PoC released for Windows Common Log File System 0-Day (CVE-2023-28252)
Exploit code for a severe zero-day vulnerability affecting the Windows Common Log File System (CLFS) is now in the open, being actively manipulated by nefarious actors. Microsoft has responded by patching the vulnerability, known for its active exploitation by cybercriminals to escalate privileges and deliver the dreaded Nokoyawa ransomware payloads.
Cognizant of the continuous exploitation, the Cybersecurity and Infrastructure Security Agency (CISA) swiftly added this Windows zero-day, identified as CVE-2023-28252, to its catalog of Known Exploited Vulnerabilities. Consequently, CISA ordered all Federal Civilian Executive Branch (FCEB) agencies to button down their hatches and fortify their systems against this imminent threat by May 2nd.

The detection and reporting of this high-risk security flaw fell upon three vigilant individuals: Boris Larin of Kaspersky, Genwei Jiang of Mandiant, and Quan Jin of DBAPPSecurity’s WeBin Lab. The vulnerability, currently causing digital mayhem, affects all supported Windows server and client versions and can be manipulated by local attackers in low-complexity attacks without any user interaction.
Successful exploitation of the vulnerability permits threat actors to obtain SYSTEM privileges, essentially giving them the keys to the kingdom – full compromise of targeted Windows systems.
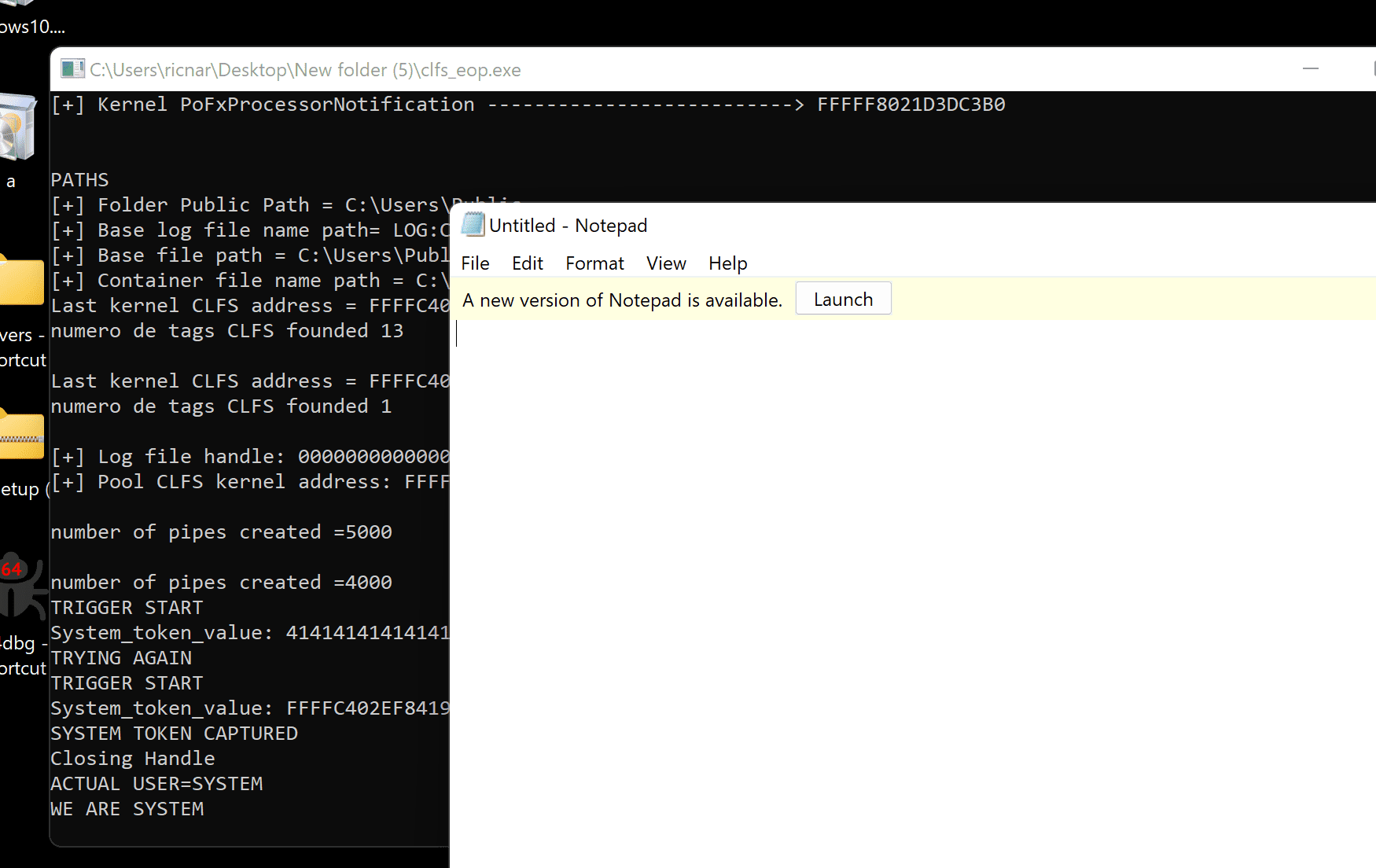
Adding fuel to the fire, Esteban Kazimirow and Ricardo Narvaja, security researchers at IT security consultancy Fortra, have published technical details and proof-of-concept (PoC) exploit code for the CVE-2023-28252 vulnerability that scales to SYSTEM privilege.
This journey to chaos can be deconstructed into several stages. Initially, the kernel addresses required for exploitation are obtained, setting the groundwork for the attack. The path is then prepared to create the .blf files, followed by the crafting of the “trigger blf” file using the CreateLogFile() function.
Further deepening the intrigue, the kernel address of the BASE BLOCK of the trigger blf is obtained, followed by the calling of AddLogContainer with the handle of the trigger blf. The next steps involve preparing the spray blf files and the memory to perform the spray, thereby triggering the bug. A Poc for CVE-2023-28252 is available here.
Therefore, it is strongly recommended that Windows users install Microsoft April Patch Tuesday as soon as possible.




