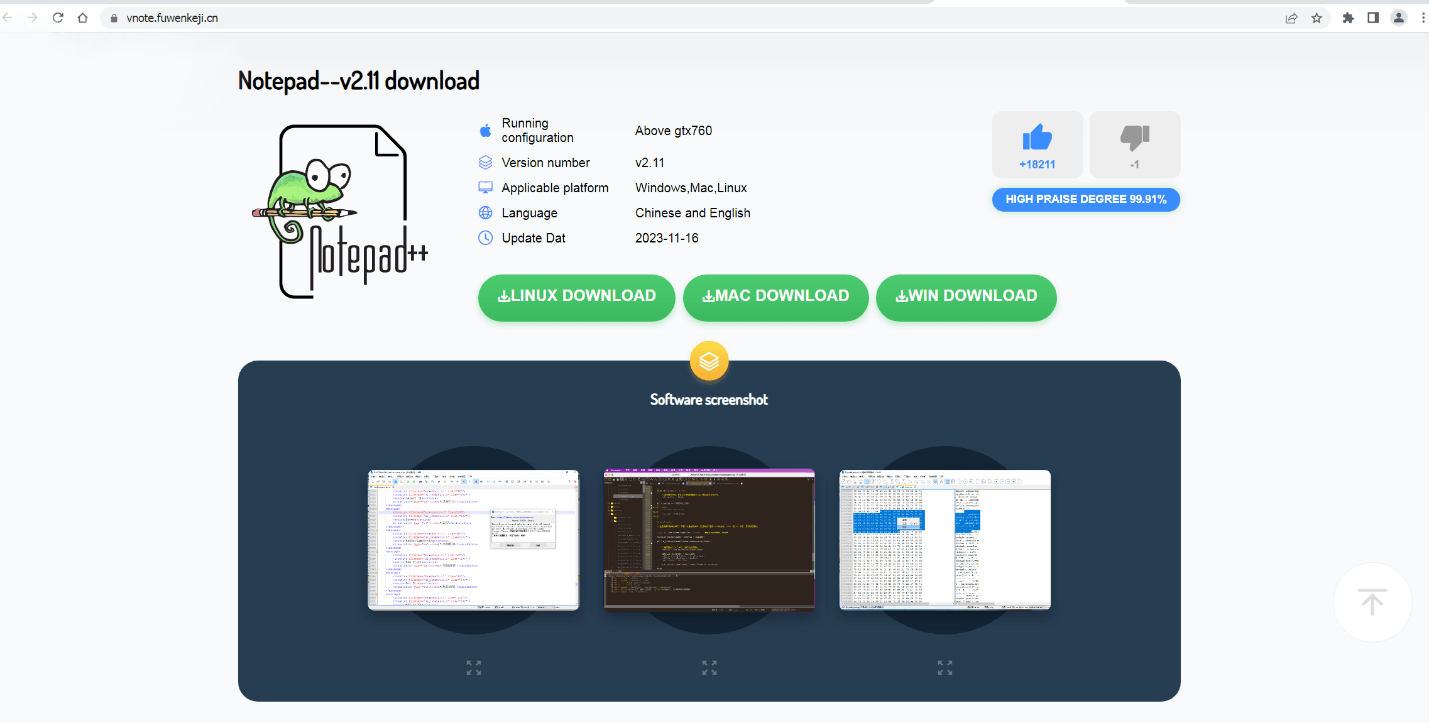
Page with fake NotePad++
Popular text editing software used by millions across China has become the latest target in a sophisticated cyberattack, security researchers at Kaspersky Labs have discovered. Threat actors are spreading modified versions of well-known editors like Notepad++ and VNote, designed to infect users’ computers with dangerous malware.
The Scheme
The attackers are employing a tactic known as “malvertising” and search engine manipulation. They place fake ads and manipulate search results so that when users search for these text editors, they are directed to malicious websites disguised as official download pages.
“Using typosquatting and other techniques, the attackers tried to make their resources look as similar as possible to the official websites of popular programs. This time, a similar threat has affected users of one of the most popular search engines in the Chinese internet.” – Kaspersky Labs researcher.

Kaspersky Labs’ researchers have pinpointed two instances where advertisements and search results led users to download trojanized versions of beloved text editors. In one case, a search for Notepad++ directed users to a site that, while purporting to offer Notepad++ downloads, actually distributed a malicious variant named Notepad–. The site cunningly offered installers for multiple operating systems, but only the links for macOS and Linux were laced with malware, leaving the Windows version untainted.
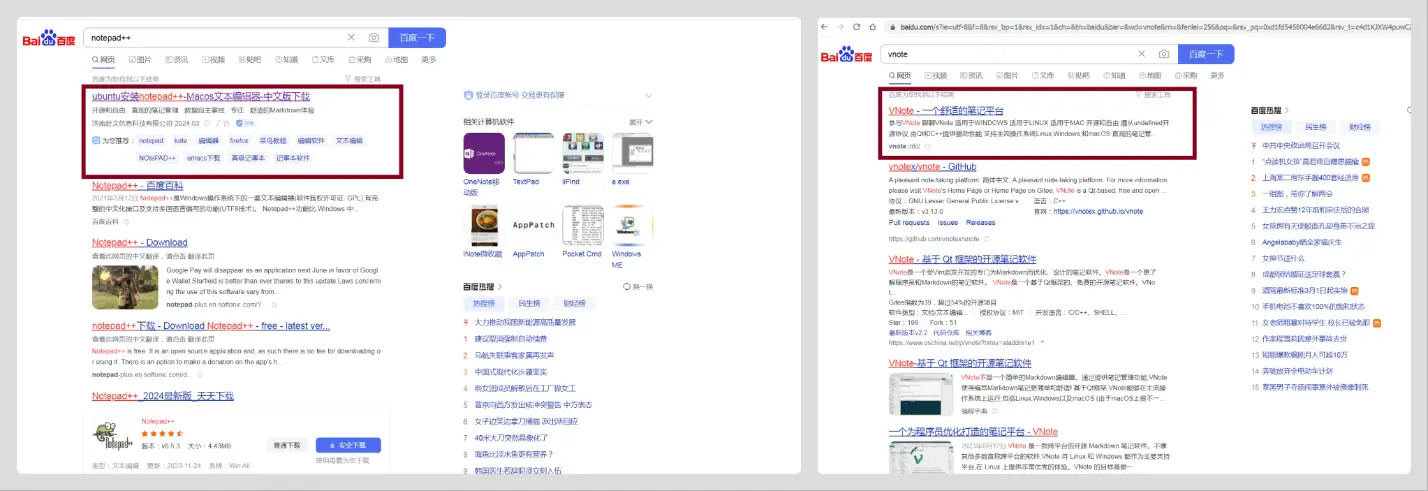
The source of these malicious packages was traced back to a suspicious server, hinting at the sophisticated infrastructure supporting this malvertising campaign. A similar fate befell users searching for VNote, another text editor, suggesting a shared modus operandi between the two cases.
Infected Software: What Happens?
Upon examining the tainted versions of Notepad– for Linux and macOS, Kaspersky Labs uncovered alarming modifications. The malware, masquerading as legitimate software, was crafted to initiate a class named Uplocal before the application’s launch, which in turn downloads and executes a file from a malicious server. This server harbored not only the updater but also a file named DPysMac64, identified as a backdoor akin to the notorious Geacon – a CobaltStrike agent clone.
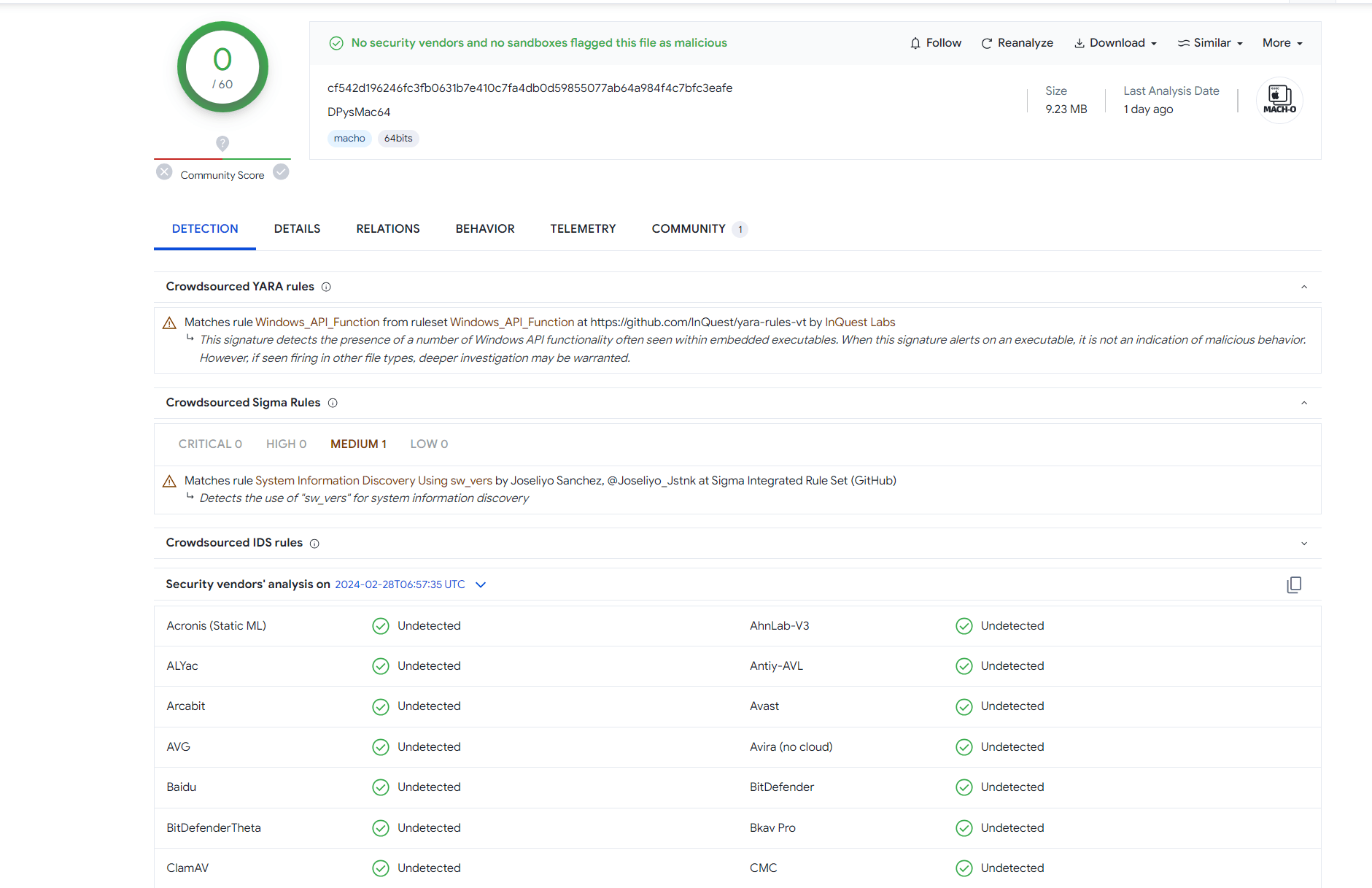
This backdoor, designed for both Linux and macOS, boasts the ability to communicate with its command and control server via HTTPS, hinting at a sophisticated network of cyber espionage. Interestingly, the attackers named the project which implements the functionality of executing remote commands spacex.
Who’s Behind It?
While the attackers’ identities remain unknown, Kaspersky Labs’ investigation suggests a well-organized and highly targeted campaign.
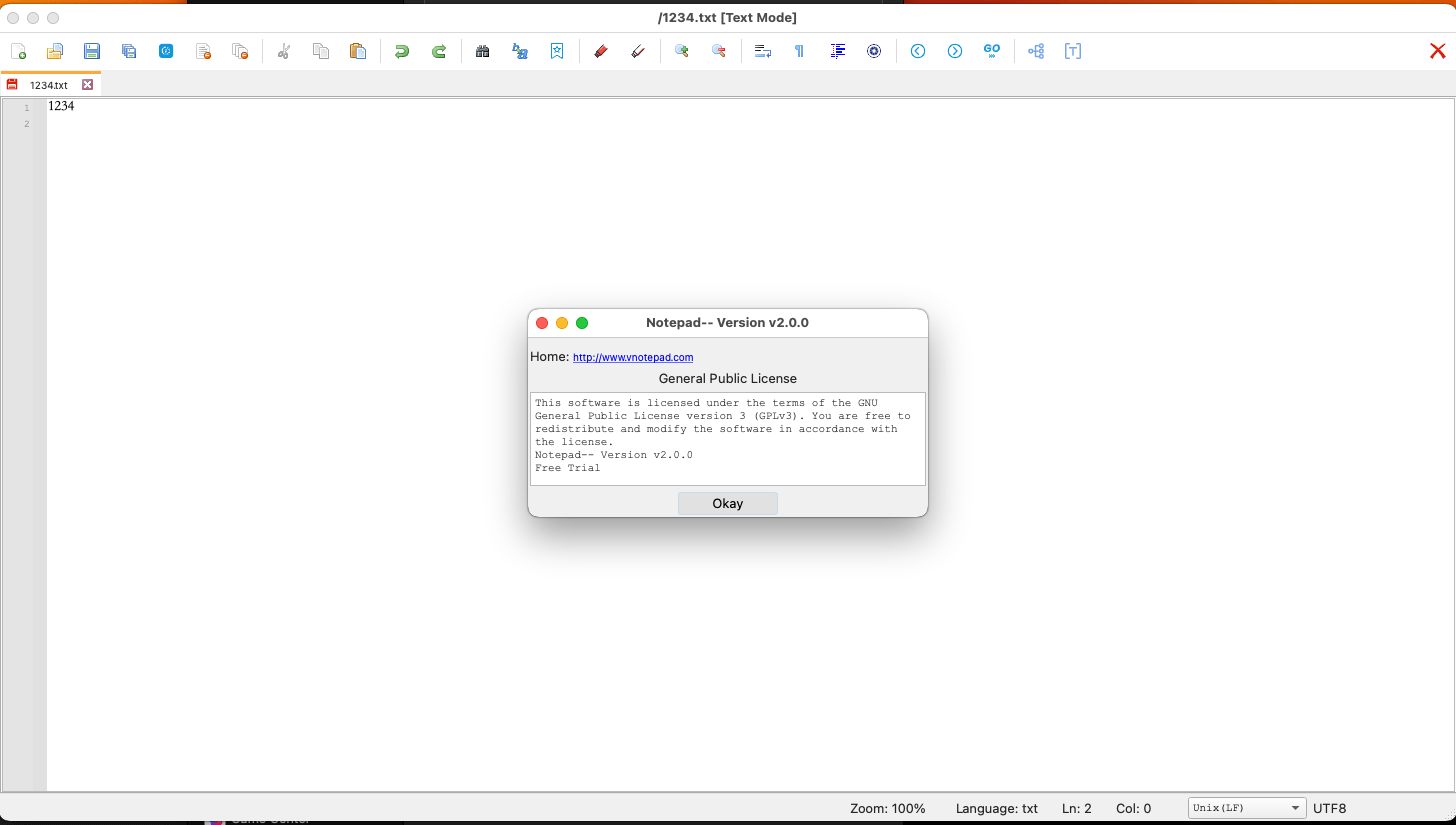
Kaspersky Labs’ sleuthing revealed an intricate web of connections between the entities distributing the infected applications. A curious discovery linked a suspicious About window in the modified Notepad– to another clone site, further entwining the narratives of the malicious VNote and Notepad– variants. This interconnectedness suggests a broad, coordinated effort to deploy a secondary infection stage through these tampered applications.
Protect Yourself
- Stick to trusted sources: Always download software from official websites or reputable repositories.
- Check for inconsistencies: Be vigilant and look for typos, odd URLs, and inconsistencies on download sites.
- Keep your security software up-to-date: A quality antivirus and firewall can help detect and block malware.
The investigation continues…
Kaspersky Labs researchers are continuing their work to uncover the full extent of this attack. Stay tuned for updates and further guidance on how to protect yourself and your data.