PrivKit: simple beacon object file that detects privilege escalation vulnerabilities
PrivKit
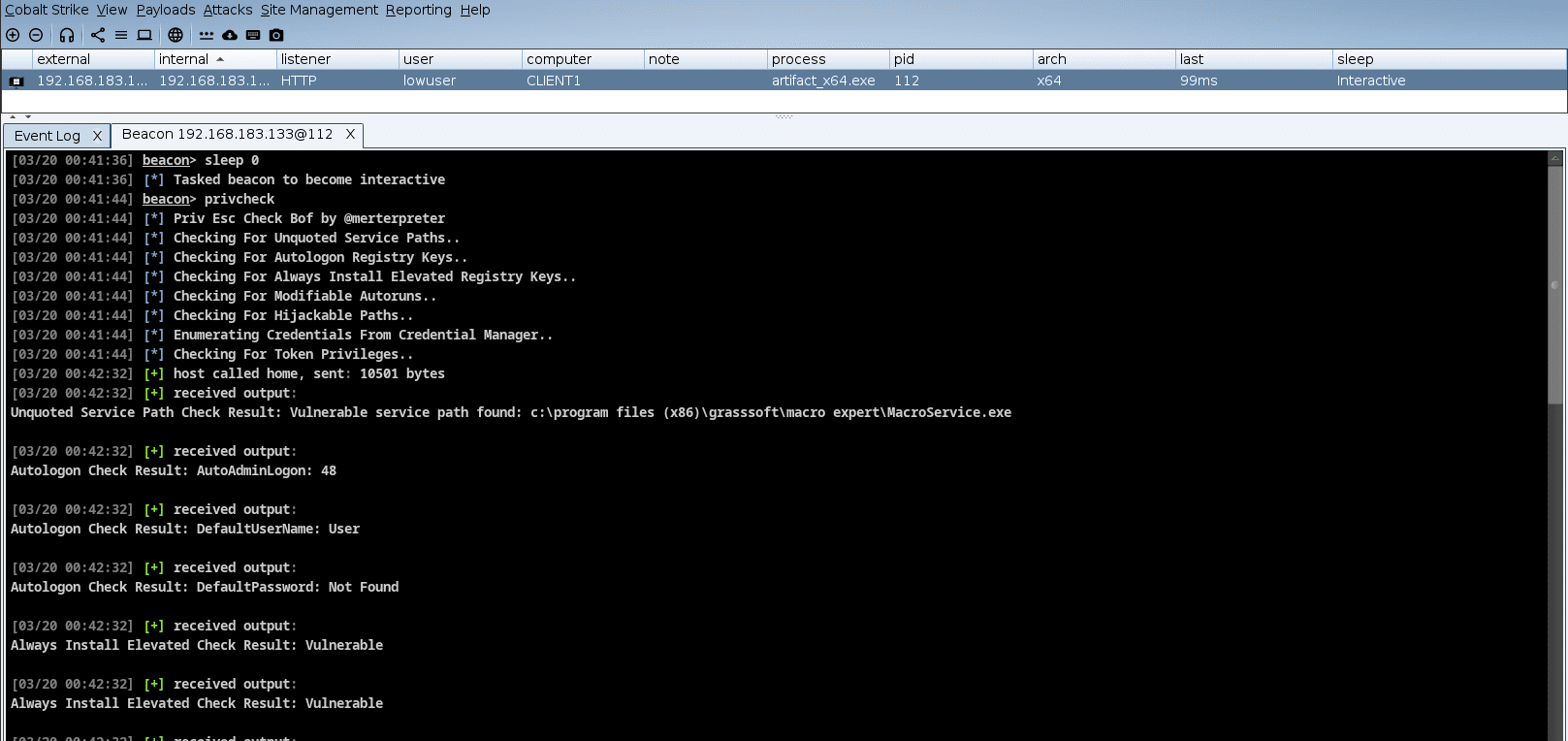
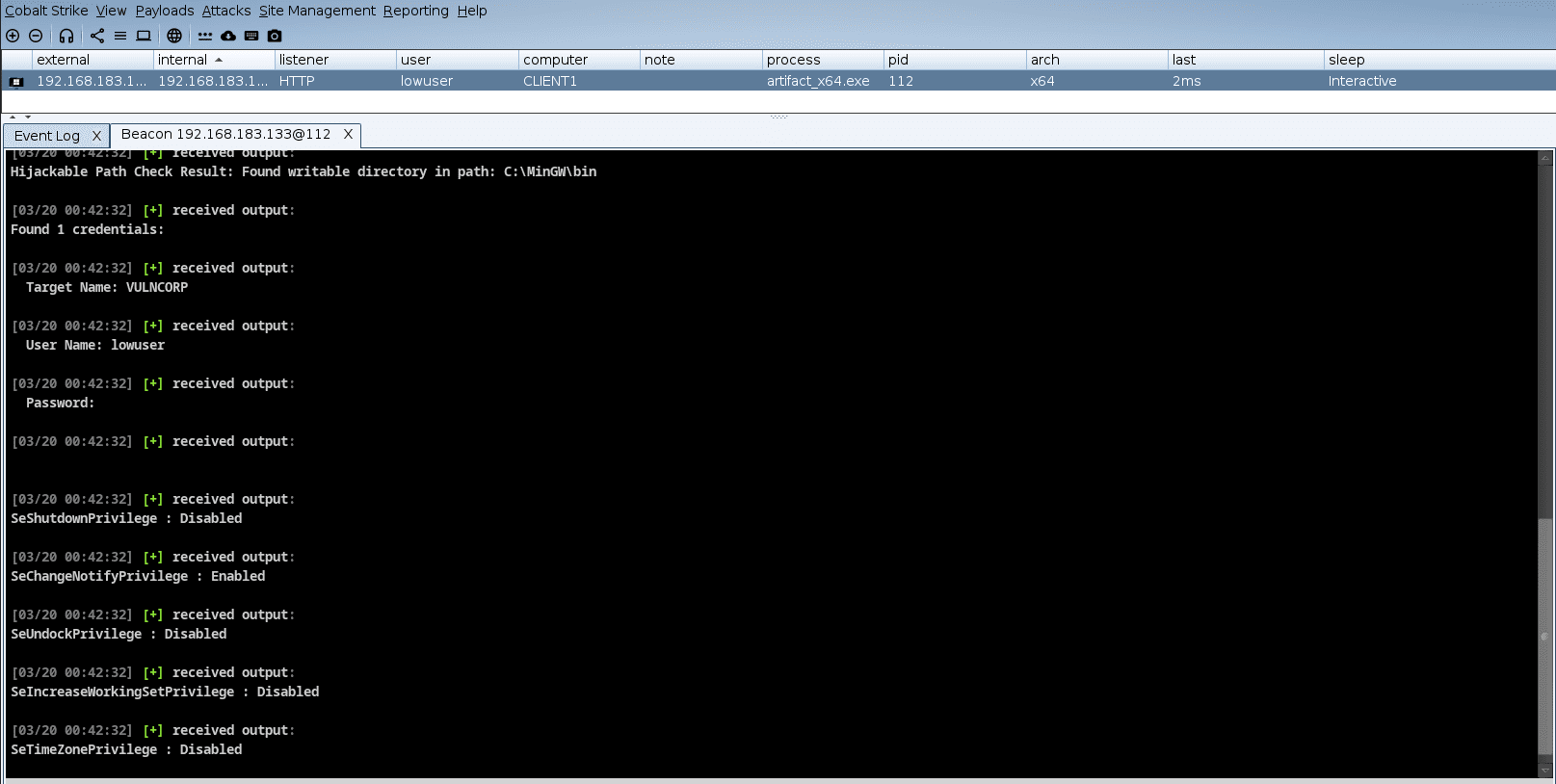
PrivKit is a simple beacon object file that detects privilege escalation vulnerabilities caused by misconfigurations on Windows OS.
PrivKit detects the following misconfigurations
- Checks for Unquoted Service Paths
- Checks for Autologon Registry Keys
- Checks for Always Install Elevated Registry Keys
- Checks for Modifiable Autoruns
- Checks for Hijackable Paths
- Enumerates Credentials From Credential Manager
- Looks for current Token Privileges
Download
git clone https://github.com/mertdas/PrivKit.git
Use
Simply load the cna file and type “privcheck”
If you want to compile by yourself you can use:
make all
or
x86_64-w64-mingw32-gcc -c cfile.c -o ofile.o
If you want to look for just one misconf you can use an object file with “inline-execute” for example
inline-execute /path/tokenprivileges.o

Copyright (C) 2023 mertdas
Source: https://github.com/mertdas/





