ProtectMyTooling: Multi-Packer wrapper letting us daisy-chain various packers, obfuscators
ProtectMyTooling
A script that wraps around a multitude of packers, protectors, obfuscators, shellcode loaders, encoders, and generators to produce complex protected Red Team implants. Your perfect companion in Malware Development CI/CD pipeline, helping watermark your artifacts, collect IOCs, backdoor, and more.

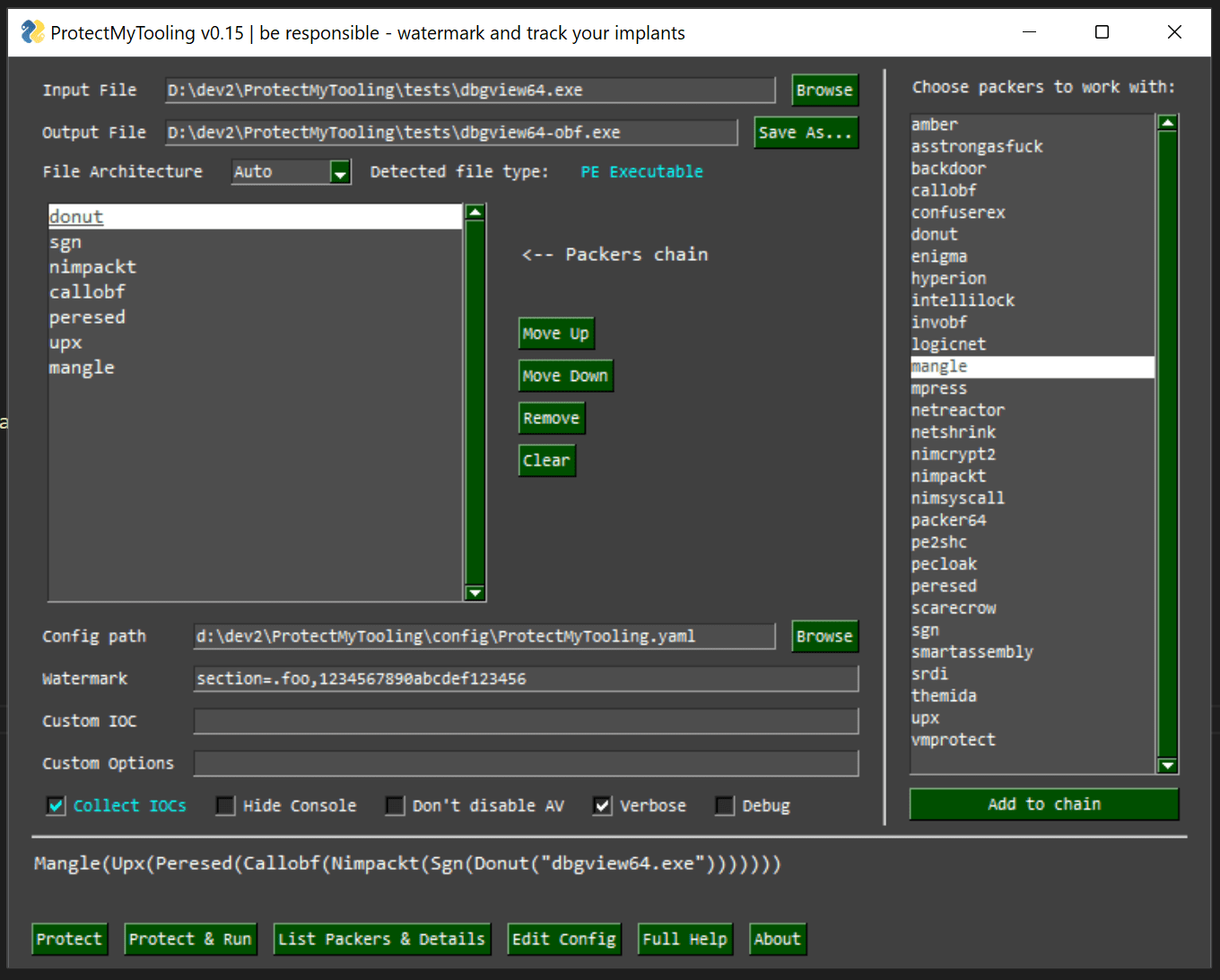
With ProtectMyTooling you can quickly obfuscate your binaries without having to worry about clicking through all the Dialogs, interfaces, and menus, creating projects to obfuscate a single binary, clicking through all the options available, and wasting time about all that nonsense. It takes you straight to the point – to obfuscate your tool.
The aim is to offer the most convenient interface possible and allow to leverage of a daisy-chain of multiple packers combined on a single binary.
That’s right – we can launch ProtectMyTooling with several packers at once:
C:\> py ProtectMyTooling.py hyperion,upx mimikatz.exe mimikatz-obf.exe
The above example will firstly pass mimikatz.exe to the Hyperion for obfuscation, and then the result will be provided to UPX for compression. Resulting with UPX(Hyperion(file))
Features
- Supports multiple different PE Packers, .NET Obfuscators, Shellcode Loaders/Builders
- Allows daisy-chaining packers where output from a packer is passed to the consecutive one: callobf,hyperion,upx will produce artifact UPX(Hyperion(CallObf(file)))
- Collects IOCs at every obfuscation step so that auditing & Blue Team requests can be satisfied
- Offers functionality to inject custom Watermarks to resulting PE artifacts – in DOS Stub, Checksum, as a standalone PE Section, to file’s Overlay
- Comes up with a handy Cobalt Strike aggressor script bringing protected-upload and protected-execute-assembly commands
- Straightforward command line usage