Image: Sophos X-Ops
Sophos X-Ops recently released a detailed report on the latest advancements in a malicious toolset known as Poortry, designed to sabotage endpoint detection and response (EDR) software on Windows systems. Originally identified by Mandiant and dubbed “Poortry,” this tool, along with its loader “Stonestop,” has been in active development since 2022, becoming a significant asset for several major ransomware groups, including BlackCat, LockBit, and Medusa.
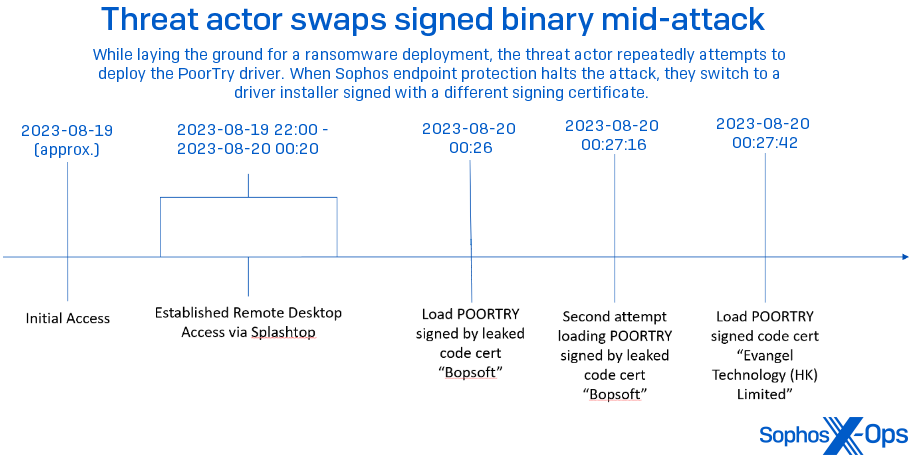
Initially, Poortry functioned as an EDR killer, exploiting gaps in Windows’ driver signature enforcement to disable protective measures. Its creators went to great lengths to ensure the tool’s drivers were signed using legitimate, albeit often compromised, certificates, allowing them to bypass Microsoft’s security mechanisms. Despite Microsoft closing a loophole that had allowed these malicious drivers to be signed, Poortry’s developers adapted quickly, employing new strategies to evade detection.
The latest versions of Poortry are far more advanced, incorporating capabilities that go beyond merely disabling EDR software. Sophos researchers have now observed that Poortry can completely wipe critical components of security software from the disk, effectively transforming it into a dual-purpose tool that not only disables but also destroys EDR systems. This evolution has raised the stakes for organizations, as Poortry now paves the way for ransomware attacks by clearing the path of any obstacles.
Sophos’ report provides an in-depth analysis of how Poortry operates within the Windows ecosystem. At its core, Poortry relies on kernel-mode drivers, which are given extensive access to low-level system functions. These drivers, once loaded into the operating system’s kernel, can unhook and terminate various protection software processes, effectively rendering them useless.
The report highlights three primary methods Poortry’s developers use to abuse code signatures:
- Abuse of Leaked Certificates: Attackers sign their drivers using stolen or compromised certificates from legitimate companies.
- Signature Timestamp Forgery: Through a series of hooks in the operating system, attackers can bypass signature validation checks by forging timestamps.
- Bypassing Microsoft Attestation Signing: The most challenging but most effective method involves submitting malicious drivers directly to Microsoft’s attestation signing process, resulting in a legitimate WHQL certificate.
Since Microsoft and Sophos exposed the WHQL certificate abuse in 2022, Poortry’s developers have shifted to using forged timestamps and leaked certificates, ensuring their tool remains effective against EDR systems.
The most concerning development in Poortry’s evolution is its new ability to wipe critical EDR components off disk. This feature was first observed in a July 2024 incident involving an attempted deployment of RansomHub ransomware. During the attack, Sophos CryptoGuard blocked the ransomware, but a post-incident analysis revealed that Poortry had attempted to delete vital security software files before the final attack phase.
Sophos researchers identified that Poortry now operates in two modes when targeting files for deletion:
- By Type: Poortry identifies and deletes all files of a specific type within the target directory.
- By Name: Poortry targets specific files by name, allowing for precise elimination of critical EDR components.
Poortry’s evolution from an EDR killer to an EDR wiper demonstrates the persistence and adaptability of cybercriminals. The tool has become a Swiss Army Knife for attackers, capable of bypassing security measures, disabling protections, and now, outright destroying security software. As Sophos X-Ops continues to monitor the development of Poortry, it is clear that organizations must remain vigilant, as the tool’s creators are relentless in their efforts to refine and expand its capabilities.
Related Posts:
- Leaked LockBit Tools: Novice Hackers Target Vulnerabilities
- New VMware Findings: Kernel Drivers’ Vulnerabilities Risk Total Device Takeover
- Unpatched Vulnerabilities: Ransomware’s Favorite Entry Point