A high-severity vulnerability in the Microsoft Windows Container Manager Service has been patched by the company, but proof-of-concept exploit code has been released, making it possible for attackers to exploit the flaw.
The vulnerability tracked as CVE-2023-36723 (CVSS score of 7.8), could allow a local authenticated attacker to gain elevated privileges on the system. An attacker who successfully exploited this vulnerability could gain specific limited SYSTEM privileges, which could be used to install programs; view, change, or delete data; or create new accounts.
The vulnerability is caused by a flaw in the Container Manager Service component, which is responsible for managing containers on Windows systems. By executing a specially crafted program, an authenticated attacker could exploit this vulnerability to obtain limited SYSTEM privileges.
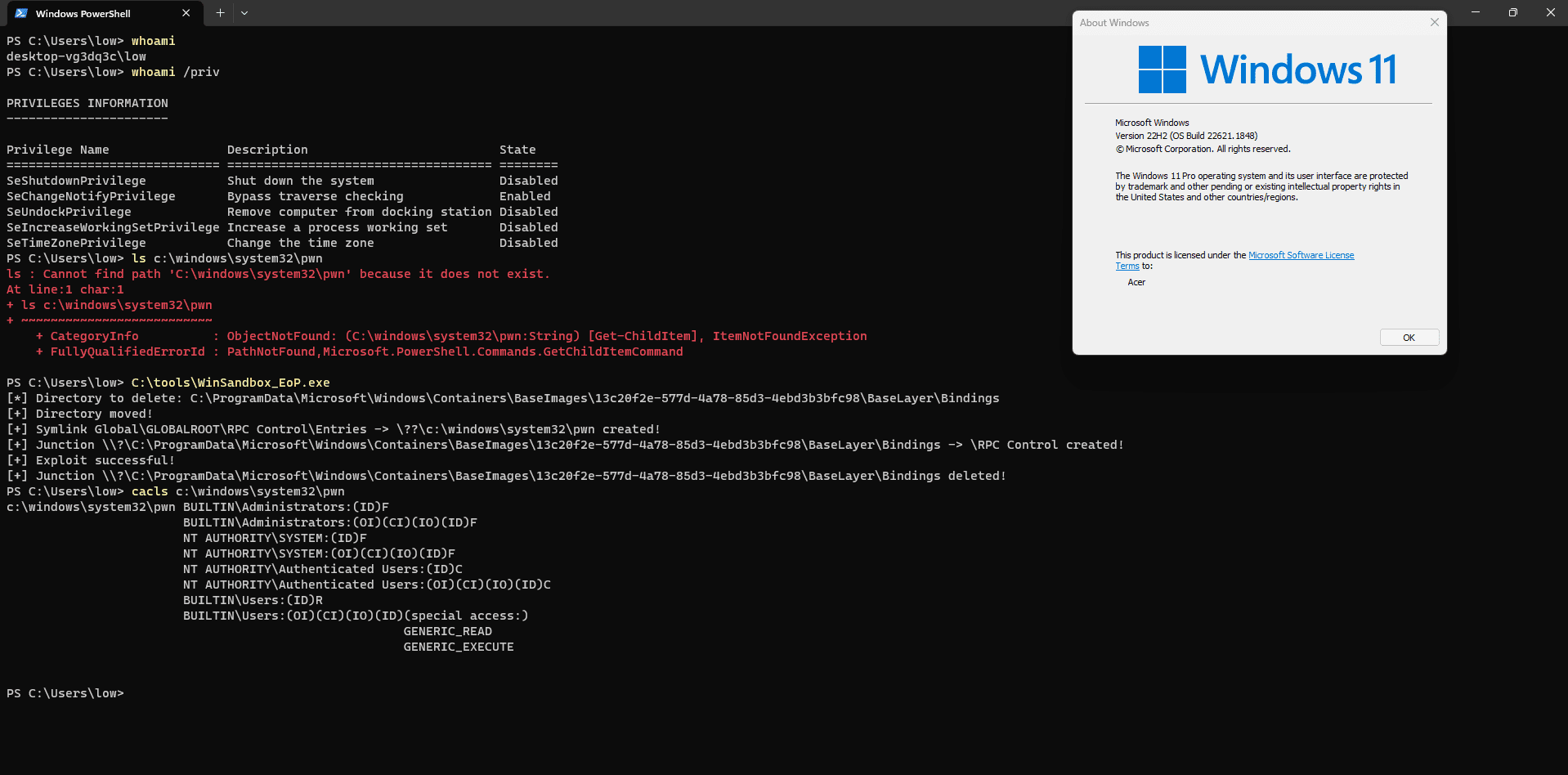
Security researcher Filip Dragović has been credited for finding and reporting this flaw. Today, Dragović released a proof-of-concept (PoC) exploit code for the CVE-2023-36723 vulnerability. The exploit code abuses a bug in the Container Manager Service that allows an attacker to create a directory with permissive DACL’s (discretionary access control lists) inside the c:\windows\system32 directory.
To effectively exploit this chink in the armor, Windows’ Sandbox feature must be activated on the host system. Once operational, this feature spawns a series of directories within the c:\programdata directory. Intriguingly, one of these directories, denoted as C:\ProgramData\Microsoft\Windows\Containers\BaseImages<GUID>\BaseLayer, stands apart. It grants the authenticated users group the power to modify all its child objects.
Should the BaseLayer directory find itself devoid of content or if some directories within it vanish, a subsequent activation of Windows Sandbox will witness the cmimageworker.exe process replenishing those directories/files. What’s unsettling is that this regeneration occurs without any symbolic link verification, and it sets a DACL permitting authenticated users to make modifications.

Masterfully exploiting the CVE-2023-36723 loophole, Dragović’s PoC has the prowess to craft a ‘pwn’ directory equipped with liberal DACLs inside the c:\windows\system32 directory.
Microsoft patched the vulnerability in its October Patch Tuesday update. The company says it is currently not aware of any attacks in the wild related to this issue.
However, the release of the proof-of-concept exploit code means that attackers could now potentially exploit the vulnerability. It is important for organizations to make sure that they have installed the October Patch Tuesday update to protect themselves from this vulnerability.