
The world of Pay-Per-Install (PPI) malware rarely stands still, and PrivateLoader, a notorious player in this arena, has pulled a new set of tricks out of its sleeve. This widespread malware downloader has recently undergone significant updates, introducing a new string encryption algorithm and an alternative communication protocol. Moreover, it has adopted a more self-reliant approach by downloading a copy of itself along with a plethora of malicious payloads.
The recent iterations of PrivateLoader have been cloaked with the commercial packer VMProtect, adding layers of complexity to the task of analysis and reverse-engineering. This strategic move not only shields its nefarious code from prying eyes but also challenges the cybersecurity community’s ability to dissect and neutralize it effectively.
Bitsight‘s telemetry data revealed a summary of PrivateLoader’s reach, revealing a sprawling network of infected systems that spans the globe, with a pronounced presence in continents bolstered by emerging economies such as Africa, Asia, and South America. This geographic distribution hints at the malware’s method of dissemination, primarily through SEO-optimized websites offering cracked software, a tactic that finds fertile ground in regions where software piracy is more prevalent.

Since July 2022, Bitsight has been closely monitoring PrivateLoader, tracking its association with the Russian Pay-Per-Install service InstallsKey. This service, instrumental in the proliferation of the malware, operates under a model that compensates for installations, thereby incentivizing the spread of the downloader.
PrivateLoader’s repertoire of malicious activities is extensive, predominantly involving the download and execution of a wide array of malware families, particularly stealers and loaders. Over the past year, it has unleashed more than 2,300 payloads, drawing largely from VK.com, a popular Russian social media platform.
The Shape-Shifting Downloader: New Developments
- A Curious Downgrade: In a surprising twist, the authors of PrivateLoader have opted to simplify their string encryption scheme, abandoning a more complex method in favor of a basic XOR-based approach. While this might make certain communication data initially less opaque, it can also be a calculated move designed to throw off some traditional detection models.
- Redundancy for Resilience: PrivateLoader has established a secondary communication protocol alongside its primary method. This dual-channel strategy is likely meant to protect its operations; if one communication pathway is disrupted, the other may remain active.
- Self-Propagation Strategy: The malware now downloads a copy of itself in addition to its other malicious deliveries. This disturbing tactic aims to increase the botnet’s footprint, ensuring persistence and making it even more difficult to fully eradicate.
- Hidden Behind Commercial Protection: The deployment of the VMProtect packer poses a significant obstacle to analysis. VMProtect is known for its advanced obfuscation and anti-debugging techniques, creating a maze for security researchers to navigate.
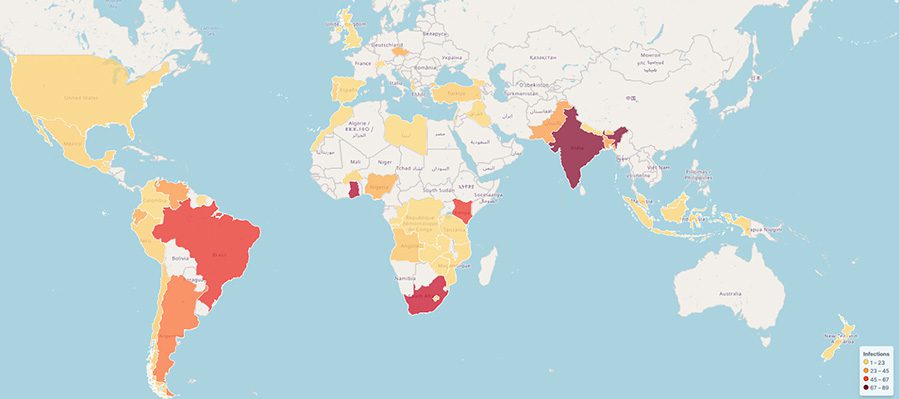
With over 1 million computers compromised in 2023 alone and an infection rate that suggests an even larger scale of impact in 2024, the urgency to counter this threat is palpable.
Bitsight’s contribution to this effort includes the development of a YARA rule designed to detect new versions of PrivateLoader, alongside a static config extractor that leverages Ghidra scripting. These tools enhance the ability to identify and analyze PrivateLoader infections.