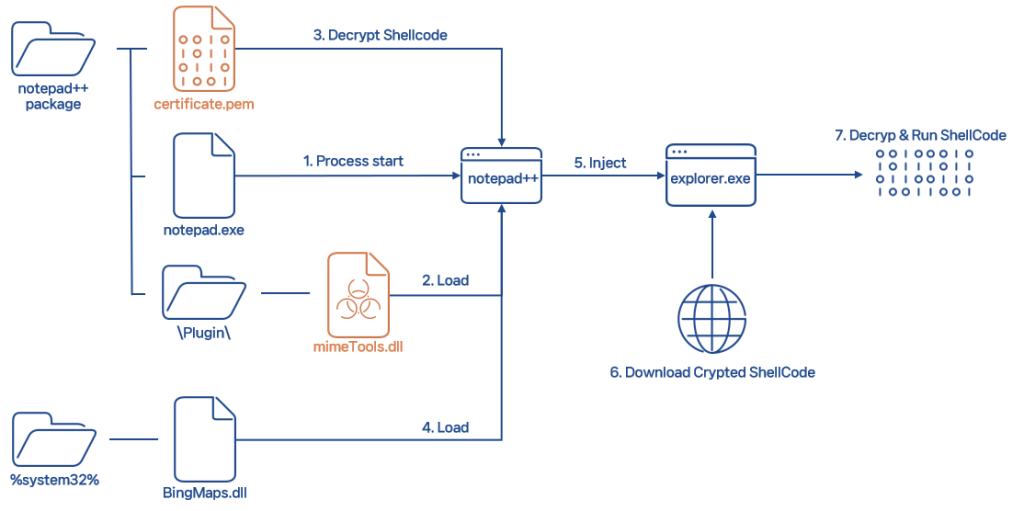
Malware flow diagram | Image: ASEC
A sophisticated malware campaign targeting the widely-used Notepad++ text editor has been uncovered by security researchers at AhnLab Security Emergency Response Center (ASEC). Dubbed “WikiLoader,” this attack demonstrates the alarming ingenuity of modern threat actors and the risks associated with even seemingly trustworthy software.
The Art of Disguise: How WikiLoader Exploits Trust
At the heart of this attack lies a technique known as DLL hijacking. The attackers surreptitiously modified a default Notepad++ plugin, “mimeTools.dll,” to execute malicious code whenever the text editor is launched. Since this plugin ships with every Notepad++ installation, users unwittingly trigger the infection as soon as they use the software.

Within the corrupted plugin, the attackers carefully concealed their payload. A file disguised as a harmless certificate, “certificate.pem,” masks encrypted shellcode – the initial stage of the attack. The complexity increases as the malware overwrites code within another plugin, “BingMaps.dll” and injects a thread into the core “explorer.exe” Windows process. This ensures persistence and makes the attack harder to detect.
Evasion, Deception, and Malicious Intent
The WikiLoader campaign showcases multiple tactics designed to thwart antivirus software and security researchers:
- Hiding in Plain Sight: The use of indirect syscalls (system calls) helps the malware avoid being flagged by standard monitoring tools.
- Playing Cat-and-Mouse: The malware actively scans for processes commonly used for analysis. If any are detected, it immediately shuts down to avoid deeper investigation.
The threat actors behind WikiLoader have a clear objective: establish a foothold on the victim’s computer. They do this by having the compromised Notepad++ connect with a command-and-control (C2) server cleverly masquerading as a WordPress login page. It’s from here that the final malware payload is delivered, though its exact capabilities are not yet fully revealed.
What We Do Know: WikiLoader’s Reconnaissance Mission
Even without the final payload, WikiLoader poses a significant risk by meticulously gathering information about the infected system. This includes:
- Computer name & Username
- Administrator access level
- Language and system settings
Protecting Yourself: Critical Steps for Notepad++ Users and Beyond
The discovery of the WikiLoader malware within Notepad++ underscores the vulnerabilities inherent in widely-used software applications. The ease with which the malware integrates into everyday tools highlights the critical need for vigilance, even when dealing with software that is frequently trusted and used by millions.
- Source Matters: Always download Notepad++, and any other software, exclusively from official and trusted sources. Pirated software poses significant risks.
- Patch Immediately: If you are a Notepad++ user, ensure you have the latest version to mitigate this exploit.
- Vigilance is Key: Be extremely cautious about unexpected behavior on your system, even from known software. Stay informed about current cybersecurity threats.
- Broader Implications: WikiLoader is a harsh reminder that no software is inherently immune. Robust security practices, skepticism regarding unexpected links, and strong password management are essential in today’s digital landscape.
