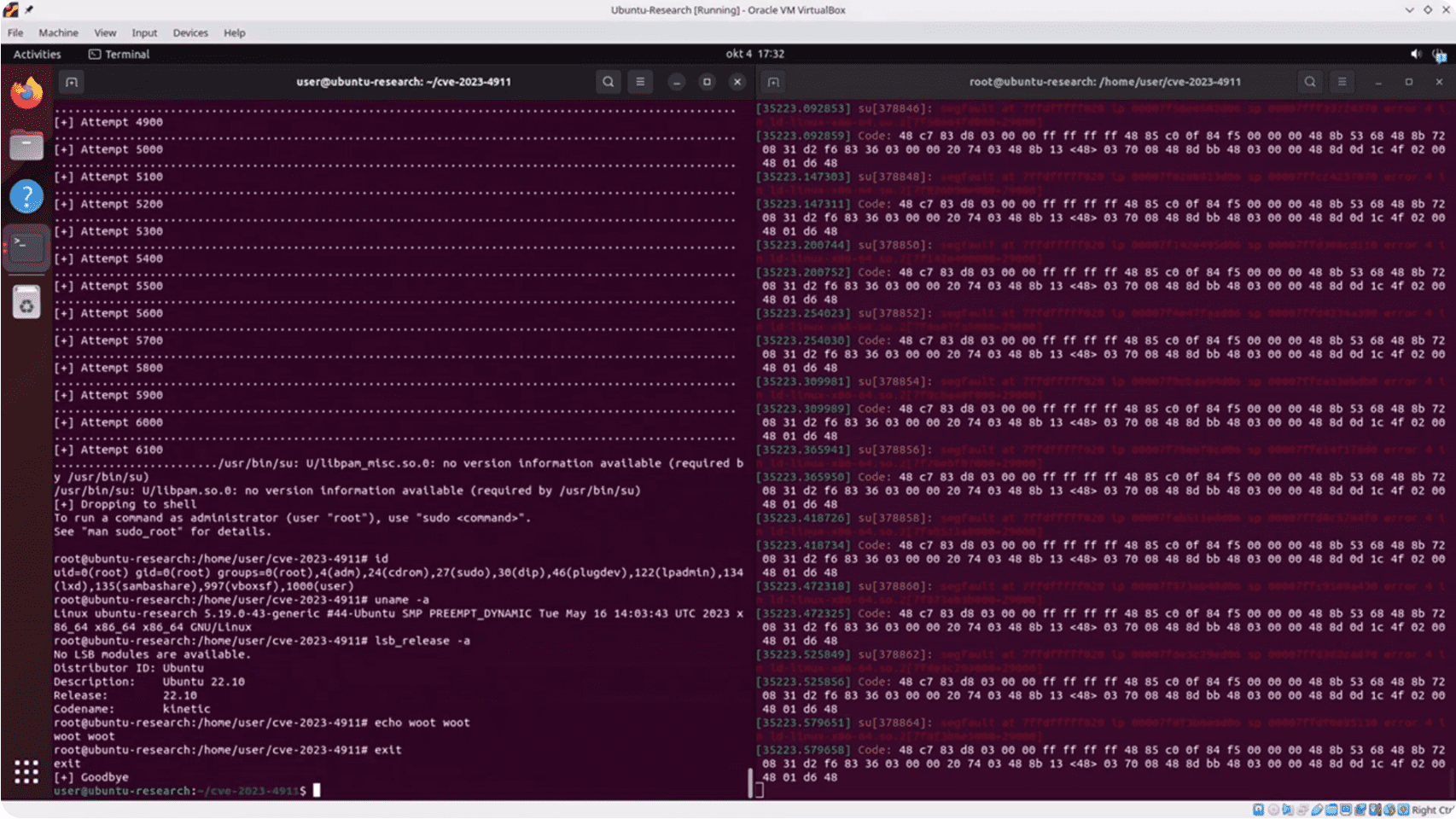
Now, thanks to the cybersecurity firm Qualys, we have more clarity. Several security researchers have now released PoC for the CVE-2023-4911 vulnerability. With a CVSS score of 7.8, this issue stems from a buffer overflow that lurks in the dynamic loader’s processing of the GLIBC_TUNABLES environment variable.
To understand its gravity, one needs to appreciate the significance of the GNU C library, fondly called glibc. This cornerstone library is a bedrock of Linux systems, providing essential features like open, read, write, malloc, and many more. The dynamic loader in glibc is vital, responsible for prepping and launching programs, managing shared object dependencies, and linking them during runtime.
The tentacles of this vulnerability spread far, touching major Linux distributions such as Fedora, Ubuntu, and Debian. Although certain distributions like Alpine Linux remain unaffected, the consensus is that many others are susceptible.
Speaking on the issue, Saeed Abbasi, a stalwart from Qualys Threat Research Unit, stated, “The presence of a buffer overflow vulnerability in the dynamic loader’s handling of the GLIBC_TUNABLES environment variable poses significant risks to numerous Linux distributions.”
GLIBC_TUNABLES, designed to fine-tune applications synced with glibc, is invaluable for developers and system administrators. Exploiting it could negatively impact system performance, reliability, and, crucially, security.
According to Red Hat’s advisory, a local cybercriminal could manipulate this flaw by using malevolently crafted GLIBC_TUNABLES environment variables. The goal? To launch binaries with SUID permissions and execute code with higher privileges.
Besides the PoC exploit code for the CVE-2023-4911 bug, researchers have also unveiled a video demonstration. This visual proof serves as a potent reminder of the vulnerability’s potential and underscores the urgent need for corrective measures.
While the release of PoC exploits often ignites concern, it also accelerates awareness and the deployment of solutions. As Linux users and administrators, it’s imperative to stay informed, keep systems updated, and remain vigilant against the ever-evolving landscape of cybersecurity threats.