PSRecon: gathers data from a remote Windows host using PowerShel
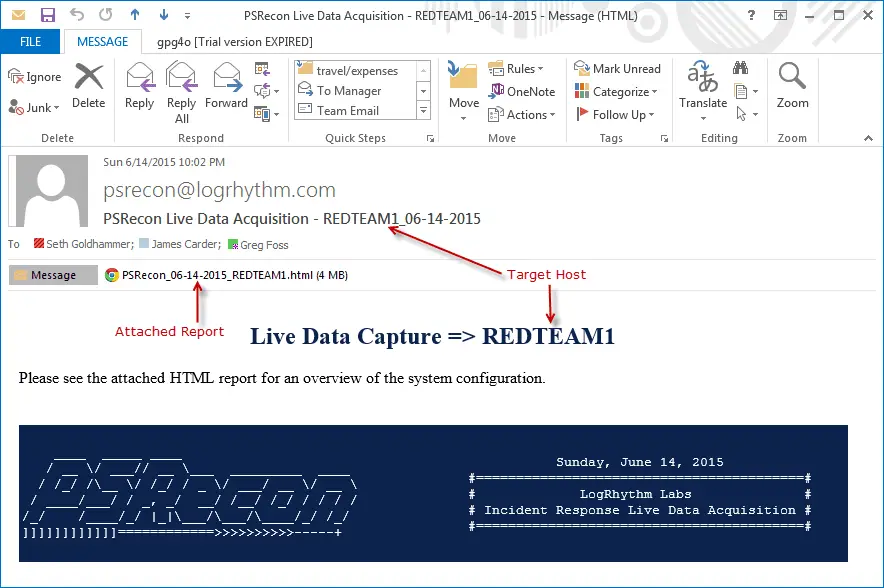
PSRecon gathers data from a remote Windows host using PowerShell (v2 or later), organizes the data into folders, hashes all extracted data, hashes PowerShell and various system properties, and sends the data off to the security team. The data can be pushed to a share, sent over email, or retained locally.
One nice part about the report is that everything is self-contained, making it easy to share as there is no reliance on a centralized server. Even the images are encoded directly into the report’s HTML.
This script also includes endpoint lockdown functionality. This can be useful when working through a malware outbreak incident, especially when there is the risk that the malware will spread to a share or other critical systems within the enterprise. Sometimes the quickest and most effective way to stop the spread of malware is to simply knock the host offline until IT/Security can respond, following the extraction of forensic data. Alternatively, to quarantining the host, PSRecon allows you to disable an active directory account as well.
Ideally, this script should be integrated with the organization’s Active Defense frameworks to automate rapid forensic data acquisition and lock down the endpoint.
Download
git clone https://github.com/gfoss/PSRecon.git
Usage
Run PSRecon on the local host:
Run PSRecon on the remote host:
What if PSRemoting and Unrestricted Execution are disabled?
[Parameter Breakdown]
Example
1) Basic Incident Response
Run this script directly to extract live forensic data from a remote host over the network and send the evidence report out via email to the Incident Response Team and/or push the evidence in its entirety to a remote share for later review. You could alternatively, run this script on the host directly, by way of a USB and store the results on the external drive.
2) SIEM Integration for Incident Response Automation
Configure as a LogRhythm SmartResponse(TM) to automatically gather live Incident Response data and push HTML reports to the IR team. This can be configured to fire based on alerts observed within the SIEM or launched at-will in SIEM versions 7.0 and higher. When associating with malware events or similar activity where containment is desired, you can leverage the lockdown feature to gather forensic data before effectively knocking the host offline.
3) Remote Data Extraction and Endpoint Quarantine
Say that you have received alerts that a system recently became infected with a variant of Cryptolocker, automated cleanup failed, and you are worried about this spreading to shares. Quickly capture data from the remote host to gather data and better understand the infection and then quarantine the host by disabling NICs, logging the user out, and locking their desktop.
[Notes]
PSRecon does modify the target filesystem, so in a sense, this is not as forensically sound as capturing an image using something like EnCase. Please be aware of this before using the tool in a real IR scenario… However, PSRecon does create it’s own application logs and hashes all data obtained in order to track and verify it’s own activity. This is helpful in reconstructing the timeline and verification of access and modifications to the target system, however, this may not hold up in court. Please be aware of this.
Speaking of Logging, PSRecon also logs attempted attacks against itself… So, take an example scenario where someone tries to hijack another employee’s browser by inserting JavaScript into a user-controllable field of PSRecon that is embedded within a security solution. To do this they would inject an XSS attack within a user-controllable field that is reflected on the HTML report. These attacks are detected and logged, allowing for additional actions to be taken. Of course, there are tons of ways around this, it’s just a small added precaution for when the script is integrated with security infrastructure.
Copyright (c) 2015, LogRhythm All rights reserved.
Source: https://github.com/gfoss/