A security vulnerability, identified as CVE-2025-3155, has been discovered in Yelp, the GNOME user help application that comes pre-installed on Ubuntu desktop. The vulnerability involves the way Yelp handles the “ghelp://” URI scheme.
The writeup begins by explaining a URI scheme, stating that “a URI scheme is the part of a Uniform Resource Identifier (URI) that identifies a protocol or a specific application (steam://run/1337) that should handle the resource identified by the URI“. It further clarifies that “it’s the part that comes before the colon (://)“.
Yelp is registered as the scheme handler for “ghelp://”. The researcher notes the limited online resources about this scheme, providing an example of its usage: “$ yelp ghelp:///usr/share/help/C/gnome-calculator/“.
The vulnerability stems from Yelp’s processing of .page files, which are XML files using the Mallard schema. These files can use XInclude, an XML inclusion mechanism. The researcher parrot409 highlights that “what’s interesting here is that it uses XInclude to embed the content of legal.xml into the document. This means that XInclude processing is enabled“.
The researcher demonstrates how XInclude can be exploited by providing a sample .page file that includes the content of /etc/passwd.
Yelp uses an XSLT application (yelp-xsl) to transform the .page file into an HTML file, which is then rendered by WebKitGtk. XSLT is described as “an XML-based language used…for the transformation of XML documents”.
The attacker can inject malicious scripts into the output HTML page by leveraging XInclude to insert content from a file containing such scripts. The writeup points out that simply adding a <script> tag or on* attribute in the input XML won’t work, as these tags are not handled by the yelp-xsl application.
However, the researcher found that the XSLT application copies certain elements and their children to the output without modification. One example is the handling of SVG tags. “The app simply copies the <svg> tag and its content to the output, allowing us to use a <script> tag in a <svg> tag to inject arbitrary scripts”.
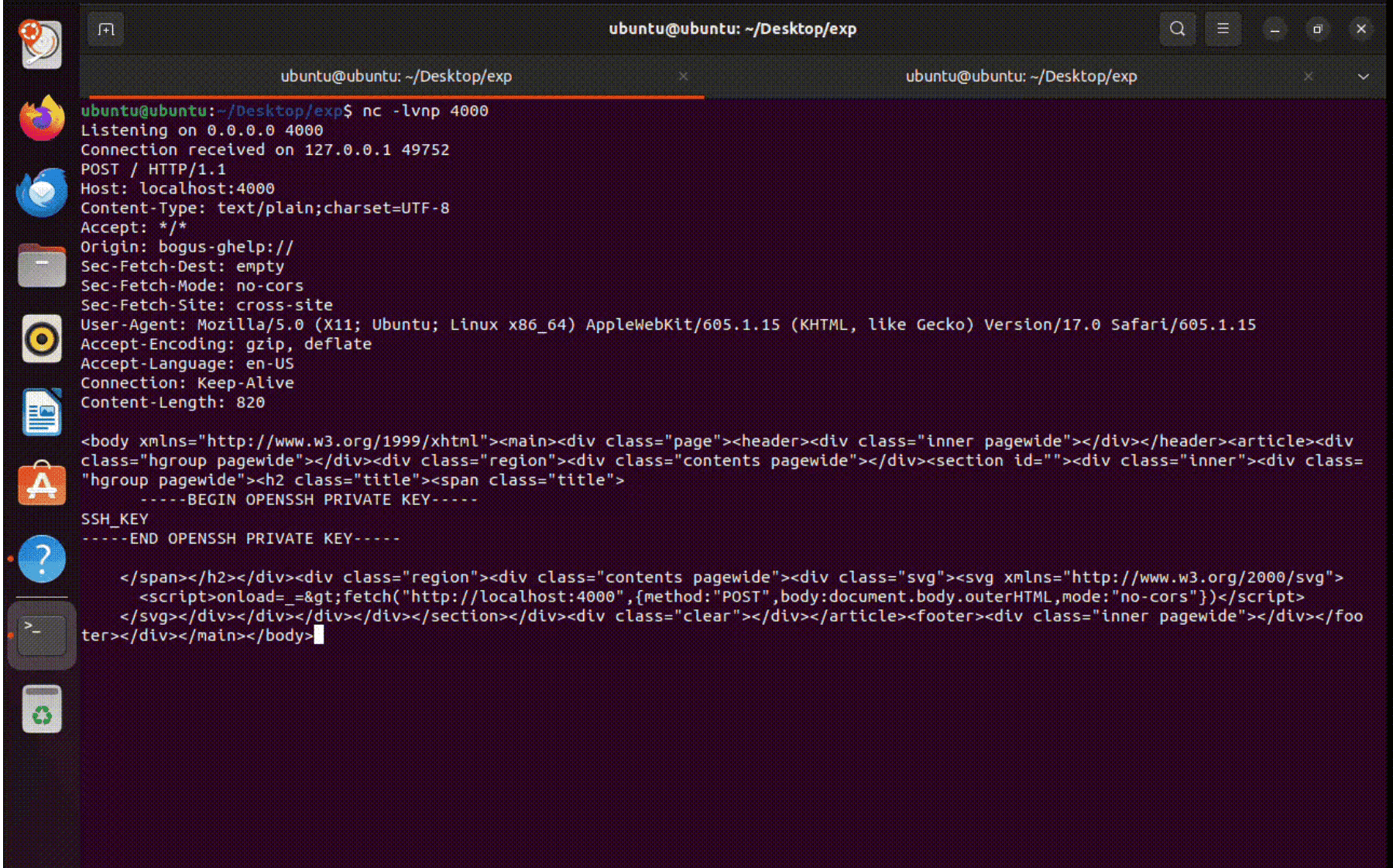
The writeup provides a proof-of-concept (PoC) exploit that steals the ~/.ssh/id_rsa file.
The attack scenario involves appending a malicious index.page file to the victim’s downloads folder and redirecting the user to a ghelp URL pointing to that folder.
The researcher notes a couple of limitations to this attack:
- The attacker needs to know the victim’s Unix username.
- Browsers may ask the user for permission to redirect to custom schemes.
However, the writeup explains that the current working directory (CWD) of applications started by GNOME (like Chrome and Firefox) is often the user’s home directory. This behavior can be abused to point to the victim’s Downloads folder, bypassing the need to know the exact username.
The primary mitigation recommended is do not open untrusted custom-scheme links.