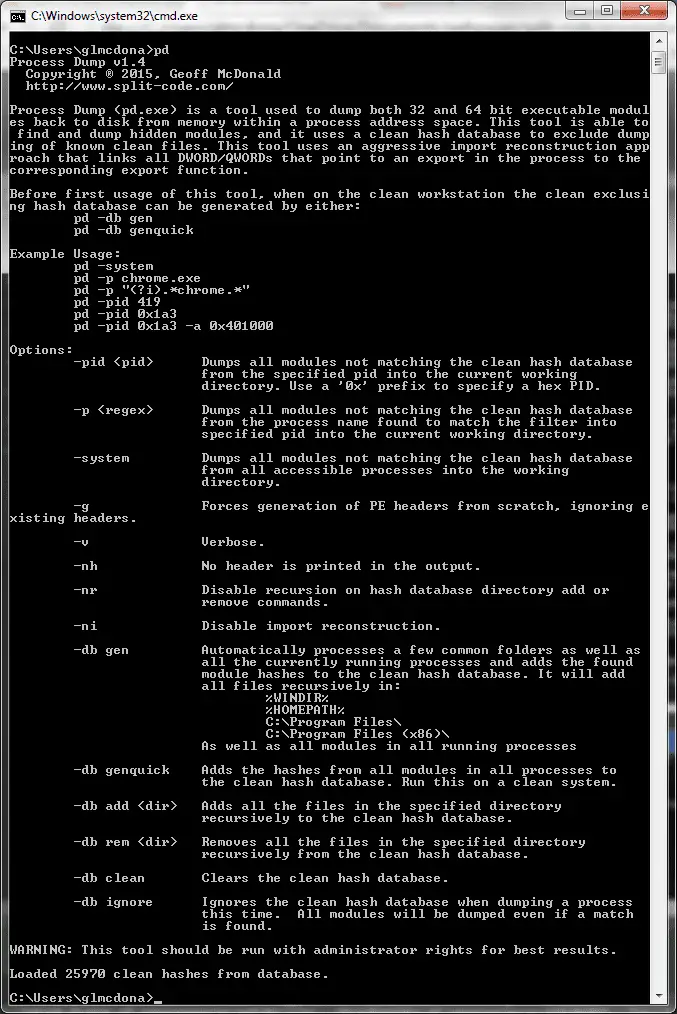
Process Dump
Process Dump is a Windows reverse-engineering command-line tool to dump malware memory components back to disk for analysis. Often malware files are packed and obfuscated before they are executed in order to avoid AV scanners, however, when these files are executed they will often unpack or inject a clean version of the malware code in memory. A common task for malware researchers when analyzing malware is to dump this unpacked code back from memory to disk for scanning with AV products or for analysis with static analysis tools such as IDA.
Process Dump works for Windows 32 and 64 bit operating systems and can dump memory components from specific processes or from all processes currently running. Process Dump supports the creation and use of a clean-hash database so that dumping of all the clean files such as kernel32.dll can be skipped. Its main features include:
- Dumps code from a specific process or all processes.
- Finds and dumps hidden modules that are not properly loaded in processes.
- Finds and dumps loose code chunks even if they aren’t associated with a PE file. It builds a PE header and import table for the chunks.
- Reconstructs imports using an aggressive approach.
- Can run in close dump monitor mode (‘-closemon’), where processes will be paused and dumped just before they terminate.
- Multi-threaded, so when you are dumping all running processes it will go pretty quickly.
- Can generate a clean hash database. Generate this before a machine is infected with malware so Process Dump will only dump the new malicious malware components.
Changelog
v2.1.1 updates:
- Statically link libraries, which removes the pre-install dependency on Microsoft Visual C++ Redistributable per suggestion from Blaine for easier integration to Mandiant FLARE-VM.
v2.1 updates:
- Fixed a bug where the last section in some cases would instead be filled with zeros. Thanks to megastupidmonkey for reporting this issue.
- Fixed a bug where 64-bit base addresses would be truncated to a 32-bit address. It now properly keeps the full 64-bit module base address. Thanks to megastupidmonkey for reporting this issue.
- Addressed an issue where the processes dump close monitor would crash csrss.exe.
- Stopped Process Dump from hooking it’s own process in close monitor mode.
Install & Use
Copyright (c) 2015 Geoff McDonald