
PoC exploit has been published for a recently patched Oracle WebLogic Server vulnerability, CVE-2024-20931, leading to arbitrary code execution. The vulnerability has a CVSS score of 7.5 and affects the Oracle WebLogic Server, particularly its T3/IIOP protocol. This revelation comes as part of Oracle’s January 2024 patch update, aiming to fortify its defenses against a new class of cyber threats.

The vulnerability was first reported to Oracle in October 2023, manifesting as a bypass for a previously identified vulnerability (CVE-2023-21839). This previous vulnerability, also within the Oracle WebLogic Server, laid the groundwork for the discovery of CVE-2024-20931.
Glassy of EagleCloud, who found CVE-2024-20931, also provides technical details on the vulnerability, and publishes proof-of-concept (PoC) code.
At the heart of CVE-2024-20931 is the Java Naming and Directory Interface (JNDI) API, a crucial component of the Java platform provided by Oracle. This vulnerability emerges when WebLogic Server implements the OpaqueReference interface for a remote object bound by the T3/IIOP protocol. The crux of the vulnerability lies in the getReferent function of these remote objects. When looked up, the getReferent function calls, under certain conditions, can lead to a JNDI injection by initiating a JNDI query during the remote object query process. This injection poses a significant threat as it can lead to Remote Code Execution (RCE), a highly sought-after exploit by cyber attackers.
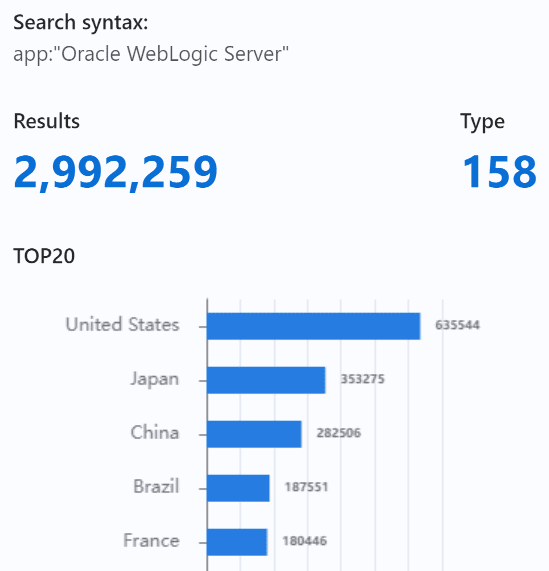
What makes CVE-2024-20931 particularly concerning is the widespread use of Oracle WebLogic Server. A quick search using the ZoomEye search engine reveals nearly 3 million accessible instances of Oracle WebLogic Server across the globe, with a significant concentration in the United States and Japan. The sheer number of instances indicates the potential scale of impact, should the vulnerability be exploited before patches are fully deployed.
Although there is no indication that the vulnerability has been exploited in attacks, Oracle users are advised to update their servers as soon as possible.