Image: CloudSEK
A recent investigation by CloudSEK has exposed PrintSteal, a vast cybercriminal operation engaged in the fraudulent generation and distribution of counterfeit Know Your Customer (KYC) documents in India. Operating under a network of impersonating websites, the scheme has exploited Common Service Centre (CSC) platforms to produce and distribute fake Aadhaar cards, birth certificates, PAN cards, and other identity documents.
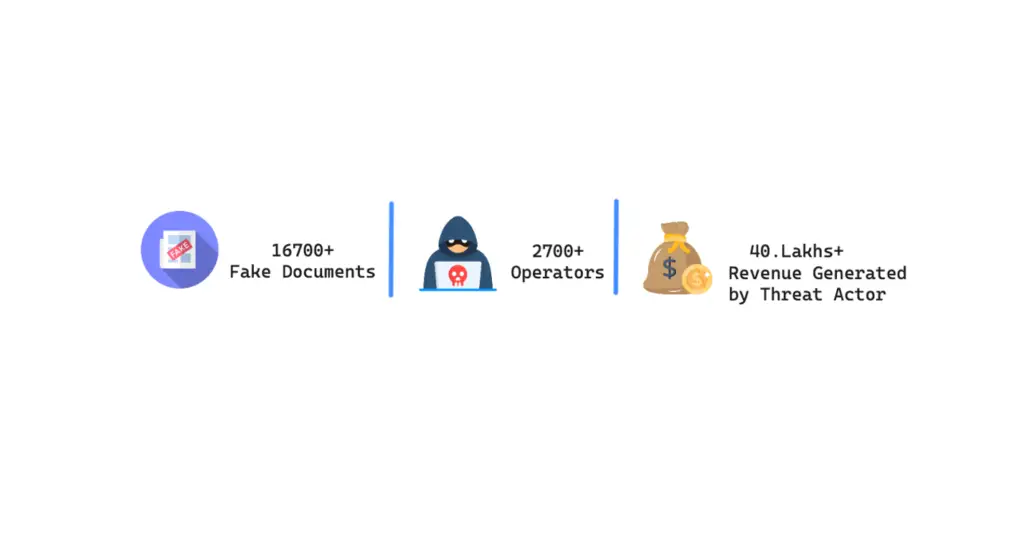
According to the report, “over 167,391 fake documents have been generated on this platform, including over 156,000 fake birth certificates, showcasing the operation’s vast scale and capabilities.”
CloudSEK’s analysis focused on crrsg.site, one of over 1,800 identified domains involved in the operation, with at least 600 active domains currently in use. These websites “impersonate csc.gov.in and crsorgi.gov.in to enhance credibility“, luring unsuspecting users into obtaining fraudulent identity documents. The operation has been active since at least 2021, leveraging a network of 2,727 registered operators—including mobile shops and cyber cafés—to facilitate document production and distribution.
The fraudsters have built a highly organized and structured system, complete with:
- A centralized web platform for document generation
- Illicit API integrations to access sensitive personal data
- Encrypted communication channels via Telegram
- A streamlined payment system that enables transactions through virtual wallets
Financial investigations indicate that the crrsg.site platform alone has generated over ₹40 lakh ($48,000) in revenue, with the total financial impact likely much higher across the entire fraudulent network.
The operation follows a systematic process to create and distribute fraudulent documents:
- Website Setup: Fraudulent KYC portals are created using pre-made templates from third-party vendors such as ahkwebsolutions.com and hardscripts.com.
- Affiliate Recruitment: Local businesses, including internet cafés and mobile shops, are enlisted as affiliates, who then promote and distribute fake documents.
- Document Generation: Operators input customer details, which are processed using PHP-based scripts and MySQL databases to produce official-looking PDF documents.
- Deceptive QR Code Verification: Fraudulent QR codes are embedded in the documents, linking users to fake verification pages that mimic official government sites.
- Payments and Revenue Model: The service operates on a prepaid wallet system, where affiliates fund accounts and generate documents at a cost of ₹20-35 per file, marking up the price for customers.
CloudSEK warns that this “sophisticated deception makes it extremely difficult to distinguish authentic documents from fraudulent ones, even with basic verification attempts.”
The fraudsters demonstrate advanced operational security (OPSEC) to evade detection:
- Use of Telegram channels for secure communications and affiliate coordination
- Rapid domain shifting to circumvent law enforcement crackdowns
- Warnings and training for affiliates on avoiding detection
Additionally, CloudSEK’s report identifies a key individual behind crrsg.site: Manish Kumar, operating from Bihar, India. The report links Kumar to multiple fraudulent sites, providing key attribution details, including:
- Phone number: +91 7070635763
- Telegram handle: @boss1432m
- UPI ID: paytm.s15mpdp@pty
- IP address: 157.90.176.32
The large-scale generation of fraudulent KYC documents has severe implications:
- Financial Crimes: Fake identity documents facilitate fraud, loan scams, and money laundering.
- Erosion of Trust: The impersonation of CSC and government services damages public confidence in legitimate e-Governance initiatives.
- Regulatory Violations: The scheme breaches Indian data protection laws, Aadhaar regulations, and IT Act provisions.
- National Security Risks: Fraudulent identities can be used for unlawful access to government services and illicit financial activities.
The PrintSteal operation underscores the growing threat posed by cybercriminals exploiting public trust in government services. With over 1,800 domains identified and hundreds still active, the scale and adaptability of this scheme present a serious challenge to law enforcement and cybersecurity professionals.
Related Posts:
- Security Alert: Hackers Can Access Google Accounts Without Passwords
- Dark Web Identity Farming Operation Exposed: A Sophisticated KYC Fraud
- Security Alert: Hackers Can Access Google Accounts Without Passwords
- Threat Actors Exploit Fake Brand Collaborations to Target YouTube Channels
- Hacker forged Windows 11 upgrade website to trick users to download the virus